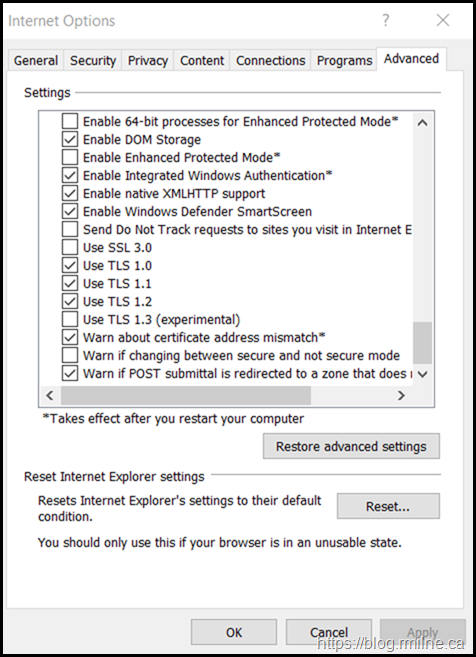
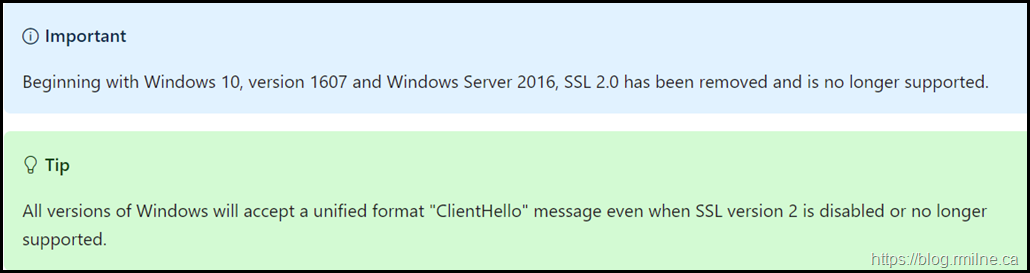
Transport Layer Security (TLS) and Secure Sockets Layer (SSL) are protocols that provide secure communications. Today several versions of these protocols exist, and not all of them are considered secure by Microsoft or other security companies.
Schannel is a Security Support Provider (SSP) that implements the SSL, TLS and Datagram Transport Layer Security (DTLS) Internet standard authentication protocols in Windows. The Security Support Provider Interface (SSPI) is an API used by Windows systems to perform security-related functions including authentication. The SSPI functions as a common interface to several Security Support Providers (SSPs), including the Schannel SSP.
A cipher suite is a set of cryptographic algorithms. The Schannel SSP implementation of the TLS/SSL protocols use algorithms from a cipher suite to create keys and encrypt information. A cipher suite specifies one algorithm for each of the following tasks:
- Key exchange
- Bulk encryption
- Message authentication
End of the Road for TLS 1.0
Multiple Microsoft products and services have defined end of life statements for TLS 1.0
UPDATE: Transport Layer Security 1.0 and 1.1 disablement
As noted in the enginnering post, TLS is an old protocol. TLS 1.0 is a security protocol first defined in 1999 for establishing encryption channels over computer networks. Microsoft has supported this protocol since Windows XP/Server 2003. While no longer the default security protocol in use by modern OS, TLS 1.0 is still supported for backwards compatibility.
The guidance provided in that post is where we should we working towards, if you are not already there.
"Microsoft recommends customers get ahead of this issue by removing TLS 1.0 dependencies in their environments and disabling TLS 1.0 at the operating system level where possible. " The same applies to TLS 1.1 - it should also be disabled, and that is noted in this post.
Update to enable TLS 1.1 and TLS 1.2 as default secure protocols in WinHTTP in Windows
AD FS
AD FS on Windows Server 2016 and 2012 R2 will need work. You will need to update the schannel settings to enable newer protocols, disable old protocols and also disable weak ciphers.
Managing SSL/TLS Protocols and Cipher Suites for AD FS
Microsoft Browsers
As announced in October of 2018, Microsoft will soon disable Transport Layer Security (TLS) 1.0 and 1.1 by default in Microsoft browsers.
September 2022 TLS 1.0 changes are discussed here in the Edge team blog.
Behavior when accessing TLS 1.0 and 1.1 links in the browser:
After September 20, 2022, a message will appear when your browser opens a website that uses TLS 1.0 or 1.1. See Figure 1. The message states that the site uses an outdated or unsafe TLS protocol. To address this, you can update the TLS protocol to TLS 1.2 or above.
Exchange Server
Exchange Team's guidance on moving to TLS 1.2, these are the original instructions on enabling TLS 1.2 for schannel and .NET framework.
Note though that the original blog article is now depreciated, and the full guidance is contained within the regular documentation.
Protocols in TLS/SSL (Schannel SSP)
For the .NET Framework Transport Layer Security (TLS) best practices with the .NET Framework
TLS 1.3 support has not been added to Windows Server. See this post from August 2020, where upcoming support is discussed.
The Time Before TLS
Private Communications Technology (PCT) 1.0 - this was a Microsoft protocol which should not be used. Wikipedia has a brief write up on its history.
Microsoft TLS Reference
For administrators, a good reference point for TLS configuration is the article below.
Protocols in TLS/SSL (Schannel SSP) - Win32 apps | Microsoft Docs
And if you want to go deeper, the developer documents get into the protocol specifics.
[MS-TLSP]: Client and Server Hello Messages | Microsoft Docs
Cheers,
Rhoderick