Rather than kicking it old school and using the classic tools such as AD Users & Computers (dsa.msc) to move FSMO roles, PowerShell makes it nice and easy to get this done rapidly.
In this example we are moving the roles gracefully, but there is also the -Force option.
State Of The Nation
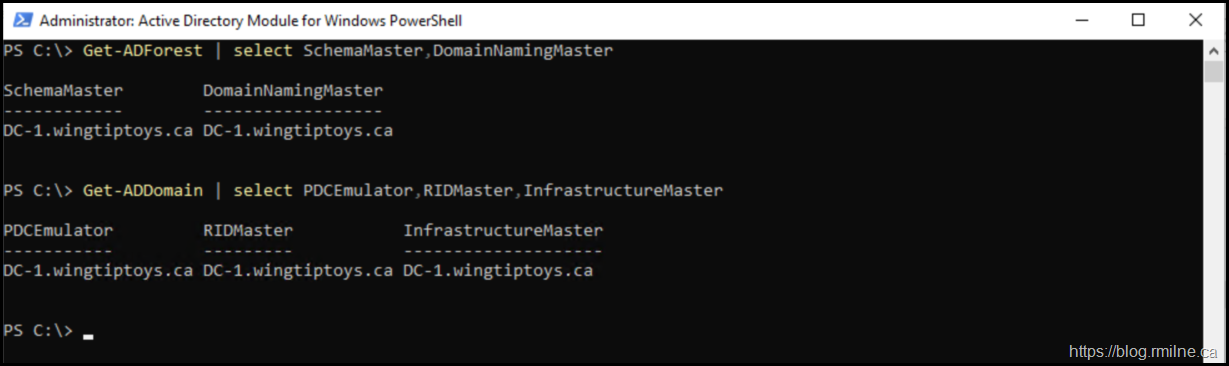
To start with, let's confirm where the FSMO roles currently reside:
Get-ADForest | Select SchemaMaster,DomainNamingMaster
Get-ADDomain | Select PDCEmulator,RIDMaster,InfrastructureMaster
Note that server DC-1.wingtiptoys.ca is where all the FSMO roles currently reside.
Moving Roles
The PowerShell cmdlet to move roles is:
Move-ADDirectoryServerOperationMasterRole
Note that we need to tell it what roles are to be moved and the roles can be identified using either a zero based numbering scheme or text label. Text is self explanatory and more readable so that is my preference. The roles and numbers are listed below.
| Role Name | Number |
| PDCEmulator | 0 |
| RIDMaster | 1 |
| InfrastructureMaster | 2 |
| SchemaMaster | 3 |
| DomainNamingMaster | 4 |
Using numbers to represent FSMO roles:
Move-ADDirectoryServerOperationMasterRole -Identity 2019-DC-1 -OperationMasterRole 0,1,2,3,4
Using text to represent FSMO roles.
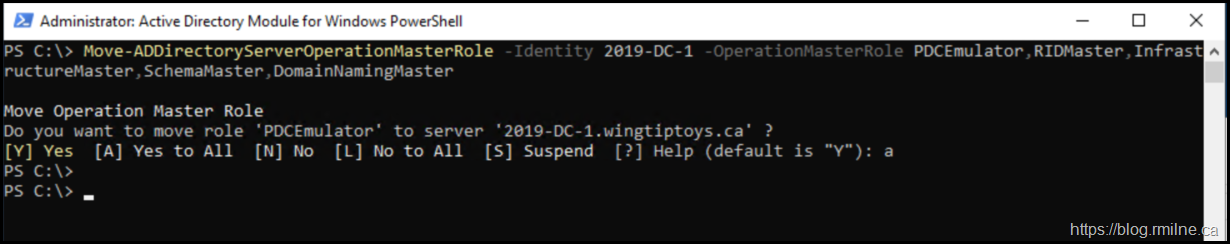
Move-ADDirectoryServerOperationMasterRole -Identity 2019-DC-1 -OperationMasterRole PDCEmulator,RIDMaster,InfrastructureMaster,SchemaMaster,DomainNamingMaster
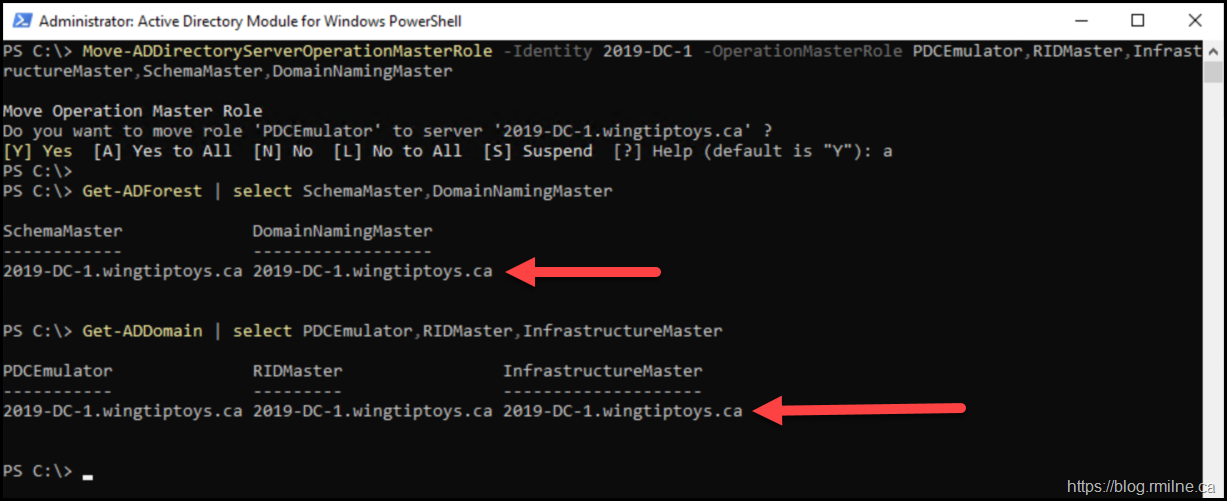
Confirm that the roles were moved, running the same commands used to show the initial layout.
Get-ADForest | Select SchemaMaster,DomainNamingMaster
Get-ADDomain | Select PDCEmulator,RIDMaster,InfrastructureMaster
The red arrows show that the FSMO roles are now on server 2019-DC-1 where previously they were located on a different server (DC-1).
Troubleshooting
Some issues to be aware of.
Group Membership
The account performing the task still requires membership in the appropriate AD group to perform the task
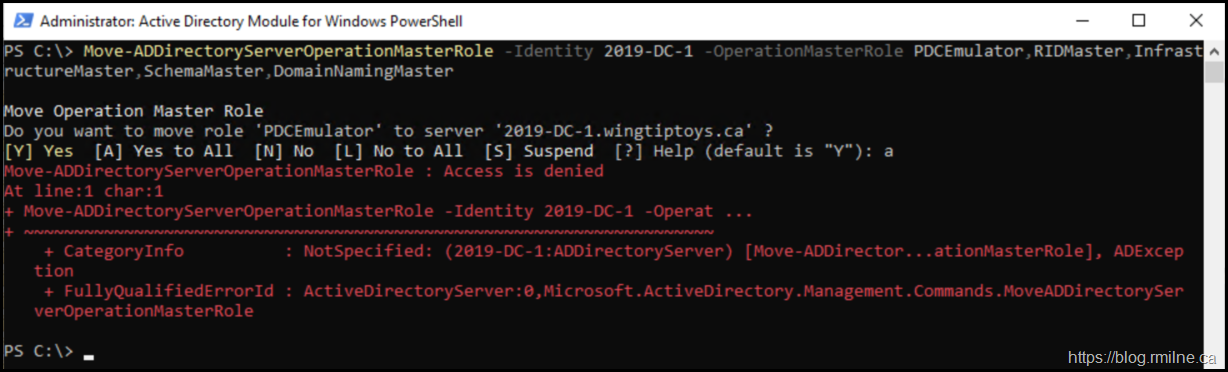
Elevated PowerShell
Run the commands in an elevated session, else you may get Access is Denied errors as show below.
Cheers,
Rhoderick