Admins have become very aware of the need to adjust the Schannel protocol settings for TLS to enable TLS 1.2 and to disable older versions. However, the cipher suites do not always receive the same amount of attention and may be left at their default values.
If you are reading this post there is a good chance that your security auditors have flagged a weak cipher is enabled on your server, and they want it disabled.
This post is specific to the issues around 3DES and SWEET32 which is CVE-2016-2183.
This attack leverages birthday attack probability theory to abuse the higher number of collisions. As noted in the NVD:
The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted session, as demonstrated by an HTTPS session using Triple DES in CBC mode
Windows will display this as the TLS_RSA_WITH_3DES_EDE_CBC_SHA cipher.
Security Audit Findings
The below are some examples of what may be provided by the security auditor. The exact text and description will depend on the security scan tool.
-
SSL Medium Strength Cipher Suites Supported (SWEET32)
-
Medium Strength Ciphers (> 64-bit and < 112-bit key, or 3DES)
-
Reconfigure the affected application if possible to avoid use of medium strength ciphers.
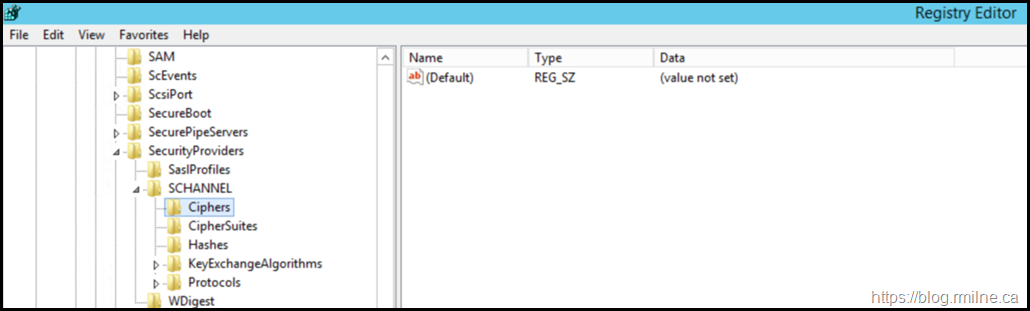
When reviewing the server in question, the below is an example of the registry which is missing the key and value to disable 3DES.
Windows Server 2012 R2 Remediation
Docs outlines all of the relevant information for Schannel protocols and algorithms.
The Ciphers registry key under the SCHANNEL key is used to control the use of symmetric algorithms such as DES and RC4. In this post we will disable the ciphers at this level. You could also edit the list of ciphers stored under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Cryptography\Configuration\Local\SSL\00010002 but that would require a little bit more work.
To disable 3DES at the Schannel level of the registry, create the below:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168
Type: DWORD
Name:Enabled
Value: 0
Note the value is zero or 0x0 in hex.
To create the required registry key and path, the below are two sample commands. The first creates the intermediate "Triple DES 168" registry key. This is required as PowerShell will error out if the “Triple DES 168” key does not exist.
New-Item -Path "HKLM:SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168" –Force
New-ItemProperty -Path "HKLM:SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168" -Name "Enabled" -PropertyType DWORD -Value "0x0" –Force
Note that Disable-TlsCipherSuite is not available for Windows Server 2012 R2. It is available for Windows Server 2016 onwards.
Windows Server 2012 R2 Verification
To verify if the server has the registry set to disable 3DES:
Get-ItemProperty -Path "HKLM:SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168" -Name Enabled | Select-Object Enabled | FT -Autosize
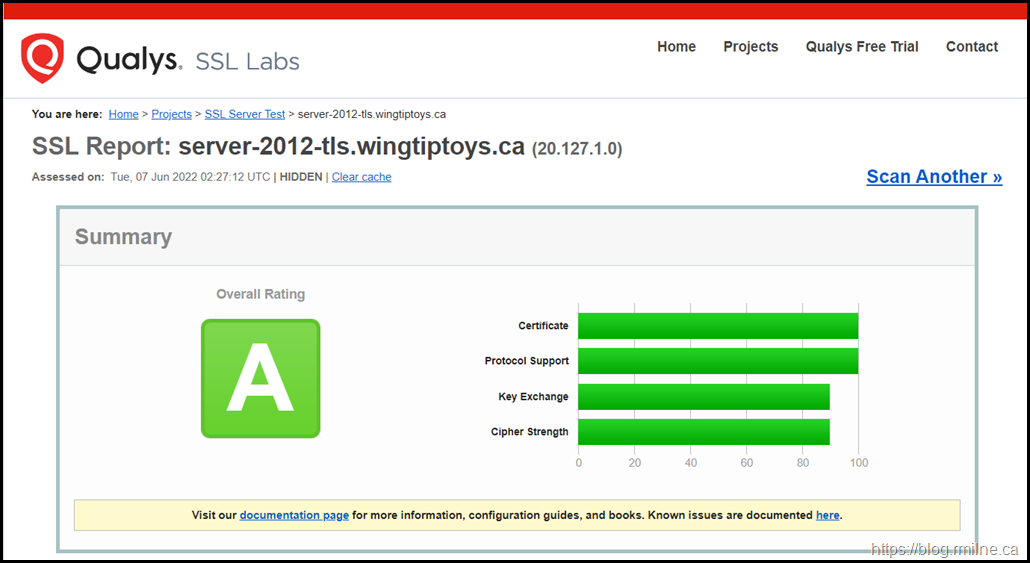
Once the registry value was added, you should then see the cipher has been removed from a SSL Labs scan.
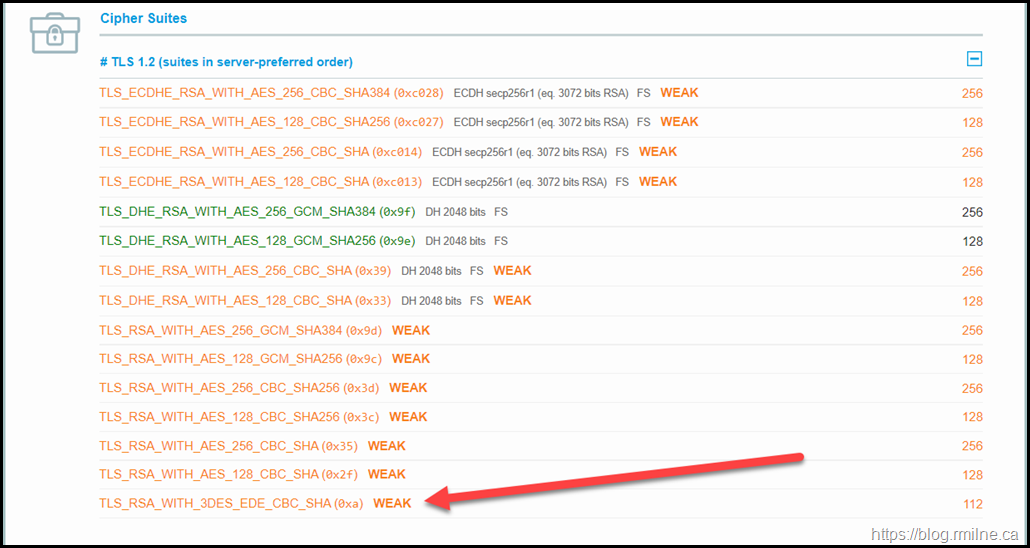
Note that TLS_RSA_WITH_3DES_EDE_CBC_SHA is not visible is the SSL Labs output.
SSL Labs Reference
Note that just because you have a grade A rating on SSL Labs, that does not mean that all issues are resolved.
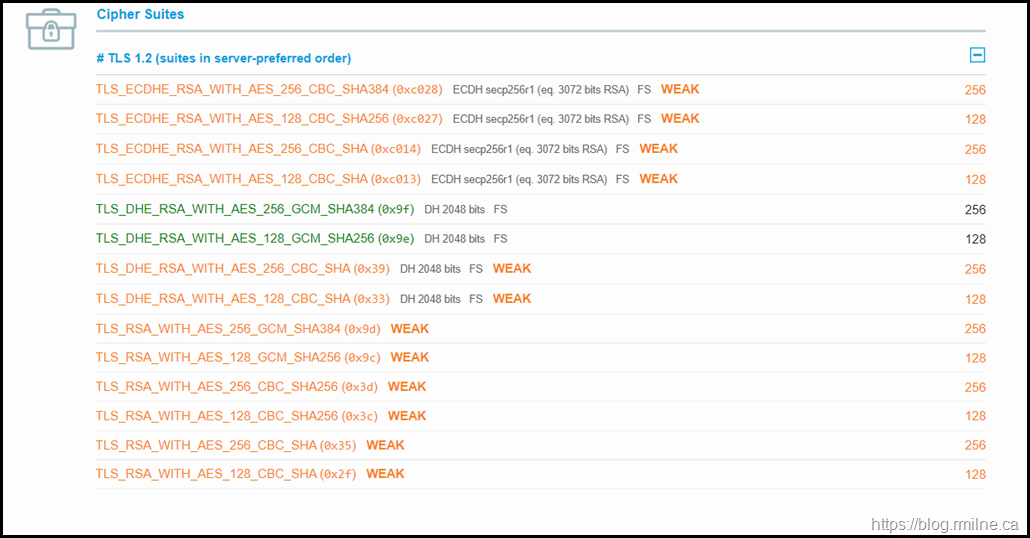
The below image is a Windows Server 2012 R2 test system with only TLS 1.2 enabled and weak DH disabled. The Certificate and Protocol Support sections are both 100%, the Key Exchange and Cipher Strength are not. You are encouraged to read the tool’s documentation to understand the scoring algorithm.
If we scroll down to the Cipher Suites section on the page, we can see why the Cipher Strength rating was not 100%
For the SWEET32 issue, the TLS_RSA_WITH_3DES_EDE_CBC_SHA cipher is highlighted.
Cheers,
Rhoderick
Oct 2024 now. just found out TLS_RSA_WITH_3DES_EDE_CBC_SHA with TLS 1.2 is still allowed in Azure services like storage account.