Wireshark is the industry tool for packet inspection, but you don’t always want, or are able, to install this onto production systems without a change request. Whether you’re troubleshooting or investigating an issues, there are alternative ways to capture meaningful network traffic without installing Wireshark. Ultimately we want to produce PCAPs easily without having to mess with switchport mirroring. Wireshark can then be used to open up and analyse the capture file. While there are others posts out there, some have incorrect parameters.
Windows has the built in Netsh.exe and also nowadays Packet Monitor (pktmon.exe) tools that are able to capture network traffic. PKMon (Packet Monitor) is a relatively new built-in network capture tool that was first introduced in Windows 10, version 2004 (May 2020 Update), and in the corresponding Windows Server 2022 builds. It was not backported – this is a Windows Server 2016 machine where Packet Monitor was not found.
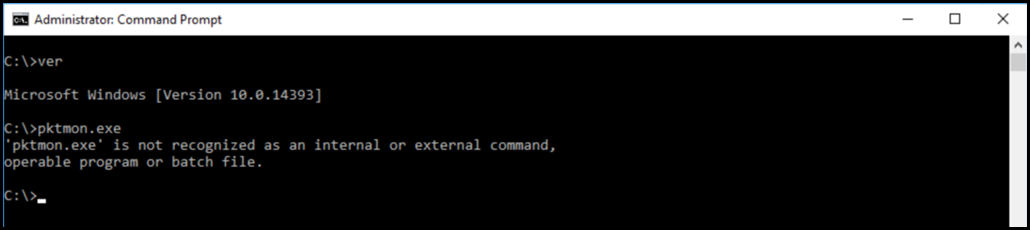
Packet Monitor
As noted above Packet Monitor was released with Windows 10 2004 (build 19041, released May 2020). Windows 10 20H2 added the ability to natively convert captures to PCAP format directly (pktmon.exe pcapng), so you can open them in Wireshark. This is cleaner than the older Netsh method – yay!
Additional improvements were made in Windows 11 and Server 2022. This includes:
- Broader Capture Coverage
-
- Windows 10 (2004/20H2): Captured at the NDIS (Network Driver Interface Specification) level — mainly packet-level data
- Windows 11 / Server 2022: Introduced the “Packet Monitor in the Networking Stack (NetEvent)” model, allowing capture across higher-level networking layers, including TCP/IP stack events, firewall, and virtual switch traffic
- You can now trace events beyond just raw packets; such as drops, filters, and stack component activity
- Enhanced Output and File Handling
-
- Added direct PCAPNG export as a first-class output (no conversion step needed)
- pktmon start --capture --pkt-size 0 --comp "Ethernet" --pcapng capture.pcapng
- Added direct PCAPNG export as a first-class output (no conversion step needed)
-
- Improved performance when converting ETL logs to PCAPNG
- Better timestamp precision and alignment for Wireshark or Network Monitor correlation
- Real-time Monitoring and Filtering
-
- Support for live, real-time packet display:
This lets you watch traffic as it flows, similar to tcpdump or netsh trace start capture=yes
- Support for live, real-time packet display:
-
-
Improved filtering syntax — you can now target by MAC address, IP, port, or even NDIS component name directly
-
-
-
-
pktmon filter add --address 10.0.0.5 --direction in
-
-
- Integration with Windows Filtering Platform (WFP)
-
- In Windows 11 and Server 2022, Packet Monitor integrates more deeply with WFP events, allowing you to see firewall and packet drop reasons within captures
- You can correlate packets with the policy or driver responsible for allowing or blocking traffic
- Stability, Performance, and Usability
-
- Substantial performance improvements in high-throughput environments (reduced packet loss)
- Better behaviour on systems with virtual adapters (Hyper-V, WSL2, VPN clients)
- Cleaner output format and more consistent command-line help (pktmon help)
- Unified Diagnostic Scenarios
-
- On Windows 11/2022, Packet Monitor is part of the “Network Diagnostic Framework”, which means it can integrate with other troubleshooting tools like netsh trace, Event Viewer, and Windows Performance Recorder (WPR)
- This allows unified trace sessions that include both packet data and system/network events
Packet Monitor Filters
Packet Monitor has multiple filtering options:
- Packet Monitor supports filtering by MAC addresses, IP addresses, ports, EtherType, transport protocol, and VLAN ID
- Packet Monitor will not distinguish between source or destination when it comes to MAC address, IP address, or port filters
- To further filter TCP packets, an optional list of TCP flags to match can be provided. Supported flags are FIN, SYN, RST, PSH, ACK, URG, ECE, and CWR
Packet Monitor Sample Commands
Some sample commands to get started with Packet Monitor.
Simple Capture
The simplest capture command would be just to start a capture. This will create a circular output file called Pktmon.etl in the current folder with a maximum file size is of 512 MB. No filters were added so that will bloat very quickly. Don't do that 🙂
pktmon start -capture
Slightly More Interesting Capture
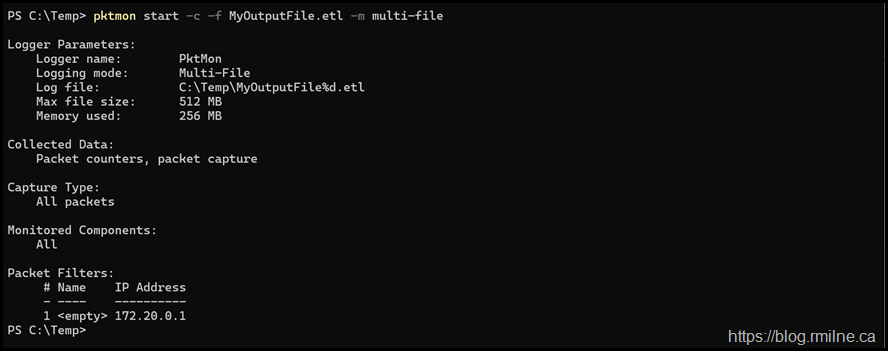
Starts the capture with a specified file name, multi file will create new files when max file size is reached
pktmon start -c -f MyOutputFile.etl -m multi-file
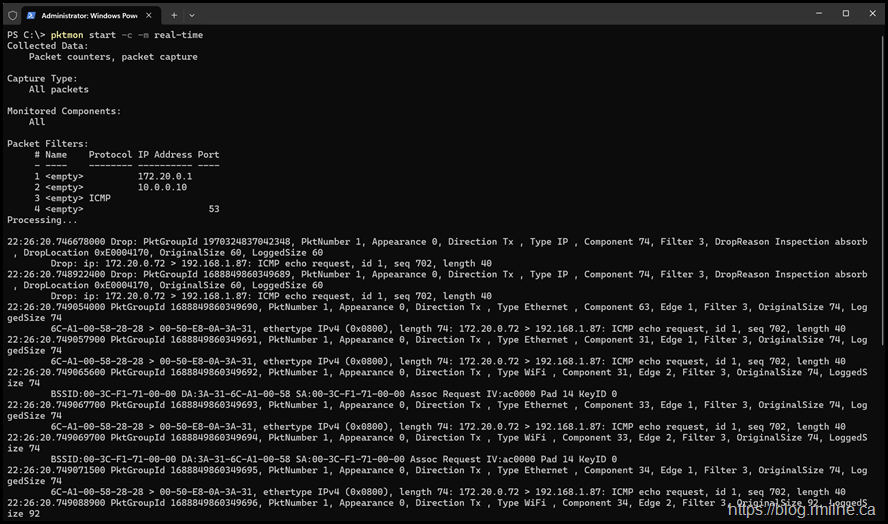
Real Time Capture
This displays output live on screen. Same applies for a real-time capture with no filter, just don't.
pktmon start -c -m real-time
Check Status
pktmon status
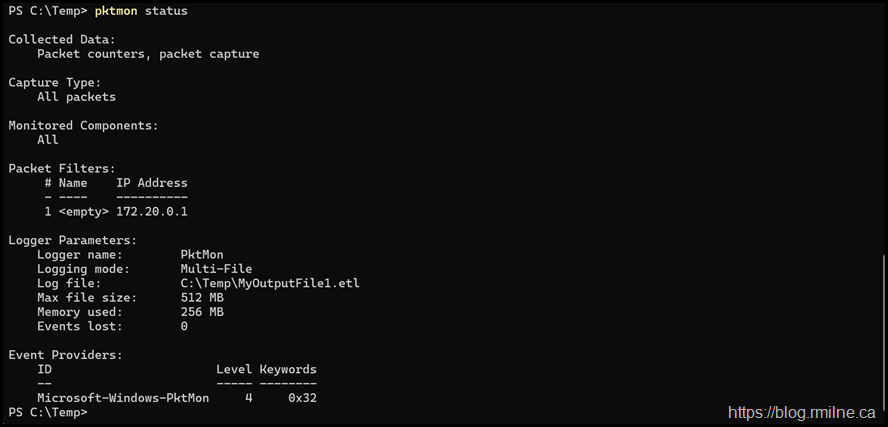
Stop capture
pktmon stop

List Filters
pktmon filter list

Filter IP
Add a filter to control which packets are reported. For a packet to be reported, it must match all conditions specified in at least one filter.
Up to 32 filters can be active at once.
Filter traffic to/from specific IP
pktmon filter add -i 10.0.0.10

Filter Type - ICMP
pktmon filter add -t icmp

Filter Port
Filter traffic on specific port
pktmon filter add -p 53

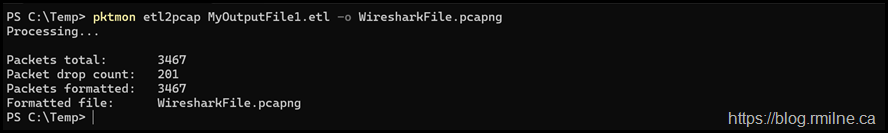
Convert to PCAP
Convert pktmon log file to pcapng format. Packet drops are not included by default. Alias: e2p
pktmon etl2pcap MyTraceFile.etl -o WiresharkFile.pcapng
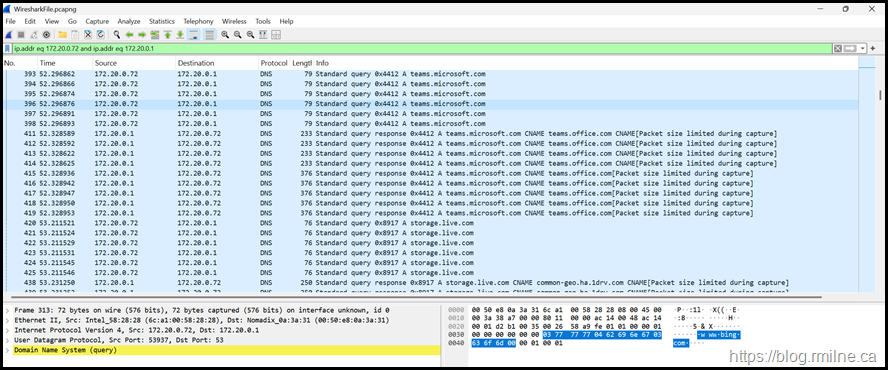
Here is the resulting WireshareFile.pcapng open in Wireshark:
Netsh Sample Command
This is very standard example of a capture.
Netsh.exe Trace Start Capture=yes IPv4.DestinationAddress=20.125.170.99 Protocol=6 Maxsize=1024 Filemode=circular Tracefile=c:\temp\NetCapture.etl
Note that you will then need to convert the .etl to a PCAP. See the next section.
Netsh Convert ETL
While it is great that we can capture data using Netsh, it can not be opened as-is in Wireshark. This is where the ETL2PCAP utility comes into play. It will do that conversion so that the network trace can be opened in Wireshark.
Download the tool from:
There are pre-built binaries that can be simply downloaded.
etl2pcapng.exe Source.etl Destination.pcapng
Reference – Protocol Numbers
TCP (Transmission Control Protocol): Protocol number 6
UDP (User Datagram Protocol): Protocol number 17
ICMP (Internet Control Message Protocol): Protocol number 1
IGMP (Internet Group Management Protocol): Protocol number 2
IPv4 (Internet Protocol version 4): Protocol number 4
IPv6 (Internet Protocol version 6): Protocol number 41
Reference Packet Monitor Help File Content
Note that this was for the addition of filters, of you want to see help for the other areas, just change the command. The command options are shown below:
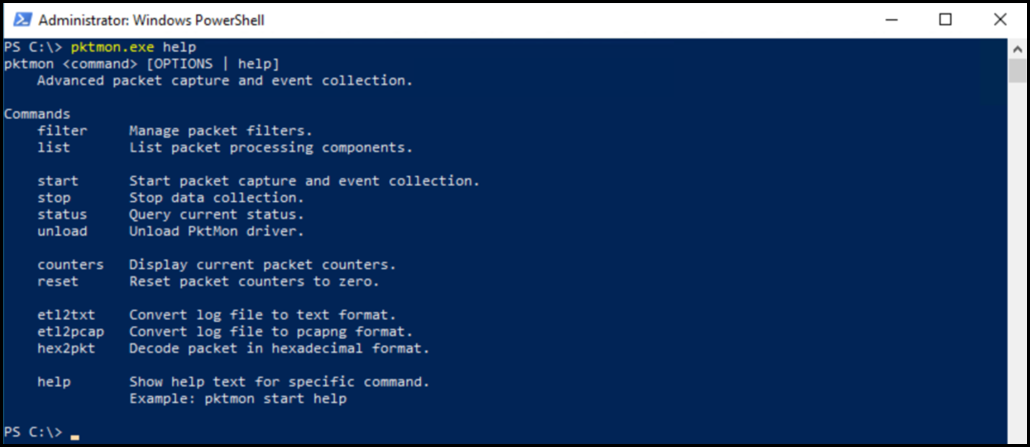
The below is output from running showpktmon.exe filter add help. It has been changed in format to improve the readability somewhat.
pktmon filter add <name> [-m <mac> [mac2]] [-v <vlan>] [-d { IPv4 | IPv6 | number }]
[-t { TCP [flags...] | UDP | ICMP | ICMPv6 | number }]
[-i <ip> [ip2]] [-p <port> [port2]] [-b] [-e [port]]
Add a filter to control which packets are reported. For a packet to be reported, it must match all conditions specified in at least one filter.
Up to 32 filters can be active at once.
NOTE1: When two MACs (-m), IPs (-i), or ports (-p) are specified, the filter matches packets that contain both. It will not distinguish between source
or destination for this purpose.
name
Optional name or description of the filter.
Ethernet frame
-m, --mac[-address]
Match source or destination MAC address. See NOTE1 above.
-v, --vlan
Match by VLAN Id (VID) in the 802.1Q header.
-d, --data-link[-protocol], --ethertype
Match by data link (layer 2) protocol. Can be IPv4, IPv6, ARP, or a protocol number.
IP header
-t, --transport[-protocol], --ip-protocol
Match by transport (layer 4) protocol. Can be TCP, UDP, ICMP, ICMPv6, or a protocol number.
To further filter TCP packets, an optional list of TCP flags to match can be provided. Supported flags are FIN, SYN, RST, PSH, ACK, URG, ECE, and CWR.
-i, --ip[-address]
Match source or destination IP address. See NOTE1 above. To match by subnet, use CIDR notation with the prefix length.
TCP/UDP header
-p, --port
Match source or destination port number. See NOTE1 above.
Cluster Heartbeat
-b, --heartbeat
Match RCP heartbeat messages over UDP port 3343.
Encapsulation
-e, --encap
Apply above filtering parameters to both inner and outer encapsulation headers. Supported encapsulation methods are VXLAN, GRE, NVGRE, and IP-in-IP.
Custom VXLAN port is optional, and defaults to 4789.
Example 1: Ping filter
pktmon filter add MyPing -i 10.10.10.10 -t ICMP
Example 2: TCP SYN filter for SMB traffic
pktmon filter add MySmbSyn -i 10.10.10.10 -t TCP SYN -p 445
Example 3: Subnet filter
pktmon filter add MySubnet -i 10.10.10.0/24
Reference – Netsh Help File Content
The below is output from running show capturefilter in Netsh\Trace. It has been changed in format to improve the readability somewhat.
Capture Filters:
Capture filters are only supported when capture is explicitly enabled with capture=yes. Supported capture filters are:
CaptureInterface=
Enables packet capture for the specified interface name or GUID. Use 'netsh trace show interfaces' to list available interfaces.
e.g. CaptureInterface={716A7812-4AEE-4545-9D00-C10EFD223551}
e.g. CaptureInterface=!{716A7812-4AEE-4545-9D00-C10EFD223551}
e.g. CaptureInterface="Local Area Connection"
Ethernet.Address=
Matches the specified filter against both source and destination MAC addresses.
e.g. Ethernet.Address=00-0D-56-1F-73-64
Ethernet.SourceAddress=
Matches the specified filter against source MAC addresses.
e.g. Ethernet.SourceAddress=00-0D-56-1F-73-64
Ethernet.DestinationAddress=
Matches the specified filter against destination MAC addresses.
e.g. Ethernet.DestinationAddress=00-0D-56-1F-73-64
Ethernet.Type=
Matches the specified filter against the MAC ethertype.
e.g. Ethernet.Type=IPv4
e.g. Ethernet.Type=NOT(0x86DD)
e.g. Ethernet.Type=(IPv4,IPv6)
Wifi.Type=
Matches the specified filter against the Wifi type. Allowed values are 'Management' and 'Data'. If not specified, the Wifi.Type filter is not applied.
Note: This capture filter does not support ranges, lists or negation.
e.g. Wifi.Type=Management</MANAGEMENT|DATA>
Protocol=
Matches the specified filter against the IP protocol.
e.g. Protocol=6
e.g. Protocol=!(TCP,UDP)
e.g. Protocol=(4-10)
IPv4.Address=
Matches the specified filter against both source and destination IPv4 addresses.
e.g. IPv4.Address=157.59.136.1
e.g. IPv4.Address=!(157.59.136.1)
e.g. IPv4.Address=(157.59.136.1,157.59.136.11)
IPv4.SourceAddress=
Matches the specified filter against source IPv4 addresses.
e.g. IPv4.SourceAddress=157.59.136.1
IPv4.DestinationAddress=
Matches the specified filter against destination IPv4 addresses.
e.g. IPv4.DestinationAddress=157.59.136.1
IPv6.Address=
Matches the specified filter against both source and destination IPv6 addresses.
e.g. IPv6.Address=fe80::5038:3c4:35de:f4c3\%8
e.g. IPv6.Address=!(fe80::5038:3c4:35de:f4c3\%8)
IPv6.SourceAddress=
Matches the specified filter against source IPv6 addresses.
e.g. IPv6.SourceAddress=fe80::5038:3c4:35de:f4c3\%8
IPv6.DestinationAddress=
Matches the specified filter against destination IPv6 addresses.
e.g. IPv6.DestinationAddress=fe80::5038:3c4:35de:f4c3\%8
CustomMac=
Matches the specified filter against the value at the specified offset starting with the MAC header.
Note: This capture filter does not support ranges, lists or negation.
e.g. CustomMac=UINT8(0x1,0x23)
e.g. CustomMac=ASCIISTRING(3,test)
e.g. CustomMac=UNICODESTRING(2,test)</TYPE(OFFSET,VALUE)>
CustomIp=
Matches the specified filter against the value at the specified offset starting with the IP header.
Note: This capture filter does not support ranges, lists or negation.
e.g. CustomIp=UINT16(4,0x3201)
e.g. CustomIp=UINT32(0x2,18932)</TYPE(OFFSET,VALUE)>
CaptureMultiLayer=
Enables multi-layer packet capture.
Note: This capture filter does not support ranges, lists or negation.</YES|NO>
PacketTruncateBytes=
Captures only the specified number of bytes of each packet.
Note: This capture filter does not support ranges, lists or negation.
e.g. PacketTruncateBytes=40
Note:
Multiple filters may be used together. However the same filter may not be repeated.
e.g. 'netsh trace start capture=yes Ethernet.Type=IPv4 IPv4.Address=157.59.136.1'
Filters need to be explicitly stated when required. If a filter is not specified, it is treated as "don't-care".
e.g. 'netsh trace start capture=yes IPv4.SourceAddress=157.59.136.1'
This will capture IPv4 packets only from 157.59.136.1, and it will also capture packets with non-IPv4 Ethernet Types, since the Ethernet.Type filter is not explicitly specified.
e.g. 'netsh trace start capture=yes IPv4.SourceAddress=157.59.136.1 Ethernet.Type=IPv4'
This will capture IPv4 packets only from 157.59.136.1. Packets with other Ethernet Types will be discarded since an explicit filter has been specified.
Capture filters support ranges, lists and negation (unless stated otherwise).
e.g. Range: 'netsh trace start capture=yes Ethernet.Type=IPv4 Protocol=(4-10)'
This will capture IPv4 packets with protocols between 4 and 10 inclusive.
e.g. List: 'netsh trace start capture=yes Ethernet.Type=(IPv4,IPv6)'
This will capture only IPv4 and IPv6 packets.
e.g. Negation: 'netsh trace start capture=yes Ethernet.Type=!IPv4'
This will capture all non-IPv4 packets.
Negation may be combined with lists in some cases.
e.g. 'netsh trace start capture=yes Ethernet.Type=!(IPv4,IPv6)'
This will capture all non-IPv4 and non-IPv6 packets.
'NOT' can be used instead of '!' to indicate negation. This requires parentheses to be present around the values to be negated.
e.g. 'netsh trace start capture=yes Ethernet.Type=NOT(IPv4)'