Active Directory synchronization was designed not just to move objects from on-premises AD to Azure AD, but to give administrators precise control over how identities were matched, transformed, and filtered. This is not a new thing. It dates back to very early days of Microsoft cloud hosted email, both commercial and educational orientated. Azure AD Connect evolved from earlier solutions such as DirSync, introduced around 2008 for BPOS, which offered basic synchronization capabilities but limited flexibility. Azure AD Sync added more configuration options. In 2015, Azure AD Connect was released as a unified, more robust platform, consolidating these older tools and introducing enhanced features like custom sync rules, filtering, and soft/hard matching. Over time AD Connect has continued to evolve with support for hybrid write-back, seamless single sign-on, and password hash synchronisation, becoming the standard solution for organisations managing their hybrid environments.
While the typical install of Azure AD Connect is sufficient for most customers, we also need to be aware of the advanced/additional option.
One of these additional features is soft match, which allowed Azure AD Connect to link an existing cloud user with an on-premises object based on matching attributes such as the userPrincipalName or mail address, reducing duplicate accounts during migrations. But there is no guarantee that sue@tailspintoys.ca in the cloud is the same person the account sue@tailspintoys.ca in a newly added directory. Hard match complemented this by using the immutableId to enforce strict mappings between objects. Beyond matching, AD Connect allowed attribute filtering, letting admins include or exclude users, groups, or organizational units, and attribute transformation rules, enabling modifications such as normalizing phone numbers or combining multiple attributes into one. For complex deployments, custom sync rules could be defined to handle scenarios like overlapping email domains or multi-forest environments. Together, these options made AD Sync highly flexible, but they required careful design and testing to ensure identities remained consistent across hybrid environments.
Note that some operations are permanent. Once they are enabled, they can not be disabled. Enabling these features, such as EnableSoftMatchOnUpn and SynchronizationUpnForManagedUsers, is a permanent operation. You can't disable these features once they're enabled.
Update: Note that MSOL PoweShell is no longer supported. Use Graph instead.
Password Hash Sync
Typically you will enable this by running the Azure AD Connect Configuration wizard. If needed, it can be enabled via PowerShell.
Password Writeback
Enable via the Azure AD Connect configuration wizard.
No longer can be enabled via PowerShell.
SynchronisedUpnForManagedUser
Historically, updates to the UserPrincipalName attribute using the sync service from on-premises was blocked, unless both of these conditions were true:
- The user managed (nonfederated).
- The user doesn't have a license assigned
Note that the federation restriction was removed in 2019.
Enabling this feature allows the sync engine to update the userPrincipalName when it is changed on-premises and you use password hash sync or pass-through authentication.
This feature is on by default for newly created Microsoft Entra directories. After enabling this feature, existing userPrincipalName values remain as-is. On next change of the userPrincipalName attribute on-premises, the normal delta sync on users updates the UPN. Once this feature is enabled, it's not possible to disable it.
BlockSoftmatch
As noted in the documentation, there is a suggestion that soft match should be disabled if we do not want to use it.
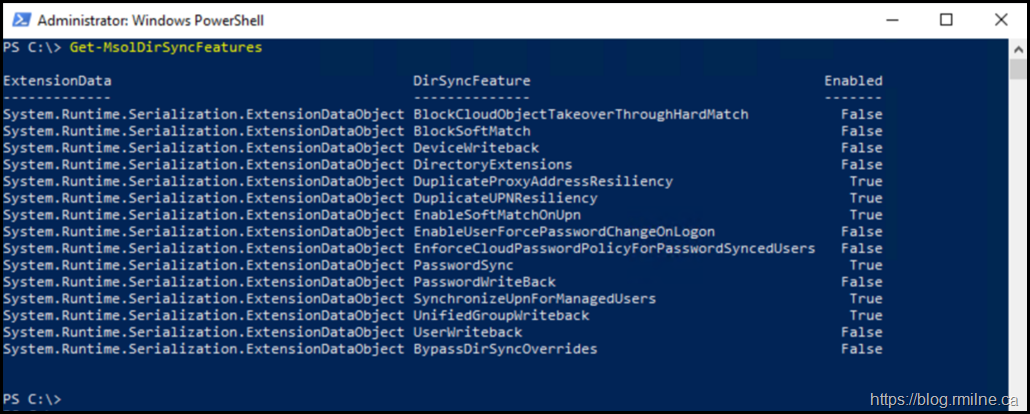
We can run Get-MsolDirSyncFeatures to list the options.
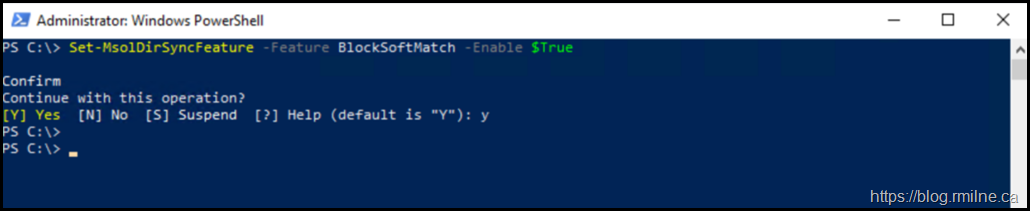
Set-MsolDirSyncFeature -Feature BlockSoftMatch -Enable $True
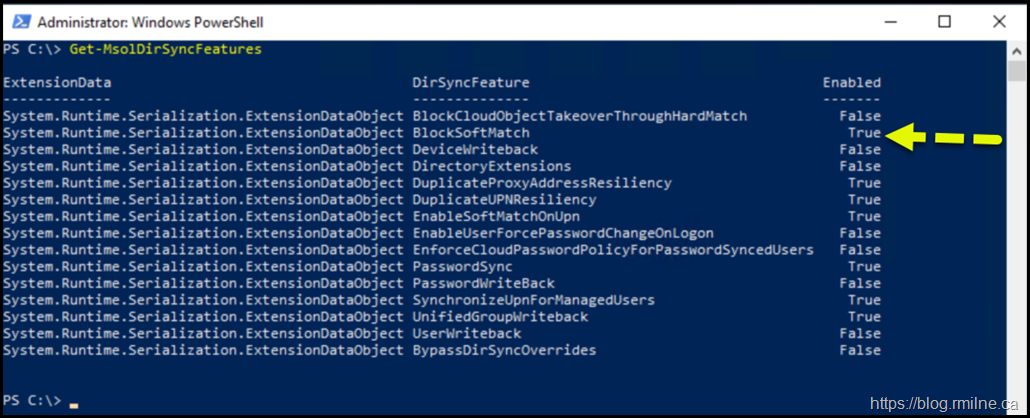
Re-running Get-MsolDirSyncFeatures afterwards shows that BlockSoftMatch is now enabled.
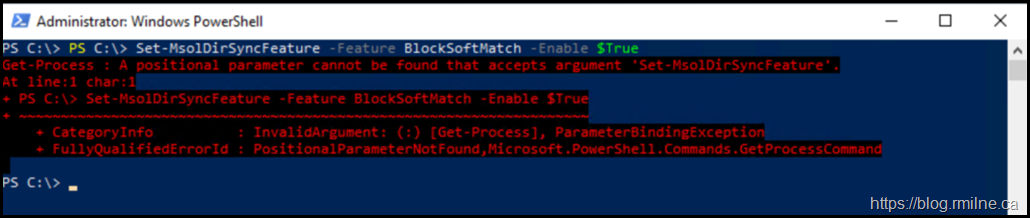
Be careful if you just copy the example from Docs – it may also bring over the unwanted characters at the beginning of the line. Note that there are multiple prompts in the example below.
Get-Process : A positional parameter cannot be found that accepts argument 'Set-MsolDirSyncFeature'.
At line:1 char:1
+ PS C:\> Set-MsolDirSyncFeature -Feature BlockSoftMatch -Enable $True
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidArgument: (:) [Get-Process], ParameterBindingException
+ FullyQualifiedErrorId : PositionalParameterNotFound,Microsoft.PowerShell.Commands.GetProcessCommand