This is the second in a series of three posts which will walk you through installing, configuring and connecting AD FS 2016 to Office 365. In part one we installed the AD FS server on our corporate network, and tested that it was working.
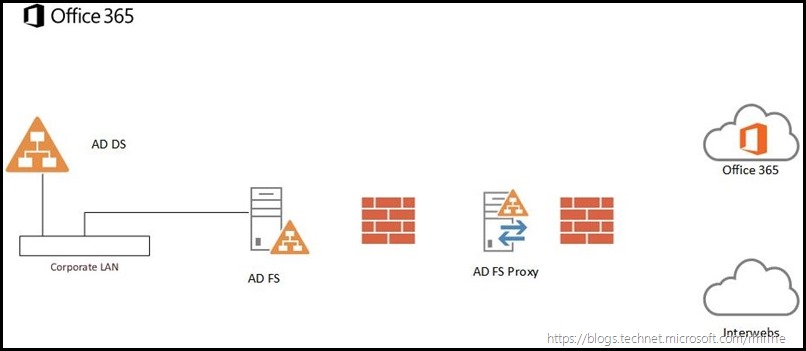
In this second post we need to make the AD FS infrastructure available to the Internet in a secure fashion, so that Office 365 will be able to contact AD FS to authenticate user requests. Previously this meant downloading and installing the AD FS 2.0 Proxy onto servers in the DMZ. In AD FS 2012 R2 onwards, the AD FS proxy functionality is present in the Web Application Publishing (WAP) component of the Remote Access role. There is no separate download required in modern versions of Windows.
In part three of this series, we will integrate the AD FS infrastructure with the Office 365 configuration.
The outcome achieved at the end of this post is the below solution. Note that the AD FS servers are domain joined an located on the corporate network. Windows 2012 R2 and newer contain the AD FS Proxy as part of the OS, specifically within the Remote Access role. For the purposes of using AD FS for Office 365 we do not need to domain join the WAP servers. They are able to provide AD FS proxy functionality as workgroup machines.
Planning And Prerequisites
Install And Configure AD FS Proxy OS
In this installation, the AD FS proxy server will be placed into the DMZ, and installed as a workgroup machine since the Wingtiptoys organisation does not possess a separate management forest in the DMZ. Ensure the machine is built as per your standard build process, is secured and all Microsoft updates are installed. Since AD FS and WAP are now a core part of the OS, they are serviced and maintained using Windows Updates.
Install And Verify Certificate
As discussed in part one, you will need a certificate from a trusted third party. Ensure that you check with the CA to ensure that you are able to install the certificate onto multiple servers as this is blocked in some license agreements. This is something that you must check directly with the CA.
If you are allowed to install the certificate from the AD FS server, then this simplifies matters else you will require an additional certificate. The name must match the AD FS namespace that you selected through the AD FS design process. By using the exact same certificate this allows the following features to be enabled:
-
ExtendedProtectionTokenCheck to be enabled on AD FS. It is enabled by default.
-
WAP can proxy AD FS requests that use Windows Integrated Authentication
Name Resolution
Since the AD FS proxy server[s] will be in a network which may not have access to the internal DNS zone information, ensure that WAP is able to resolve the AD FS namespace to the internal AD FS infrastructure. Typically this will point to the VIP of the internal AD FS load balanced endpoint. A swift update to the local hosts file may suffice, just remember to add this to your build documentation. In some cases you way need to set a DNS suffix in the system properties or in the IP configuration.
External DNS Record
Create external DNS record for the AD FS proxy server. This A record will exist in the external DNS zone. In the Wingtiptoys enterprise (cough, cough this lab) the internal DNS zone is held on AD integrated DNS zones. The external zone is at a commercial ISP, so the external DNS record was created at the commercial ISP so it resolves to the external IP of the AD FS proxy infrastructure when I am at Starbucks.
As with the internal AD FS farm, there should be multiple WAP servers in the DMZ. They should be load balanced, and the DNS record should resolve to the VIP.
Open Firewalls
Having the external DNS record point to the AD FS server’s external IP address will not allow traffic to flow unless the firewalls are configured to do so. In enterprises the AD FS proxy server will be installed into a DMZ so there will be an internal and external firewall. Both must be opened to allow inbound SSL traffic over TCP port 443. In addition to this, the servers will also need access to the CA's CRL distribution points on the Internet to verify certificate validity.
Exchange administrators should be used to this now as they have see Exchange updates take a long time to install on Exchange servers do not have access to crl.microsoft.com. In the case of AD FS, the server should be able to hit the CRL of external CAs. Each vendor has their own endpoints.
The AD FS server will require access to the Internet in order to complete the configuration of the solution (in the 3rd post of this series). This may be an issue if your servers are behind a proxy solution.
Installing Web Application Proxy
First we will go through the graphical install process, then review the PowerShell commands to install the necessary role services and then to configure WAP. There are two discrete tasks which are to be performed. The Remote Access role with with the Web Application Proxy service must first be installed, and then it can be configured.
Let’s fire up the Add Roles Wizard from Server Manager!
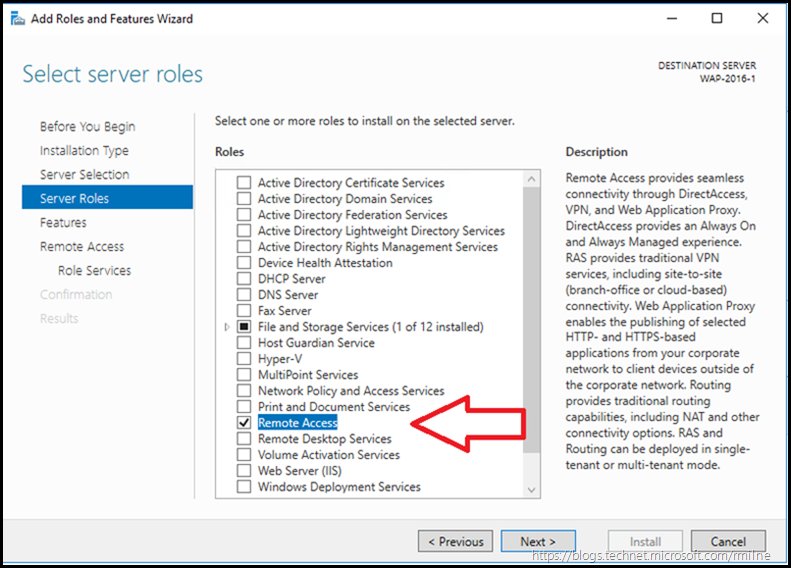
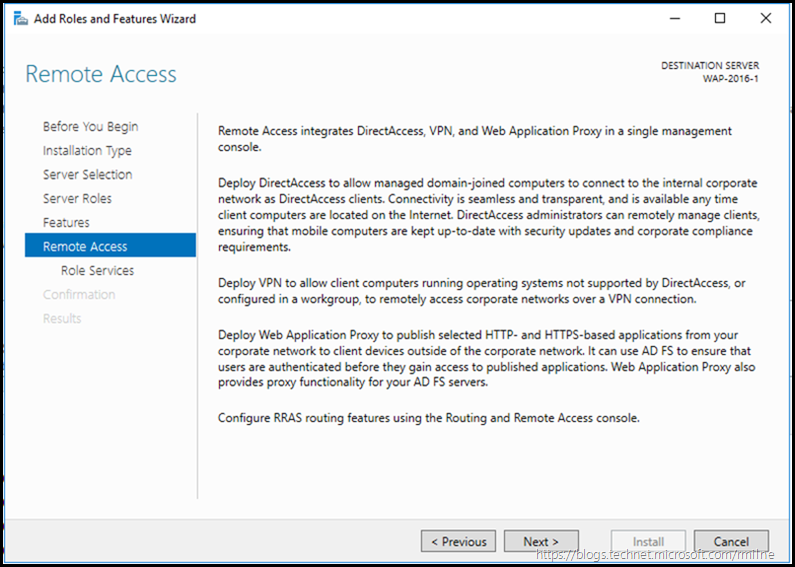
As noted in the previous post, there is no longer a separate AD FS proxy role in Windows 2016. The Remote Access feature provides VPN, Direct Access and Web Application Proxy (WAP) functionality. It is the latter that we need to install.
Select Remote Access and let’s go find the droids we are looking for…
Unless you want to add any features, like telnet * for troubleshooting purposes later, click next.
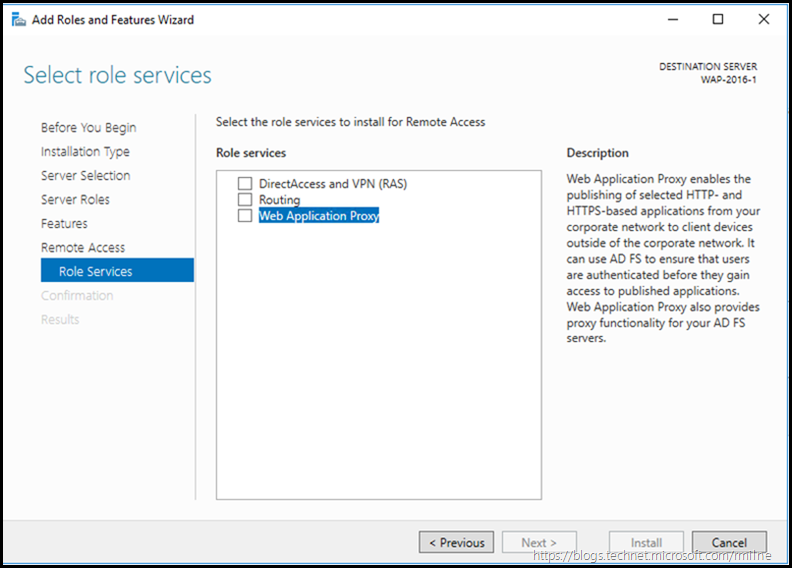
The Remote Access role selection process starts. Unlike in days of old when installing a feature would install all of the bits, and by extension potential vulnerabilities, Windows now wants to only install the bare minimum. This is a paradigm shift compared to the early days of IIS where it would install everything and then you have to spend time stripping stuff back out. Index extension attack anyone?
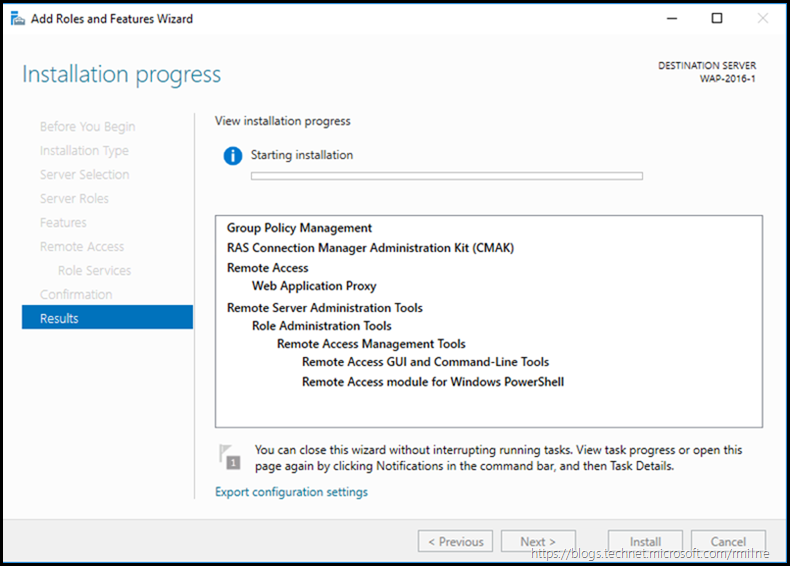
In our case we just want to install the Web Application Proxy role service, so select that and click next
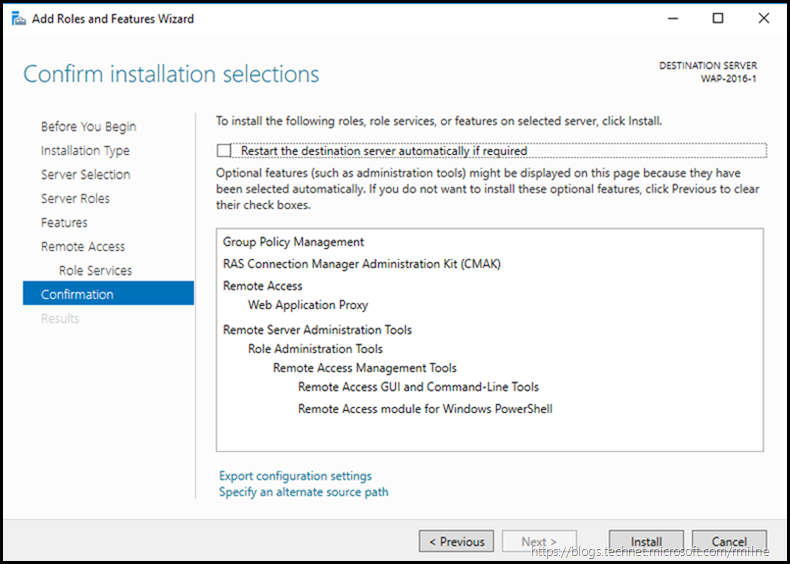
Confirm the choice, and then install.
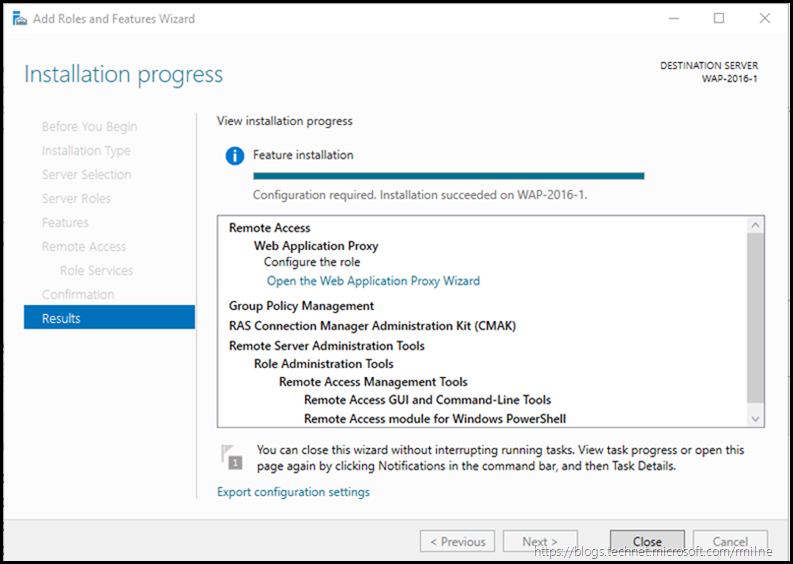
Once the necessary WAP role services are installed, we are then able to launch the Web Application Proxy Wizard to configure WAP.
The installation process will complete, click to close the wizard.
Configure Web Application Proxy
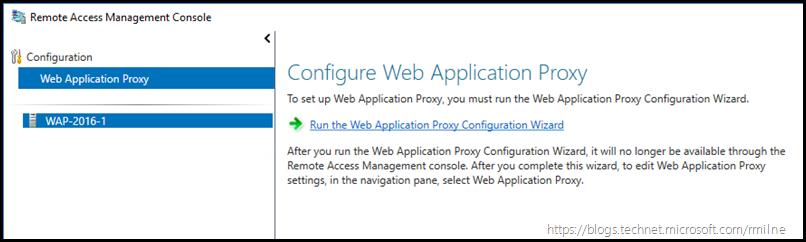
We need to configure the WAP proxy with the necessary information so that it knows it will be publishing our internal AD FS server and how to access AD FS. Under administrative tools, open the Remote Access Management console.
Select the Web Application Proxy role which is listed on the left hand pane, and then the option to run the Web Application proxy configuration wizard will be displayed.
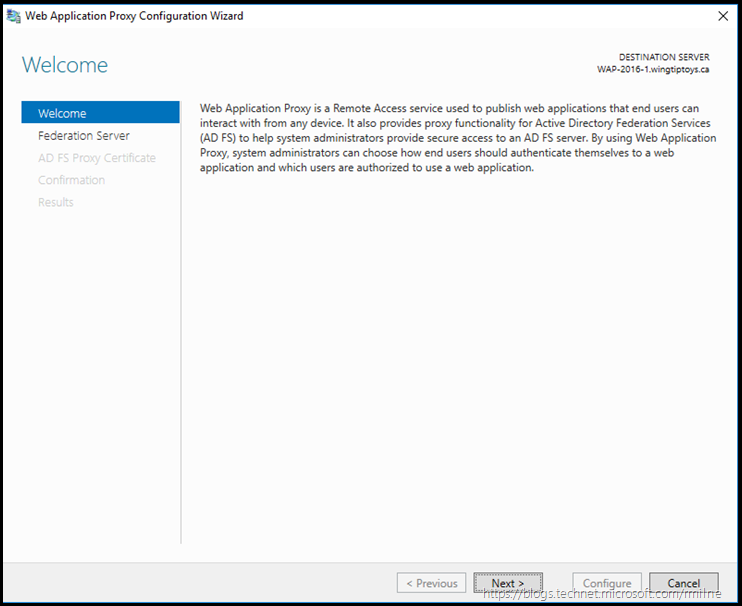
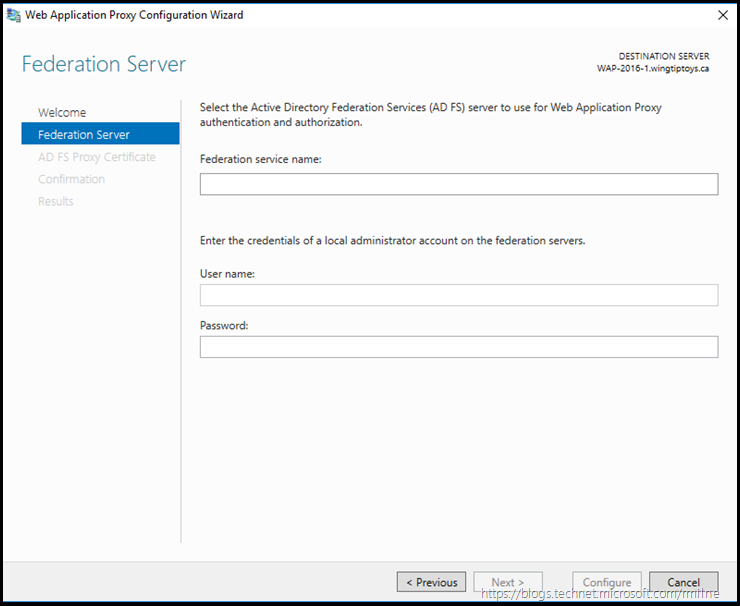
The wizard will then initiate the process to configure the Web Application Publishing service.
The screen below is where most configuration issues arise with this process. What a lot of folks do is interpret the Federation service name as the display name of the AD FS server. That will not get you very far unfortunately…
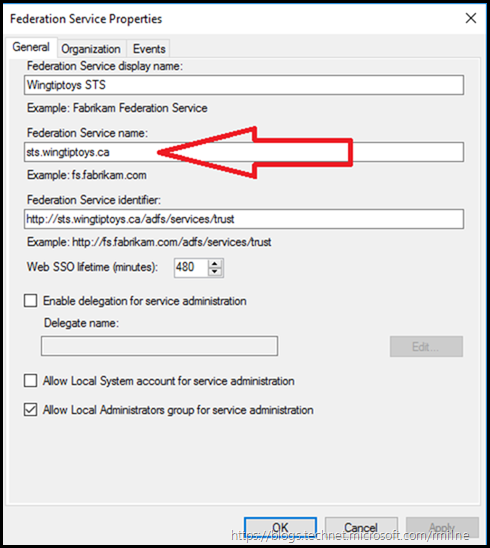
The federation service name field does NOT want you to enter the display name of the AD FS server farm. The display name in the previous example was “Wingtiptoys STS”. and this can been checked by looking in the AD FS console on the AD FS server itself.
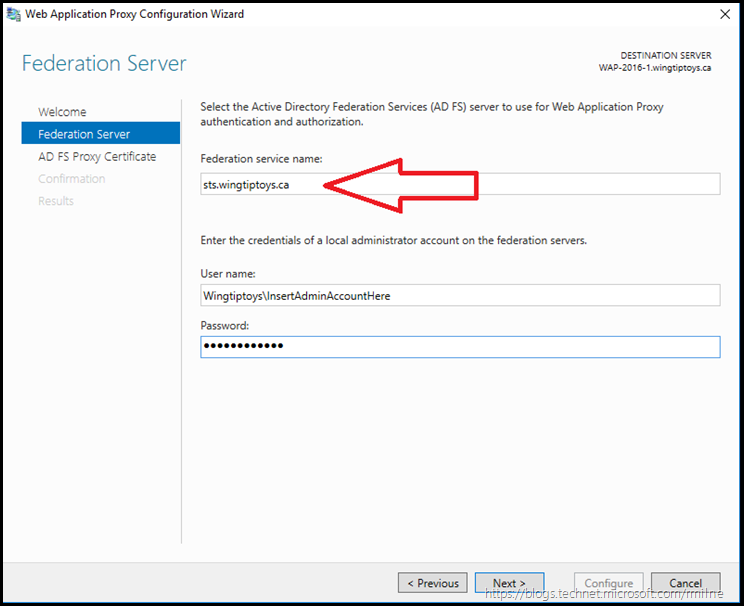
If you look closely at the AD FS properties, the federation service name is actually the FQDN of the service. In our case this is sts.wingtipyoys.ca so let’s enter that along with administrator credentials on the AD FS server so we are able to access AD FS.
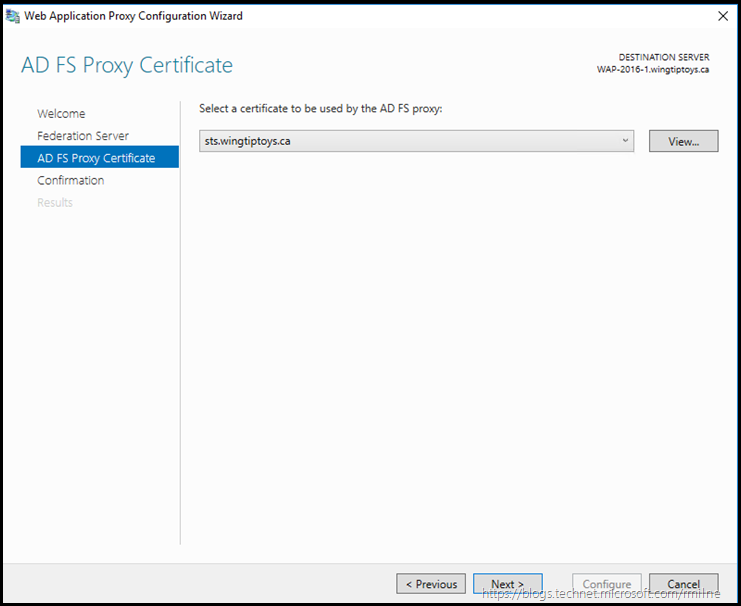
In the same way that we require a SSL certificate on the AD FS server, the same is true on the WAP as clients will establish SSL sessions to this machine. WAP will then us a SSL session to the internal AD FS server on TCP 443.
Since the certificate was previously installed and verified as part of the preparatory work, we select it and move on.
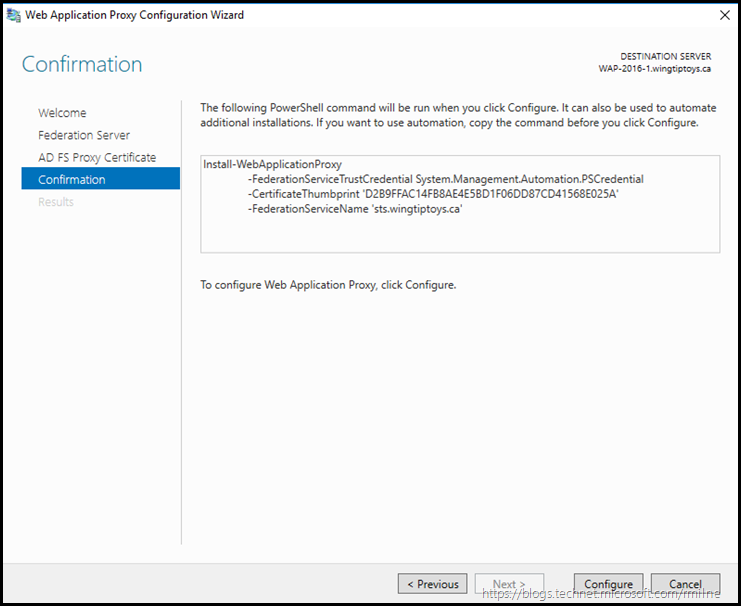
Verify the details, and click configure.
The wizard starts to configure the AD FS proxy
And shortly thereafter completes!
Installing Web Application Proxy Using PowerShell
In the vein as the graphical installation, there are two discrete tasks which are to be performed. The Remote Access role with with the Web Application Proxy service must first be installed, and then it can be configured.
Install Remote Access – Web Application Proxy
The below command will install the necessary OS components for the Remote Access role.
Install-WindowsFeature Web-Application-Proxy –IncludeManagementTools
Configure Web Application Proxy Using PowerShell
Once the OS components have been installed, they must be configured. Note that you require the correct certificate thumbprint, and the command will prompt for an account which has administrative permissions on the AD FS server.
Install-WebApplicationProxy –CertificateThumbprint 'D2B9FFAC14FB8AE4E5BD1F06DD87CD41568E025A' -FederationServiceName 'sts.wingtiptoys.ca'
Verifying AD FS Proxy Installation
At this time we should have a functional AD FS proxy server that is able to provide internet based users with access to our AD FS server’s authentication services. But as always, we need to test!
To open up the Remote Access management console, use the Remote Access Management shortcut in administrative tools.
If you have immediately launched this after installing the AD FS proxy it may take a few seconds or a refresh to show up. The other top tip is not to look for a published web app. Remember that WAP can be used to publish various applications to the internet, but in this case we are just wanting to use the base AD FS proxy components. No further configuration is required.
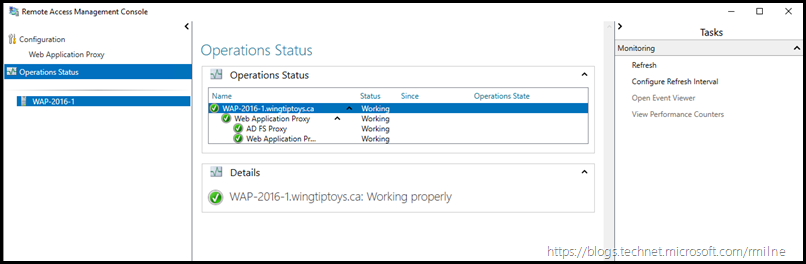
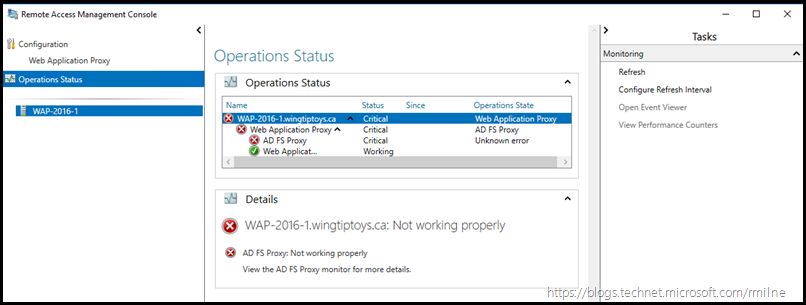
To check that the AD FS proxy is running, click onto the Operational Status in the left hand tree
Selecting the operational status, will then show how the AD FS proxy is currently running. You can also jump to Perfmon or Event Viewer from this node.
Should the AD FS proxy have an issue the console will light up like a Christmas tree. In this case I deliberately stopped the “Active Directory Federation Services” service on the AD FS proxy, please click to enlarge the image:
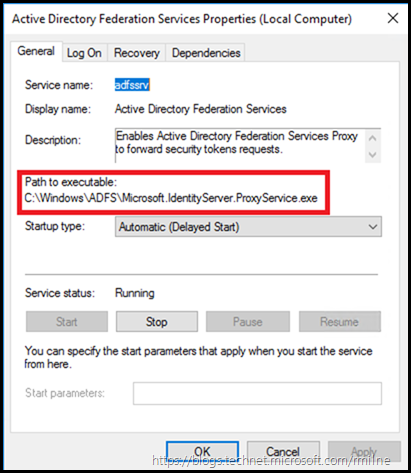
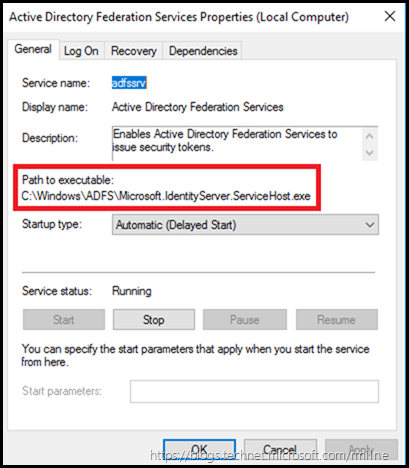
Even though the Windows service is name the same on both the AD FS server and the AD FS proxy, note that the executable path is different:
WAP
AD FS
Verify AD FS Proxy Configuration
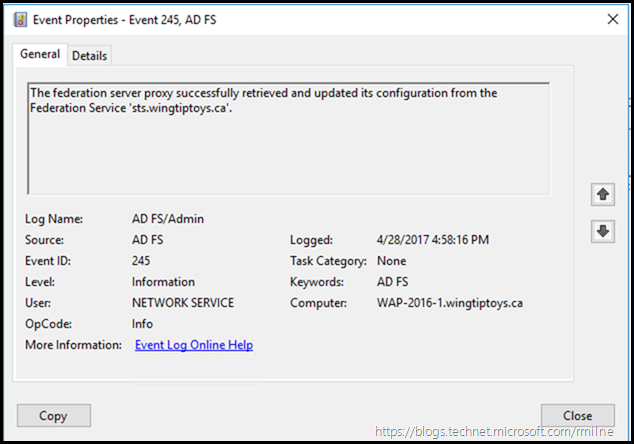
In event viewer on the AD FS proxy, open up the application and services logs and check that the proxy is able to retrieve it’s configuration from the AD FS server. This can be seen here, click to enlarge:
With the full EventID 245 details shown here:
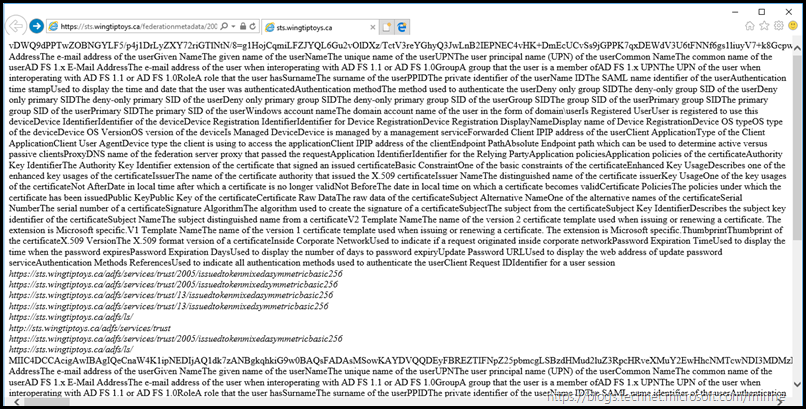
Verify Federation Service Metadata
Using the same URL as before, open Internet Explorer and navigate to your AD FS server’s federation metadata URL.
This will be something like the below, just change the FQDN to match your environment.
https://adfs.tailspintoys.ca/federationmetadata/2007-06/federationmetadata.xml
https://sts.wingtiptoys.ca/federationmetadata/2007-06/federationmetadata.xml
The intent here is to ensure that we are able to get to the site externally. If you are not able to see the AD FS text rendered in the browser, start with ensuring that the firewalls are not dropping traffic.
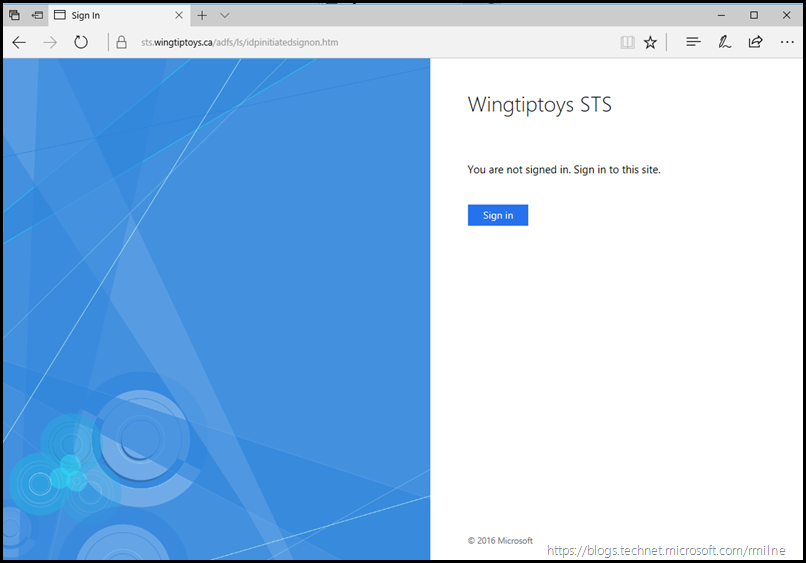
Verify AD FS Sign-In Page
Browse to the AD FS sign-in page and test that you are able to authenticate.
The URL will be similar to the below, again change the FQDN to match your organisation’s.
You should see the below, and be prompted to sign in:
(Note that I did not full screen the window before grabbing capture else it would be too small)
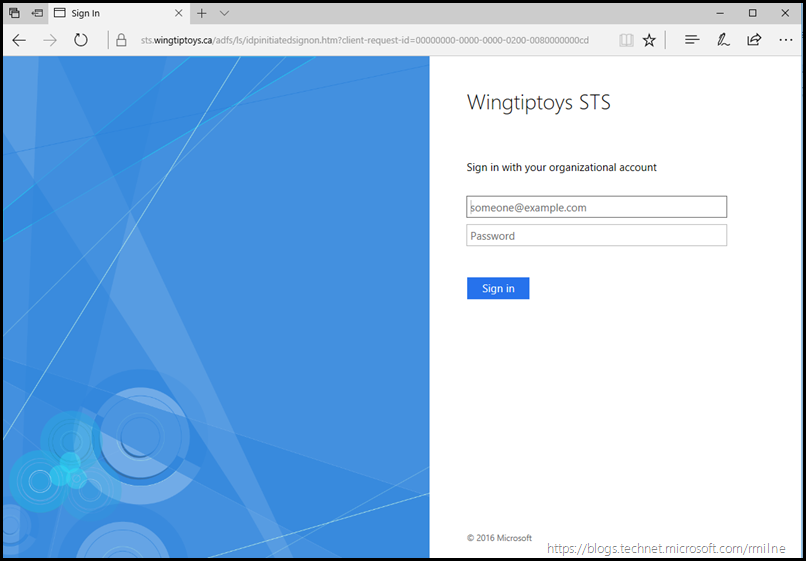
Clicking the Sign In button will prompt for credentials:
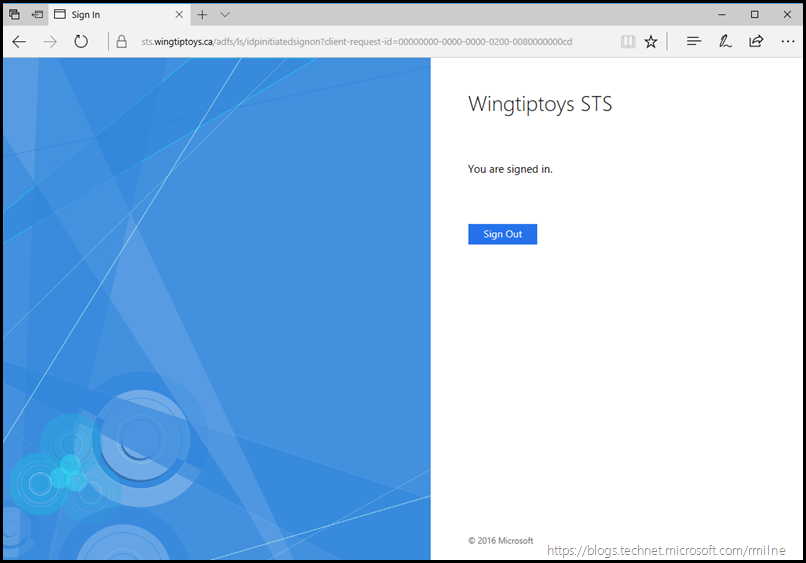
If you successfully authenticate then you will be rewarded with this stellar screen:
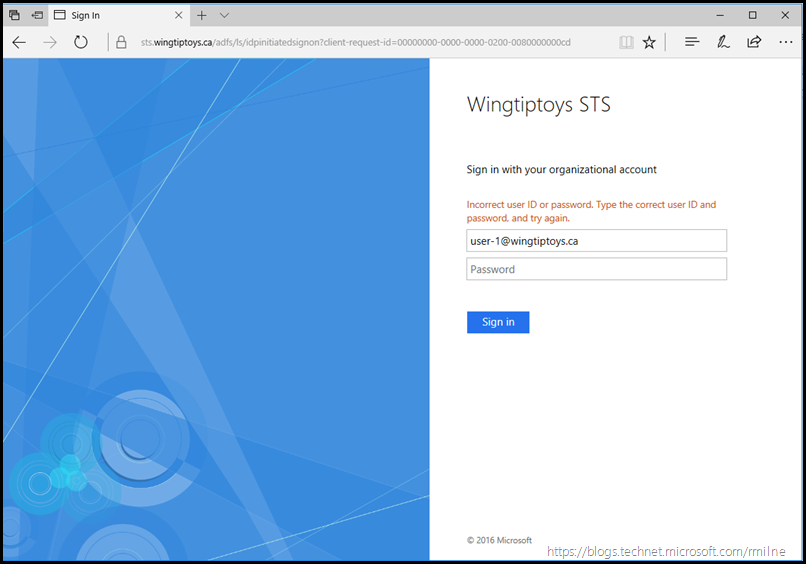
And if are unable to type a password (like me doing demos) then you will get this less than stellar result:
In part three we will complete the configuration, and instruct Office 365 to leverage the shiny AD FS infrastructure to authenticate users.
Cheers,
Rhoderick
* – Not having telnet client by default always grates. In the same way that explorer file options are always set to hide the good stuff like file extensions, system files and the ilk.