Endpoint security has always been a cornerstone of enterprise protection. Microsoft Defender for Endpoint (MDE) is the enterprise offering from Microsoft in this space. MDE is a leading solution for advanced threat detection and response. MDE is not a new product, it has already been in market for several years. You would have recognised it by the previous names Microsoft Advanced Threat Protection and Windows Defender Advanced Threat Protection (WDATP). These products are from 2016 and 2019 respectively.
The latest rebranding happened in 2020 at Ignite when the products below were unified under the Defender banner.
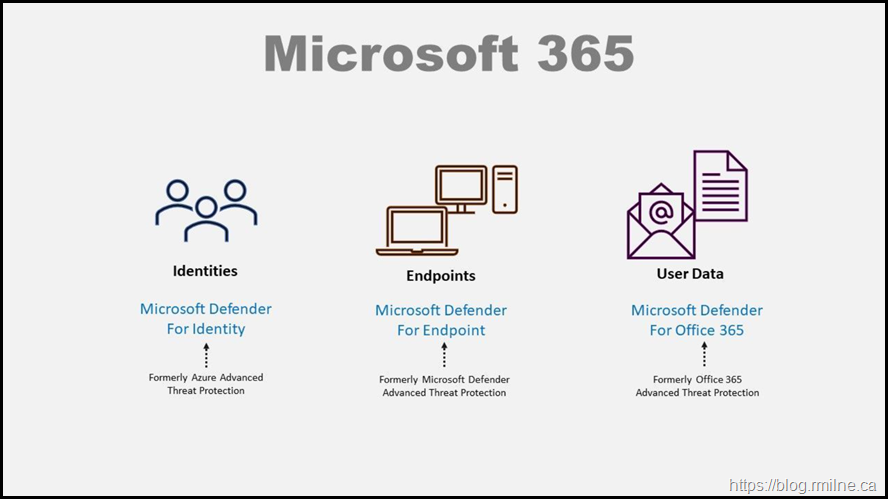
The product is now known ad Microsoft Defender for Endpoint or MDE. However, you will still see registry settings using the original ATP path. Marketing can sprinkle their rebranding pixie dust and change a splash screen, but having to re-write all of the internals is a much larger task. Good job that products don't get renamed all the time...
Initialising MDE
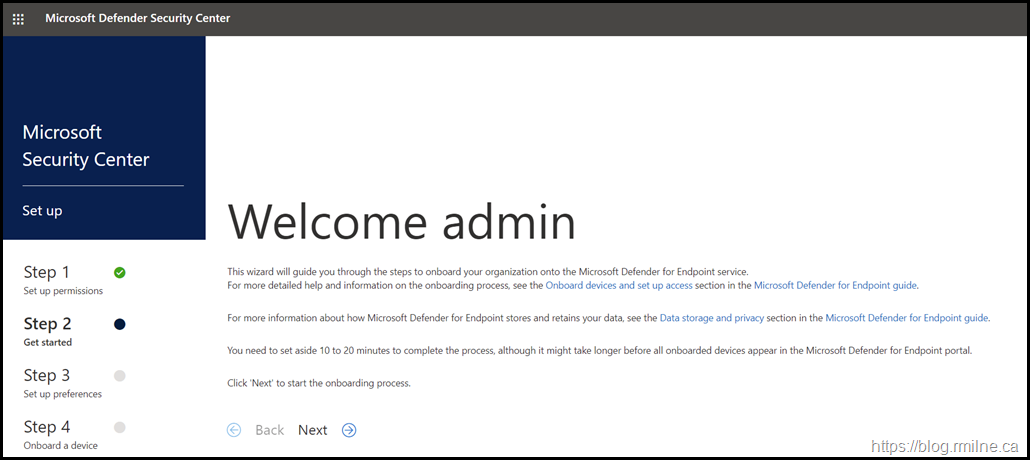
If we navigate to the Windows Security Center at https://securitycenter.windows.com/ the wizard will then guide us through the process of configuring the tenant for MDE. There are some important choices to be made!
For the search engines the text:
This wizard will guide you through the steps to onboard your organization onto the Microsoft Defender for Endpoint service.
For more detailed help and information on the onboarding process, see the Onboard devices and set up access section in the Microsoft Defender for Endpoint guide.
For more information about how Microsoft Defender for Endpoint stores and retains your data, see the Data storage and privacy section in the Microsoft Defender for Endpoint guide.
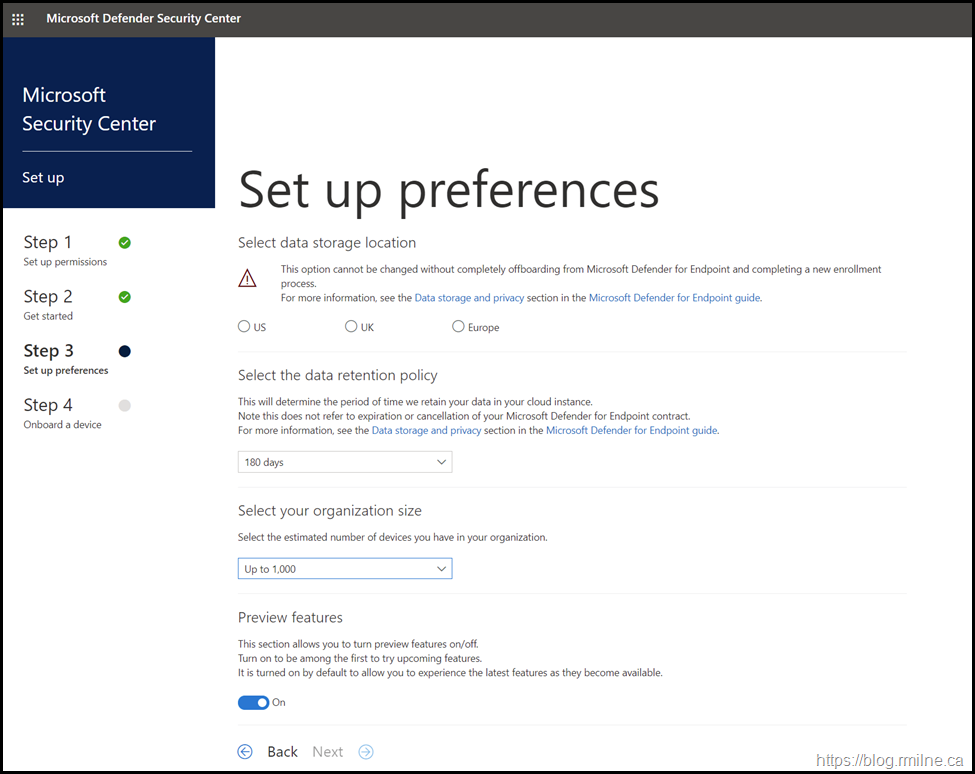
Note that you are asked to select the data storage location. You have three choices - US, UK and Europe.
Chose carefully - this can not be changed without completely tearing down MDE and rebuilding everything.
There is also the option to select the data retention policy. You can select from 60, 90 or180 days.
Update - this was removed in 2022 and the limit is now 180 days
Verbiage from the UI:
Select data storage location
This option cannot be changed without completely offboarding from Microsoft Defender for Endpoint and completing a new enrollment process.
For more information, see the Data storage and privacy section in the Microsoft Defender for Endpoint guide.
Select the data retention policy
This will determine the period of time we retain your data in your cloud instance.
Note this does not refer to expiration or cancellation of your Microsoft Defender for Endpoint contract.
For more information, see the Data storage and privacy section in the Microsoft Defender for Endpoint guide.
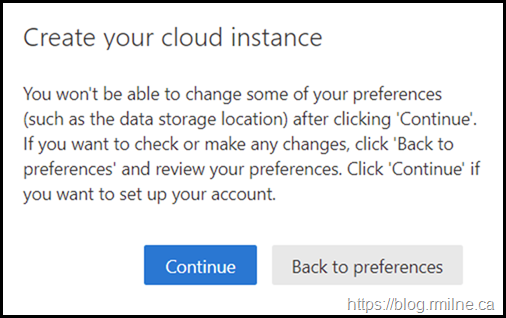
Confirm Choice
You will be prompted to confirm the choices made.
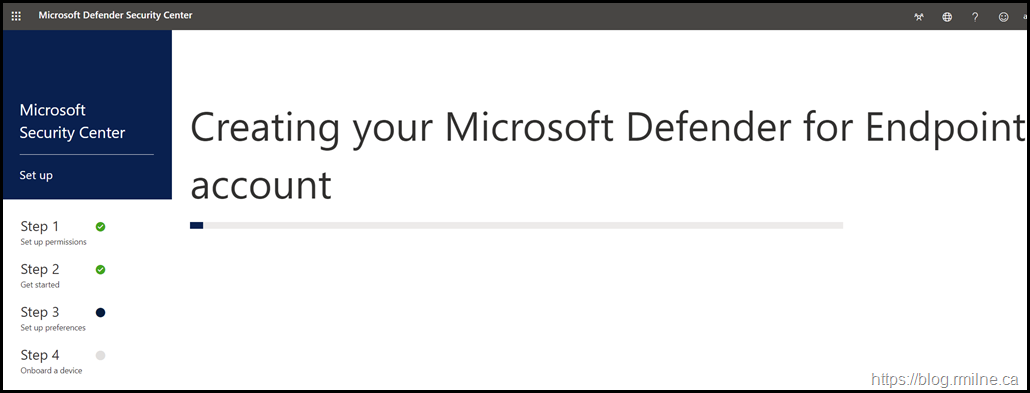
Once you are sure, click continue and then the MDE instance is created
Once the setup has completed, you can now onboard a device,
Note that are multiple options for onloading, they are covered in more detail below.
There are multiple onboarding methods:
If you click the drop down deployment methods, you will see the below:
-
-
Local Script Up to 10 devices
-
Group Policy
-
Microsoft Endpoint Configuration Manager current branch and later
-
System Center Configuration manager 2012, 2012 R2/ 1511/1602
-
Mobile Device Management / Microsoft Intune
-
VDI onboarding script for non-persistent devices
-
Note that the download package button reflects the choice made.
1 Onboard a device
First device onboarded: Incomplete
Onboard devices to Microsoft Defender for Endpoint using the onboarding configuration package that matches your preferred deployment method. For other device preparation instructions, read Onboard and set up.
You can configure a single device by running a script locally.
Note: This script has been optimized for usage with a limited number of devices (1-10). To deploy at scale, please see other deployment options above.
For more information on how to configure and monitor Microsoft Defender for Endpoint devices, see Configure devices using a local script section in the Microsoft Defender for Endpoint guide.
2 Group Policy
You can configure your devices using Group Policy.
For more information on how to configure and monitor Microsoft Defender for Endpoint devices see Configure devices using Group Policy section in the Microsoft Defender for Endpoint guide.
3 Microsoft Endpoint Configuration Manager current branch and later
Version 1606 and later of Microsoft Endpoint Configuration Manager provides an integrated console to deploy Microsoft Defender for Endpoint policies and monitor the Microsoft Defender for Endpoint agent health status.
For more information on how to configure and monitor Microsoft Defender for Endpoint devices, see Microsoft Defender for Endpoint section in the Microsoft Endpoint Configuration Manager guide.
4 System Center Configuration manager 2012, 2012 R2/ 1511/1602
You can use System Center Configuration Manager’s default policy functionality to configure and monitor your devices. This is supported in the following versions:
-
-
System Center 2012 Configuration Manager
-
-
-
System Center 2012 R2 Configuration Manager
-
-
-
System Center Configuration Manager (current branch) version 1511
-
-
-
System Center Configuration Manager (current branch) version 1602
-
For more information on how to configure and monitor Microsoft Defender for Endpoint devices, see Configure devices using System Center Configuration Manager section in the Microsoft Defender for Endpoint guide.
5 Mobile Device Management / Microsoft Intune
You can use Mobile Device Management solutions, such as Microsoft Intune to configure and monitor your devices.
For more information on how to configure and monitor Microsoft Defender for Endpoint devices, see Configure devices using Mobile Device Management tools section in the Microsoft Defender for Endpoint guide.
6 VDI onboarding script for non-persistent devices
Use the VDI onboarding scripts to onboard non-persistent virtual desktop infrastructure (VDI) devices. These scripts help overcome typical challenges associated with these devices:
-
-
Persistent device IDs for devices with the same device name
-
-
-
Instantaneous onboarding on initial startup
-
For more information about onboarding non-persistent VDI devices, see Onboard non-persistent VDI devices.
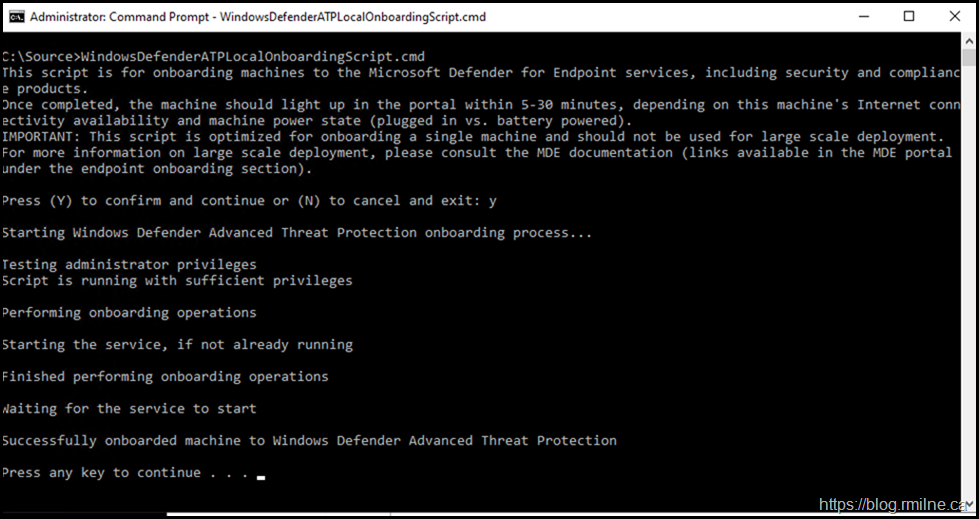
Example of Onboarding Using Local Script
The relevant download package was copied to the Windows 10 test machine.
Run as an elevated cmd prompt. Must have local admin permissions.
Now that the device is onboarded, there will be some interesting registry values to look at. For example:
OnboardingInfo Registry Value
The onboardingInfo stores the onboarding configuration data that tells the local Defender service how to communicate with the MDE cloud service. Created by the onboarding script, Intune policy, Group Policy, or local onboarding package (e.g., WindowsDefenderATPOnboardingScript.cmd). You should see a base64-encoded JSON blob or binary value representing onboarding metadata which includes:
- Tenant ID and service endpoints
- Environment (Commercial, GCC, GCC High, DoD, etc.)
- Reporting configuration
- Signature or certificate information used to authenticate to MDE backend
REG Query "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v OnboardingInfo
OnboardedInfo Registry Value
OnboardedInfo indicates the current state of the onboarding process . Whether the machine has successfully onboarded and is recognised by the MDE service. Created/updated by the Sense service after successful registration with the MDE online service. You can see the organisationID as part of this registry value.
REG Query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection" /v OnboardedInfo
Onboarding State Registry Value
This is a simple boolean flag. 1 = Onboarded. 0 = Not so much.
REG Query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" /v OnboardingState
Run a detection test
First device detection test: Incomplete
To verify that the device is properly onboarded and reporting to the service,run the detection script on the newly onboarded device:
-
-
Open a Command Prompt window
-
-
-
At the prompt, copy and run the command below. The Command Prompt window will close automatically.
-
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference= 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://127.0.0.1/1.exe', 'C:\\test-WDATP-test\\invoice.exe');Start-Process 'C:\\test-WDATP-test\\invoice.exe'
This is the same command, just with syntax highlighting. Double click to select the entire thing to copy and paste:
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference= 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('<a href="http://127.0.0.1/1.exe'">http://127.0.0.1/1.exe'</a>, 'C:\\test-WDATP-test\\invoice.exe');Start-Process 'C:\\test-WDATP-test\\invoice.exe'
After a brief wait:
Cheers,
Rhoderick