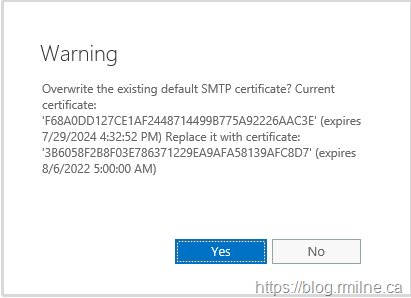
When adding a TLS certificate on an Exchange server, the inevitable prompt will appear to enquire if you wish to overwrite the default SMTP certificate binding. While the UI in the current versions of Exchange is slightly different, it was basically the same prompt in Exchange 2010 & Exchange 2007.
While the prompt language was the same in Exchange 2007 and newer versions, the way that transport deals with TLS certificates did change significantly in Exchange 2010. Exchange 2007 allowed only a single certificate to be bound to SMTP, and thus that certificate needed to have all of the required names. In Exchange 2010, the transport service became more intelligent and was able to determine which TLS certificate should be used based on the connection.
This process is documented for Exchange 2010 here.
The below flowchart illustrates the logic:
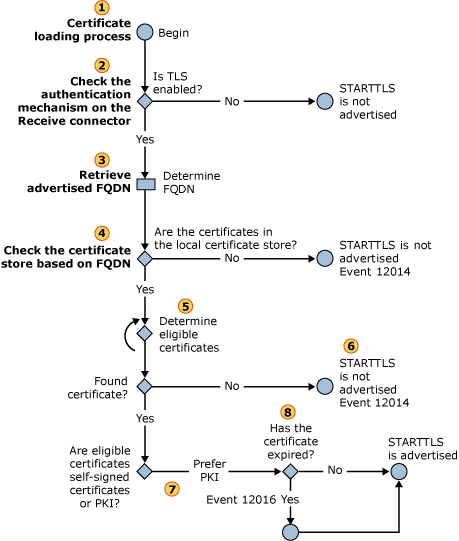
When an SMTP session is established, the receiving server initiates a certificate selection process to determine which certificate to use in the TLS negotiation. The sending server also performs a certificate selection process. For more information about that process, see Selection of Outbound Anonymous TLS Certificates. From this link, step 5 outlines some of the pertinent aspects of the certificate selection:
The certificate selection process searches for all certificates in the certificate store that have a matching FQDN. From this list, the certificate selection process identifies a list of eligible certificates. Eligible certificates must meet the following criteria:
- The certificate is an X.509 version 3 or a later version certificate.
- The certificate has an associated private key.
- The Subject or Subject Alternate Name fields contain the FQDN that was retrieved in step 3.
- The certificate is enabled for SSL/TLS use. Specifically, the SMTP service has been enabled for this certificate by using the Enable-ExchangeCertificate cmdlet.
In a nutshell, the fundamental difference with Exchange 2010 onwards is that multiple TLS certificates can be bound to SMTP
To Overwrite, Or Not Overwrite...
While the documentation says that there is typically no need to overwrite the default SMTP certification, I have noted that most customers actually do this as they click the default option which is to overwrite.
In most cases this does not cause issues as they are not using Edge servers for example. They also typically leave the additional SMTP binding so that transport can use both certificates.
My default preference is NOT to overwrite the default SMTP certificate.
Please note that CAS is separate from transport. The IIS binding will be changed from the default CAS configuration, as we do NOT want users to get certificate errors in Outlook.
Walkthrough of Prompts to Overwrite Default SMTP Certificate
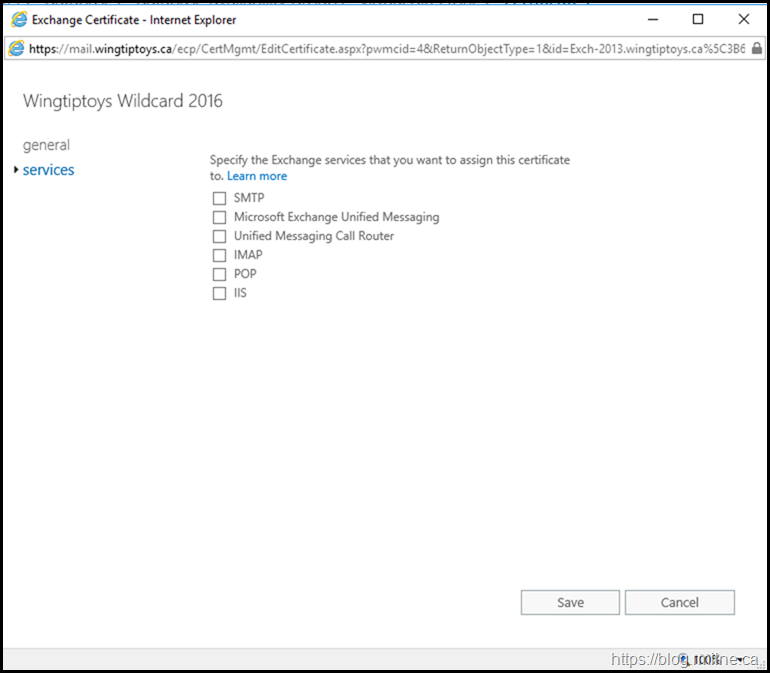
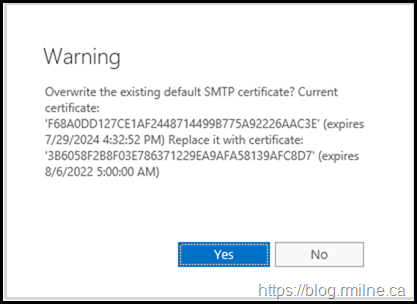
The below screenshots illustrate the UI shown when updating TLS certificate on Exchange.
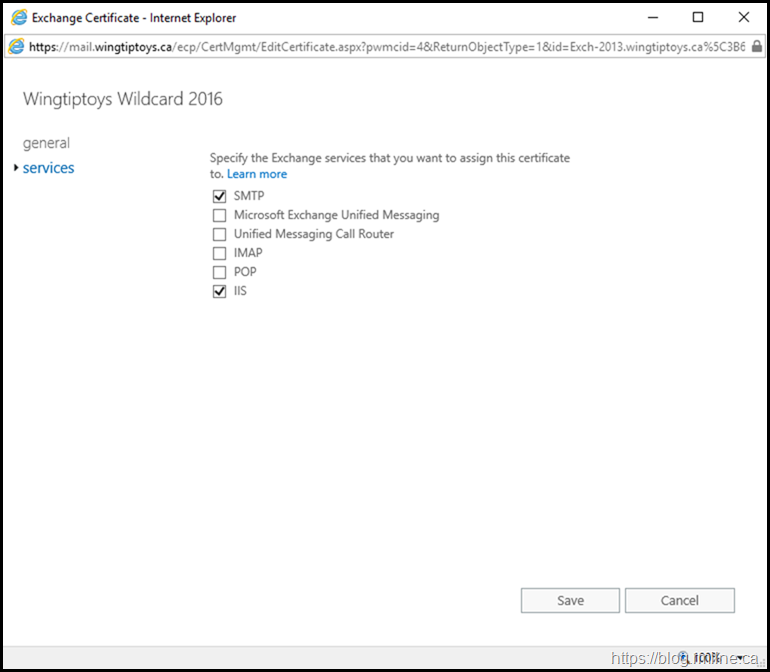
We then chose to bind the certificate to IIS and SMTP services by selecting their respective boxes.
Note that it is at this point we get the warning, and question if we want to overwrite the default SMTP certificate. There is no prompt for if were to choose only IIS as that follows the Highlander principle. *
Additional Consideration
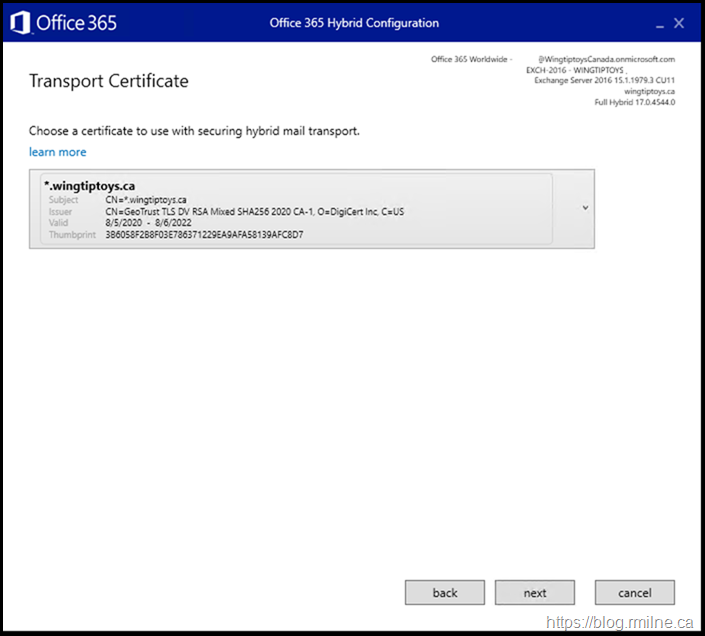
As an additional note, please note that we use a designated TLS certificate to encrypt cross-premises messages from Exchange to Exchange Online Protection.
If you have updated the on-premises SMTP certificate, please review your hybrid configuration as it is likely you will need to re-run the Hybrid Configuration Wizard (HCW).
As a reminder, the below is what you will see when running the HCW and are prompted to choose the TLS certificate.
Cheers,
Rhoderick
* There can be only one!
Hi Rhoderick,
Thanks for the post. One scenario not mentioned where I think it makes sense to overwrite the default is when you renew the self-signed certificate (the original default). Would you agree? If not, can you shed any light on the why?
Thanks in advance.
Hi Jeremy,
For that scenario, yes I would overwrite.
When done, then I would also remove the old expired cert as well.
Cheers,
Rhoderick
Good day, Rhoderick.
Like some of your customers, I overwritten default SMTP certificate, while renewing the public certificate in my Exchange 2016 environment. Is there a way to restore the original setting? By default it is a Microsoft Exchange self-signed certificate that is being used for SMTP, correct?
Thank you.
Easiest way is to create a new self signed cert by pipeline the current on you have, then assign SMTP services to the new self signed cert and say "YES" and then you can delete the old self signed cert.
https://learn.microsoft.com/en-us/exchange/architecture/client-access/renew-certificates?view=exchserver-2019#use-the-exchange-management-shell-to-renew-an-exchange-self-signed-certificate
Hi Rhoderick, as a "backup" connectivity protocol I need to enable IMAP for my roaming users.
The official procedure (https://learn.microsoft.com/en-us/exchange/clients/pop3-and-imap4/configure-imap4?view=exchserver-2016) consists of:
- to enable imap services
- set imap settings (fqdn and connectivity bindings/protocols)
- Configure the authenticated SMTP settings for internal and external clients, since when you enable imap to read emails you must also have a valid smtp server to be able to send emails as well. This step consists of overwriting the default Exchange self-signed certificate.
What you write in your article apparently constrasts with what is being said in the MS article regarding the overwriting the smtp certificate. My guess is that I should replace the default Exchange self-signed certificate for my goal, otherwise the subject name in the certificate does not match the dns name set in the imap settings.
But I am concerned about the fact that the default Exchange self-signed certificate is also used to encrypt SMTP communication between internal Exchange servers.
Is not that, by repalcing the default Exchange self-signed certificate, something gets broken? Is the official MS procedure linked above safe or is there something that should I be made aware of before continuing this way?
Thank you,
Francesco
Hi Francesco,
Are you referring to this bit?
Although you can use a separate certificate for IMAP4, we recommend that you use the same certificate as the other Exchange IIS (HTTP) services, which is likely a wildcard certificate or a subject alternative name (SAN) certificate from a commercial certification authority that's automatically trusted by all clients. For more information, see Certificate requirements for Exchange services.
You can have the namespace used for the IMAP namespace in that SAN cert, or it can be on a separate cert. Ideally all of your CAS namespaces are on a single cert, but that is still separate from overwriting the default SMTP cert that is bound to SMTP.
The overwriting consideration is due to issues I've had with Edge subscriptions etc.
Cheers,
Rhoderick
Hello Rhoderick,
We have both default certificates (Microsoft Exchange Server Auth Certificate and Microsoft Exchange) plus our own Digicert wildcard certificate assigned to SMTP. We have a single customer who when we try to email, the emails sit in the outbound queue with a 454 4.7.0 Invalid client certificate error. Could this any way be caused by TLS selecting one of the default certificates for encryption versus our wildcard? Running on-prem Exchange 2016. Thanks!
I have seen this with folks that overwrote one or more Exchange mailbox servers with 3rd party certificate and the next hop is Edge. This is another reason I tell every customer to never replace the default internal transport certificate... plus it gives you 5 years instead of the 1 year standard we see today. I would have your customer rebuild the Edge Subscription and that should do the trick if Edge was next hop. If not turn on verbose logging for your send connectors to see your target and thumbprint that the TLS negation is failing on.
Hello Rhoderick
I'm looking for a way to check for default SMTP certificate on the Edge servers.Nobody has any info on that.
I found how to check for default SMTP certificate on the mailbox servers as they do live in AD, but Edge servers do not
below is a sample code for mailboxservers, but nothing for Edge servers
DO you know how to check for this inforrmation on Edge servers?
$ExchangeServers = (Get-ExchangeServer |Where-Object {$_.ServerRole -like "mailbox"} )| Select-Object Name,DistinguishedName
$Results = @()
#Process Information
ForEach($Server in $ExchangeServers){
$TransportCert = (Get-ADObject -Identity $Server.DistinguishedName -Properties *).msExchServerInternalTLSCert
$Cert = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2
$CertBlob = [System.Convert]::ToBase64String($TransportCert)
$Cert.Import([Convert]::FromBase64String($CertBlob))
$server | Add-Member -MemberType NoteProperty -Name DefaultTLSCertSubject -Value $Cert.Subject
$server | Add-Member -MemberType NoteProperty -Name DefaultTLSCertFriendlyName -Value $Cert.FriendlyName
$server | Add-Member -MemberType NoteProperty -Name DefaultTLSCertThumbprint -Value $Cert.Thumbprint
$server | Add-Member -MemberType NoteProperty -Name DefaultTLSCertExpireDate -Value $Cert.NotAfter
$Results += $Server
}
#Show result
#$Results | Out-GridView
$Results
Hi Rhoderick!
I sucessfully installed a Letsencrypt certificate on my Exchange 2019 with automated win-acme app. I can see the certificate in EAC. I then tried to assign the Exchange services IIS and SMTP to the new cert. The overwriting question I answer with "yes". But this only works for IIS service, not for SMTP, it remains unticked. There is absolutly no error message. I also tried it via powershell, but same result. Any ideo how to overcome this?
Thanks and regards,
Stefano
I'd split this into two questions.
1 - is the new cert enabled for SMTP
2 - can it be enabled
Wondering exactly what type of cert this is. Can you share?
Cheers,
Rhoderick
Hi,
Thanks for helping!
1 - during certificate creation process with win-acme client you specify a script with parameters IIS and SMTP
2 - not sure what you mean with "enabled"; on my old exchange 2012 I had nothing to do after creating the certificate with win-acme client, it just worked
3 - also not sure, sorry. I never had to specify within the win-acme client, what type of cert I need. In the properties of the certificate on the old (working) server it says "client authentication" and "server authentication". Does that help?
One additional finding which could be a clue: On the old server (still productive) it says in MMC "cannot export private key, because it is not marked as exportable"; in the new server it says "private key not found". Why is that? Could it be that letsencrypt does deliver a private key only one time and that I have to import it from the old server myself?
Thanks again for your help!
I'd spend a bit of time reading the Exchange docs about how we manage the certs. You must enable the certificate for Exchange, and that happens *after* you install it. The ACME tool hides that from you, but it's in their Exchange V2 script (I took a look).
Something went wrong with the certificate creation on this server. You *must* have a private key, else that cert is useless for what Exchange & IIS needs. Revist that part, get it fixed and the rest should work
Cheers,
Rhoderick