Active Directory Federation Services (AD FS) uses endpoints to provide access to features. There are a series of different endpoints which each serve a different purpose from password reset, publishing federation metadata or multiple web services protocols. It is important to ensure that only the required features are actually enabled, and also if those features are to be made available internally only, or to the Internet. Not all endpoints should be published to the Internet.
While a new AD FS install will roll out with a defaul configuration, that does not necessarily mean it is as secure as it can be. Microsoft does document the minimum endpoints that are required for Azure AD and Office 365 integration. For 3rd party applications etc, please check with the respective vendor for their requirements.
One of the common security issues is with the WSTrust endpoints. One of them is enabled by default on the Web Application Proxy (WAP).
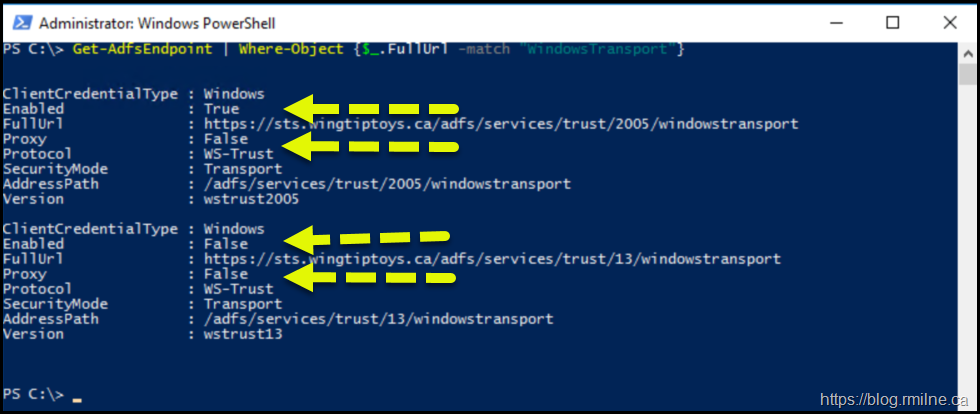
We can check this quickly using Windows PowerShell locally on the AD FS server.
Get-AdfsEndpoint | Where-Object {$_.FullUrl -match "WindowsTransport"}
Disable WS-Trust Endpoints on WAP
The commands below will disable WS-Trust endpoints on the WAP servers, i.e. from the Internet. This can be done whilst leaving them enabled internally.
Note that you run the commands on AD FS. That is because the WAP configuration is stored within AD FS and it's database.
Set-AdfsEndpoint -TargetAddressPath /adfs/services/trust/2005/windowstransport -Proxy $False
Set-AdfsEndpoint -TargetAddressPath /adfs/services/trust/13/windowstransport -Proxy $False
Note that if you use the default Windows Internal Database (WID), the Federation service will need to be restarted on all servers in the farm. This synchronisation is done using TCP 80 and you can check the last sync time on a secondary farm server using PowerShell
Get-AdfsSyncProperties
Cheers,
Rhoderick