The November 8, 2022 and later Windows updates address a security bypass and elevation of privilege vulnerability with Authentication Negotiation by using weak RC4-HMAC negotiation.
This update will set AES as the default encryption type for session keys on accounts that are not marked with a default encryption type already.
To help secure your environment, install the Windows update that is dated November 8, 2022 or a later Windows update to all devices, including domain controllers
These Windows updates contain updates to the Kerberos protocol, to help with recent security issues. For example:
This was a planned change. Information was published to help admins manage this and subsequent changes as further work is required for Kerberos. You can review those details in articles like:
KB5021131: How to manage the Kerberos protocol changes related to CVE-2022-37966
You can read the articles for the full details, but the high level summary to help protect your environment and prevent outages, we recommend that you do the following steps:
-
UPDATE your Windows domain controllers with a Windows update released on or after November 8, 2022.
-
MOVE your Windows domain controllers to Audit mode by using the Registry Key setting section.
-
MONITOR events filed during Audit mode to secure your environment.
-
ENABLE Enforcement mode to address CVE-2022-37967 in your environment
However there were some issues, and this post will note the issues experienced in the field plus an additional problem that that was observed with an AD FS server.
Update: 10-1-2023 The OOB fix noted below is present in the updates releated this month. Please see this release announcement.
Unplanned Impact
Please take the time to read through this post How Do I Know If My AD Environment Is Impacted By The November 8th 2022 Patch? as it provides a good overview of the issue. An Out Of Band (OOB) update was released to deal with the issue introduced by the 8th November 2022 update.
Microsoft is releasing Out-of-band (OOB) updates today, November 17, 2022 and November 18, 2022 for installation on all the Domain Controllers (DCs) in affected environments. This update addresses a known issue which might cause sign in failures or other Kerberos authentication issues. You do not need to install any update or make any changes to other servers or client devices in your environment to resolve this issue. If you used any workaround or mitigations for this issue, they are no longer needed, and we recommend you remove them.
Out of Band Updates
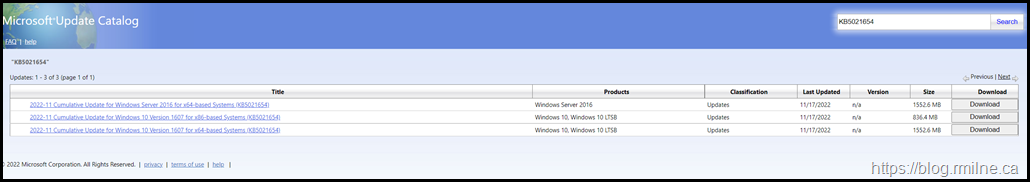
The Out Of Band updates can be manually downloaded from the Microsoft Update Catalog.
The relevant download links are:
Windows Server 2022 KB5021656
Windows Server 2019 KB5021655
Windows Server 2016 KB5021654
Windows Server 2012 R2 KB5021653
Windows Server 2012 KB5021652
Resources
If you are reading this as a result of issues with the November 2022 update. There are a number of resources on the Internet. Some examples are below.
Steve Syfuhs is senior dev on the Windows team at Microsoft and has some truly outstanding content on his blog. He has a post specifically on this issue Kerberos Event ID 27 (syfuhs.net) and the comments at the end also deserve a read.
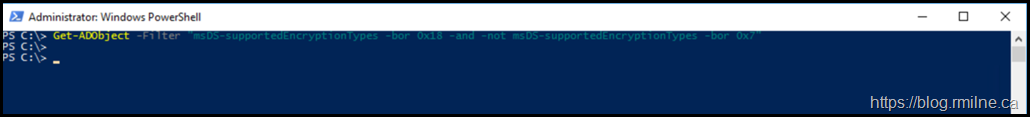
Some posts and articles have sample queries you can run to find objects in AD DS that may have an issue. For example this PowerShell oneliner is in the known issues section of the how to manage the Kerberos protocol change KB article.
Get-ADObject -Filter "msDS-supportedEncryptionTypes -bor 0x18 -and -not msDS-supportedEncryptionTypes -bor 0x7"
The How Do I Know If My AD Environment Is Impacted By The November 8th 2022 Patch has the below PowerShell excerpt:
Get-ADObject -Filter * -Properties msDS-SupportedEncryptionTypes | `
select name,objectClass,'msDS-SupportedEncryptionTypes', @{N='EncryptionTypes';E={Get-ETypeDefinition -msDSSupportedEncryptionTypes ($_.'msDS-SupportedEncryptionTypes')}}, @{N='EncryptionTypesAsString';E={Get-ETypeDefinition -msDSSupportedEncryptionTypes ($_.'msDS-SupportedEncryptionTypes') -AsString}} | `
select name,objectClass,EncryptionTypes,@{N='HasRC4OrIsBlank';E={$_.EncryptionTypesAsString -like "*RC4*"}} | `
Where{-not $_.HasRC4OrIsBlank}
Interestingly the above did not help with the situation below.
Additional Kerberos Issue Post November 2022 OOB Update
This was an additional issue which persisted even after applying the OOB update. The issue is reproduced below for your viewing pleasure.
The initial symptom was that AD FS authentication failed.
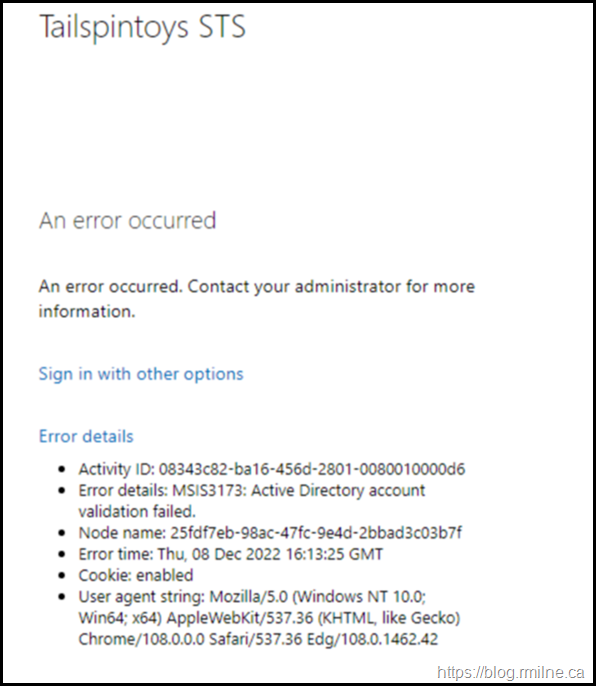
If we look at the error details, there is some interesting additional information.
The full Error details: MSIS3173: Active Directory account validation failed.
There are no meaningful errors on the client. Let’s go check the DCs .
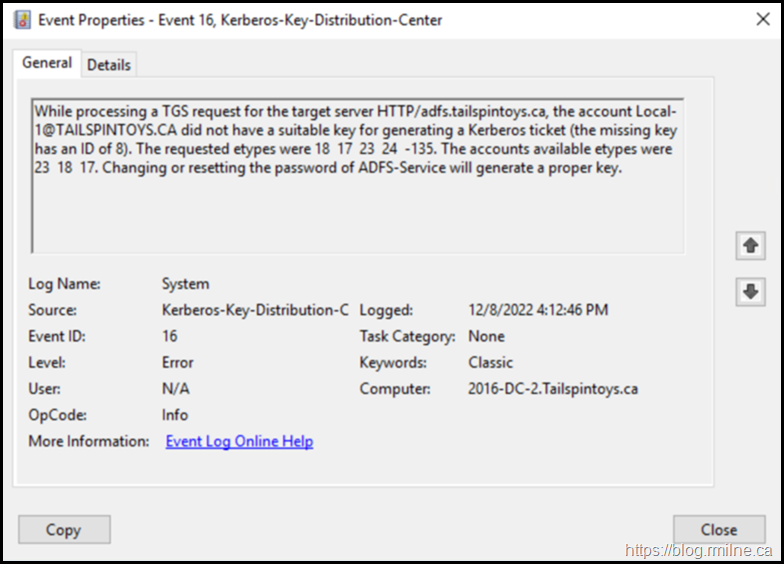
In the DC's system event log we can see that EventID 16 is present stating that there is a Kerberos issue with the AD FS service account.
The full EventID text:
While processing a TGS request for the target server HTTP/adfs.tailspintoys.ca, the account Local-1@TAILSPINTOYS.CA did not have a suitable key for generating a Kerberos ticket (the missing key has an ID of 8). The requested etypes were 18 17 23 24 -135. The accounts available etypes were 23 18 17. Changing or resetting the password of ADFS-Service will generate a proper key.
All other authentication scenarios were fine after the OOB update. Only AD FS had an issue.
What’s wrong with the AD FS service account?
AD FS Service Account Details
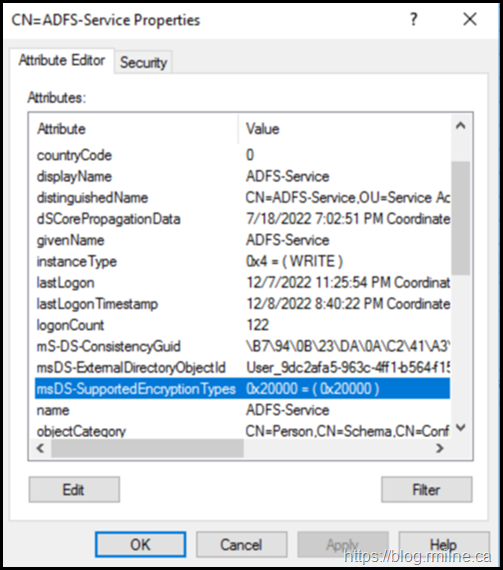
If we take a look at the ADFS-Service Account in AD DS using ADSIEdit, the msDS-SUpportedEncryptionTypes has an unexpected value of 0x2000 in hexadecimal.
As you can see msDS-SupportedEncryptionTypes - has a value of 0x2000.
This is hexadecimal which is 131072 decimal. Or 0010 0000 0000 0000 0000 in binary.
Good luck trying to find that in official documenation of all the supported values [MS-KILE]: Supported Encryption Types Bit Flags | Microsoft Learn
This is an example where the cusomer at some point in the past added this value, but the reason is lost in the mist of time.
When the value was cleared and the AD FS service restarted the issue was resolved.
Provided Scripts Checking For msDS-SupportedEncryptionTypes
If we use the two provided PowerShell excerpts from earlier in this post to help scan for potential account misconfigurations, they do not catch the value present in the environment.
Checking For Unexpected msDS-SupportedEncryptionTypes Values
As you saw above, the provided PowerShell code did not find the the misconfiguration as it was so unexpected. If we do want to check the values in PowerShell there are a few options.
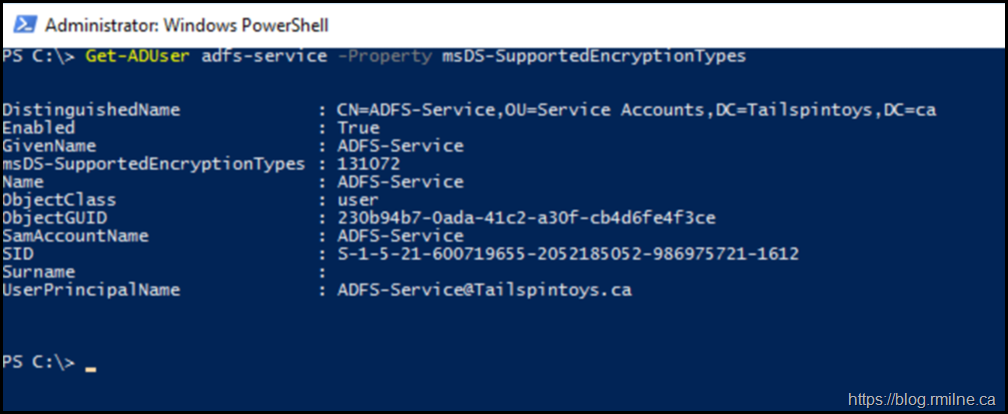
A simple check for a single account could be done like this:
Get-ADUser adfs-service -Property msDS-SupportedEncryptionTypes
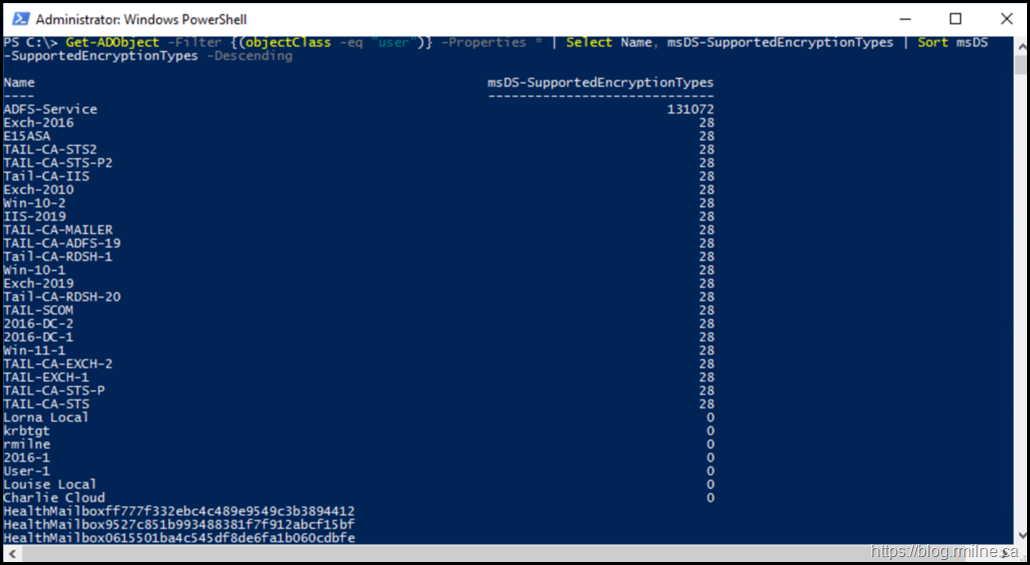
I settled on the below for checking all of the accounts. The output order was sorted to help sift through all of the accounts. You could also export this to Excel if needed. The sort order helps expose the outliers.
Get-ADObject -Filter {(objectClass -eq "user")} -Properties * | Select Name, msDS-SupportedEncryptionTypes | Sort msDS
-SupportedEncryptionTypes –Descending
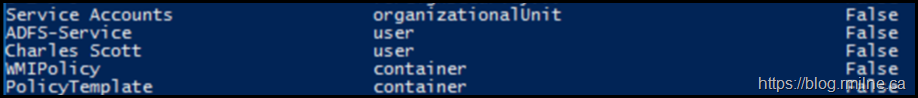
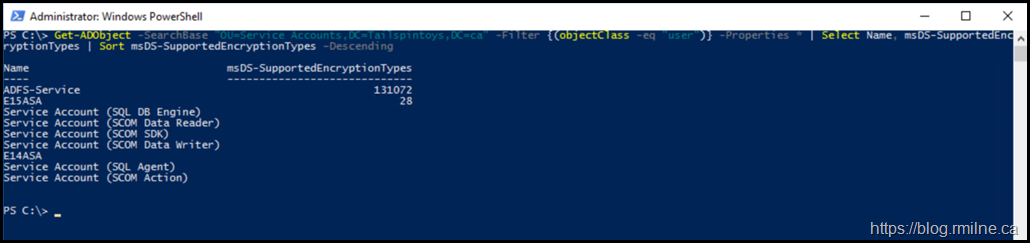
We could further refine the query to a particular portion of the directory with the below example where it scopes the searchbase.
Get-ADObject -SearchBase "OU=Service Accounts,DC=Tailspintoys,DC=ca" -Filter {(objectClass -eq "user")} -Properties * | Select Name, msDS-SupportedEncryptionTypes | Sort msDS-SupportedEncryptionTypes –Descending
Additional Resources
Steve's blog was aready mentioned, but he is also active on Twitter. Well worth following him!
Steve Syfuhs (@SteveSyfuhs) / Twitter
He has also discussed another note around EventID 27.
And his blog again: Steve on Security | Theoretical Headbanging (syfuhs.net)
Jerry Devore wrote a great article on Decrypting the Selection of Supported Kerberos Encryption Types
Cheers,
Rhoderick