Azure AD Self Service Password Reset (SSPR) has the ability to restrict which group of users are able to perform SSPR tasks. It is a slightly limited administrator control as only a single group can be selected. Azure AD administrator roles are able to perform SSPR even if they are not in scope of the selected group.
They typical user experience is that the person goes to https://aka.ms/SSPR and completes the SSPR process. Note that they should have completed registration prior to this. They also really should be forced to perform MFA rather than rely on generic security questions.
The high level overview of this process is here:
Let users reset their own passwords - Microsoft 365 admin | Microsoft Learn
Example Lab Configuration
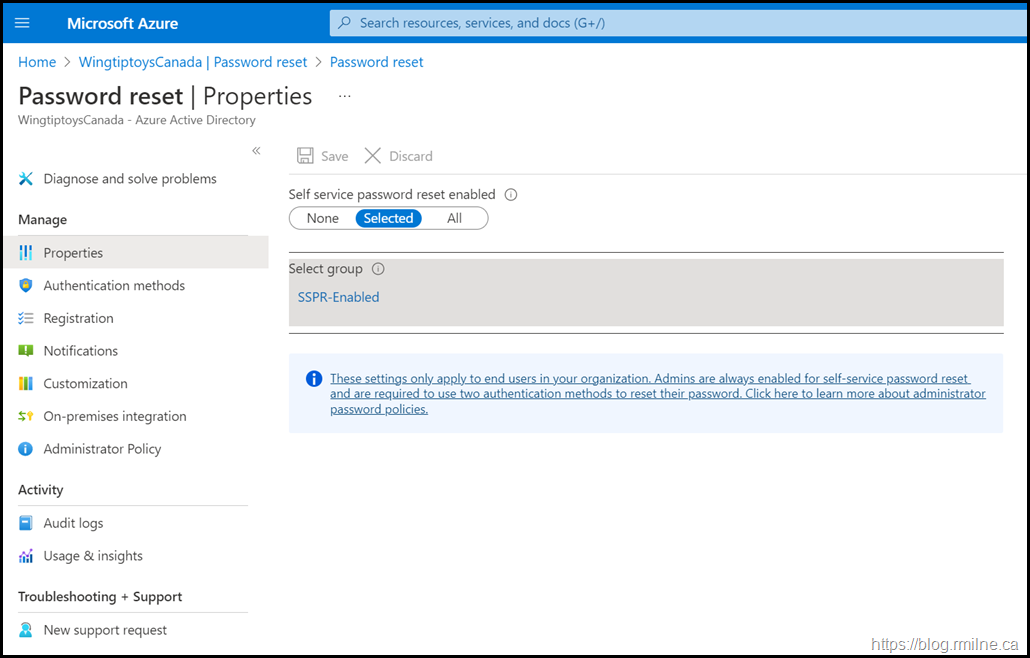
Below is the SSPR configuration in the wingtiptoys.ca environment.
Note that there is the option to select just a single group, and there is also the note that admins are always enabled for SSPR.
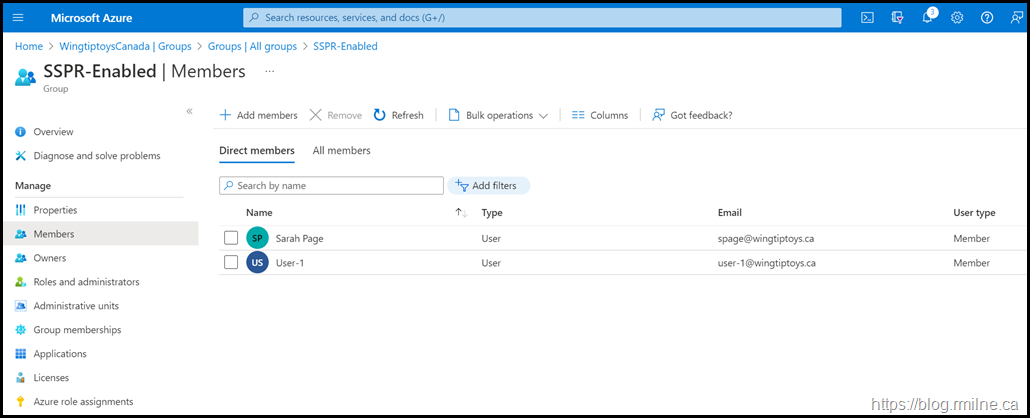
There are a limited number of users actually in the SSPR-Enabled Azure AD group as we want to test the user experience for a person that is NOT in scope of SSPR.
The account that we will use later is called Darren Gibb and as you can see they are not in the group below.
Attempting to Use SSPR With Synchronised Excluded Account
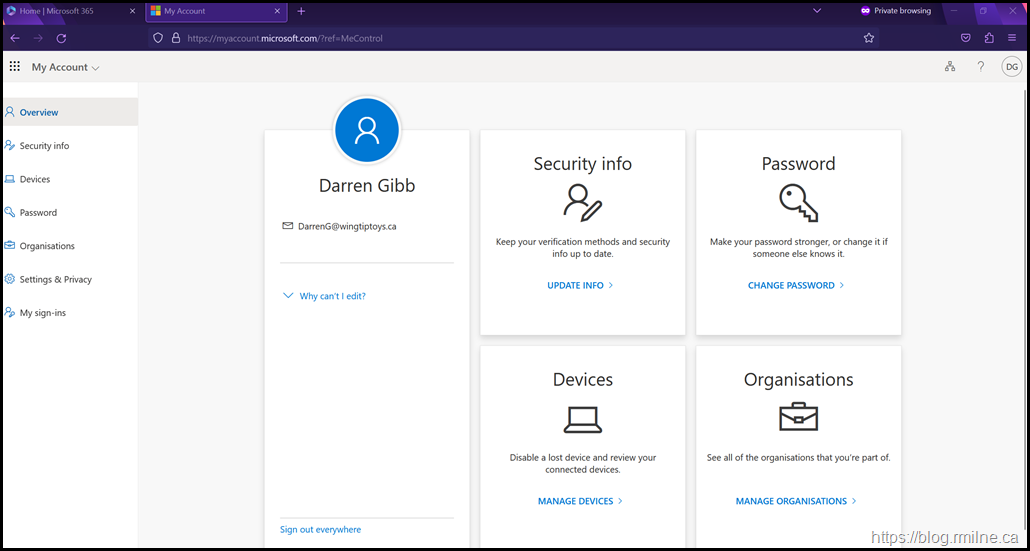
Below we are signed-in as Darren. This is an on-premises AD account that is synchronised to Azure AD using Azure AD Connect.
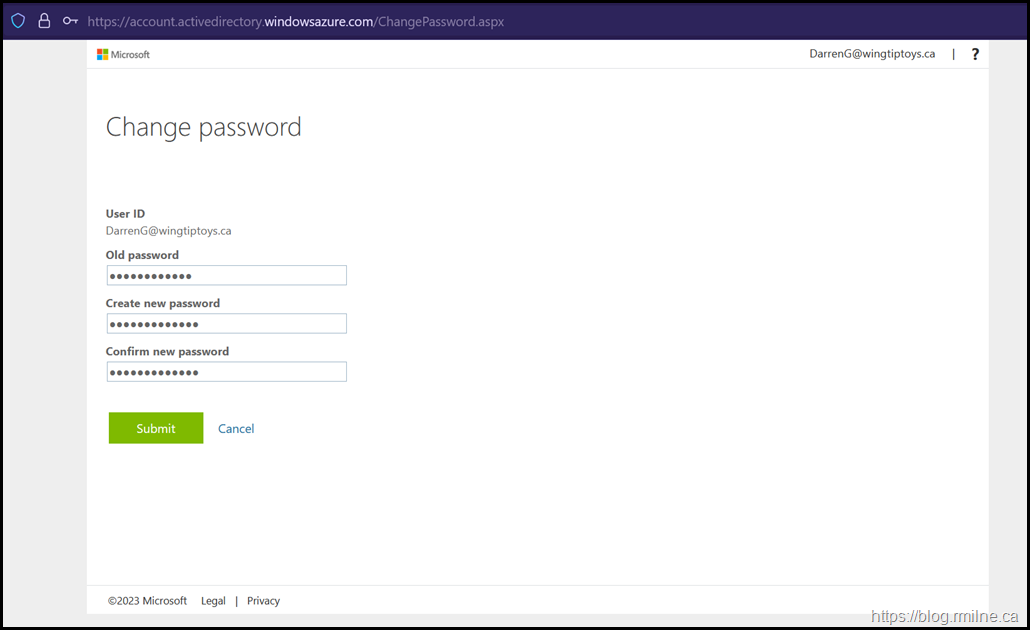
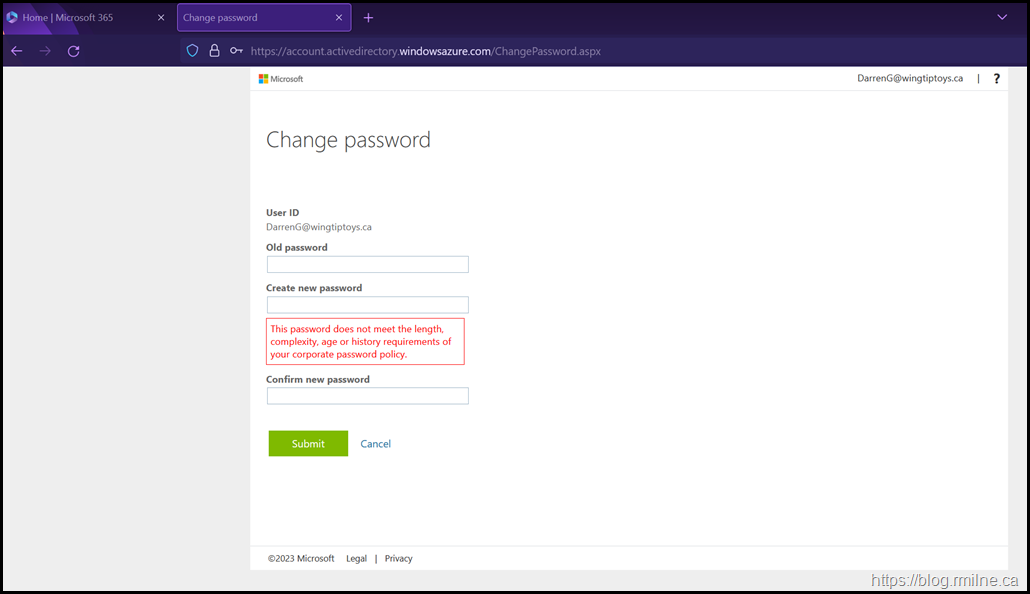
If they click the Change Password or use the shortcut URL they will be taken to the SSPR page.
https://account.activedirectory.windowsazure.com/ChangePassword.aspx
They enter the correct current password. Then a new password that does meet policy requirements is entered.
So far so good. But...
But...
Then they run into an issue and get the error message that:
This password does not meet the length, complexity, age or history requirements of your corporate password policy.
What The Azure AD Connect Server Saw
Since this is an on-premises account, the flow is for the password to be reset on-premises and if that was done sucessfullythen the reset password will be synchronised to Azure AD.
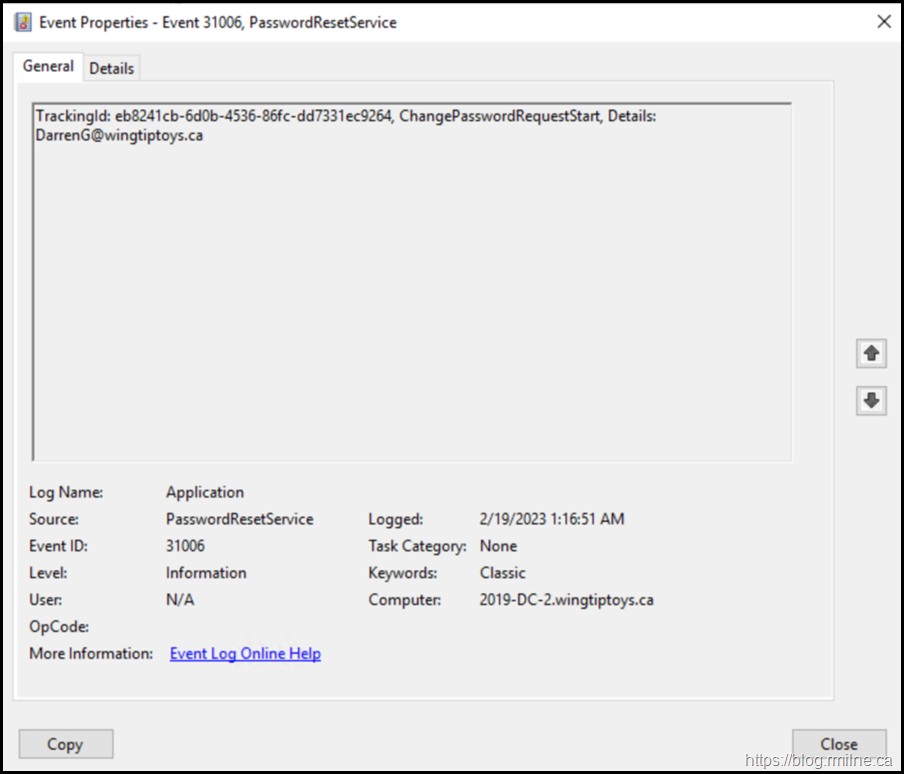
Azure AD Connect is unable to synchronise the reset password. In the server's Application EventLog you will find EventID 31006 and 33008. Both of which have a source of PasswordResetService.
Examples of these EventIDs are shown below.
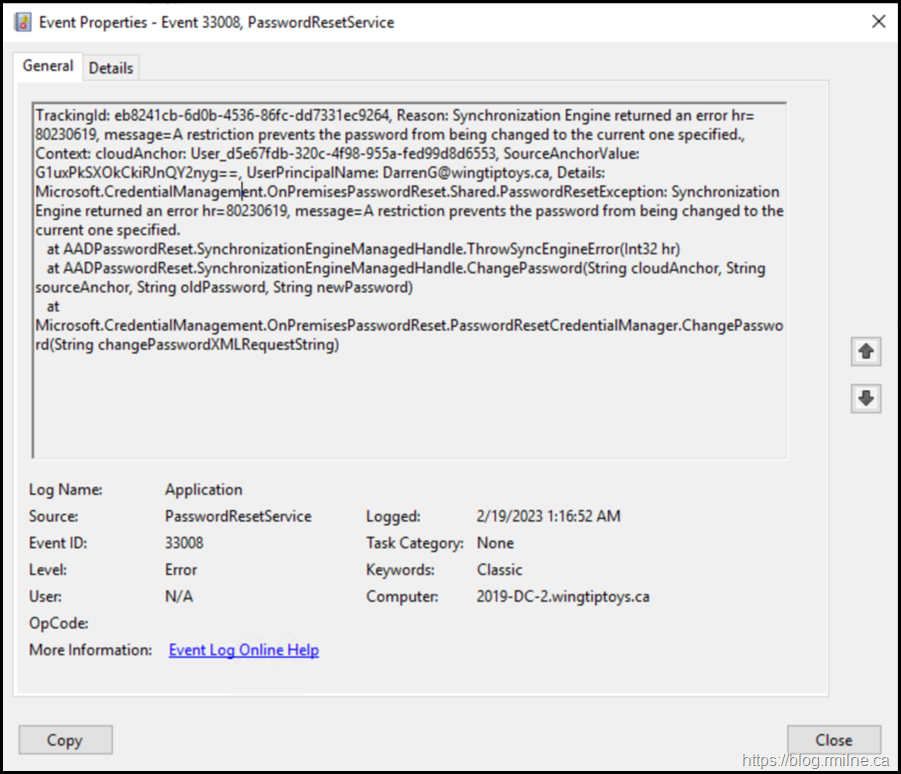
Full error text for the search engines:
TrackingId: eb8241cb-6d0b-4536-86fc-dd7331ec9264, Reason: Synchronization Engine returned an error hr=80230619, message=A restriction prevents the password from being changed to the current one specified., Context: cloudAnchor: User_d5e67fdb-320c-4f98-955a-fed99d8d6553, SourceAnchorValue: G1uxPkSXOkCkiRJnQY2nyg==, UserPrincipalName: DarrenG@wingtiptoys.ca, Details: Microsoft.CredentialManagement.OnPremisesPasswordReset.Shared.PasswordResetException: Synchronization Engine returned an error hr=80230619, message=A restriction prevents the password from being changed to the current one specified. at AADPasswordReset.SynchronizationEngineManagedHandle.ThrowSyncEngineError(Int32 hr) at AADPasswordReset.SynchronizationEngineManagedHandle.ChangePassword(String cloudAnchor, String sourceAnchor, String oldPassword, String newPassword) at Microsoft.CredentialManagement.OnPremisesPasswordReset.PasswordResetCredentialManager.ChangePassword(String changePasswordXMLRequestString)
Additional SSPR Reading
Below are some additional links to how SSPR operates and its deployment.
How it works: Azure AD self-service password reset
Self-service password reset deep dive - Azure Active Directory - Microsoft Entra | Microsoft Learn
Cheers,
Rhoderick