Starting a setup of Copilot for Security in a demo tenant led to an interesting issue where the expected bootstrap process was not launched. As an eligible administrator, when you navigate to https://securitycopilot.microsoft.com you will either access the previously deployed Copilot for Security (CfS) instance or be prompted to create it. This assumes that you are logged on as either a Global Admin or Security Admin, or setup was completed and you were assigned a role via a different Entra ID group.
Starting Environment
This is a vanilla Entra ID tenant, and you will note that there are no Microsoft Copilot for Security Compute Capacities initially present. This is the expected behaviour as CfS has not been deployed in this tenant.
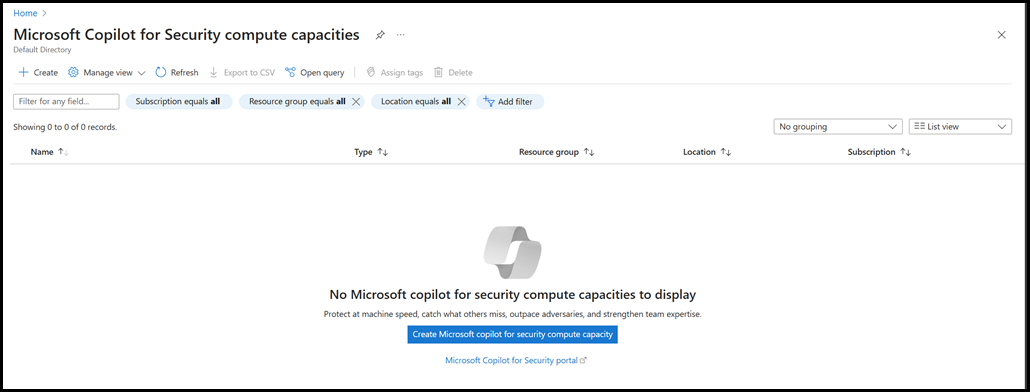
All good so far.
When accessing the standalone experience at https://securitycopilot.microsoft.com things go slightly squirrley. We get a nice black screen with an error that states:
Can't get account information

The tenant ID is redacted on purpose.
OK - plan B then. Go straight to the setup URL.
Trying CfS Setup URL
Plan B was an attempt to bypass the initial page by going directly to the setup URL. It was also not sucessful. In the image below note that the setup prompt URL was pasted directly into the browser. The URL is:
https://securitycopilot.microsoft.com/tour/welcome
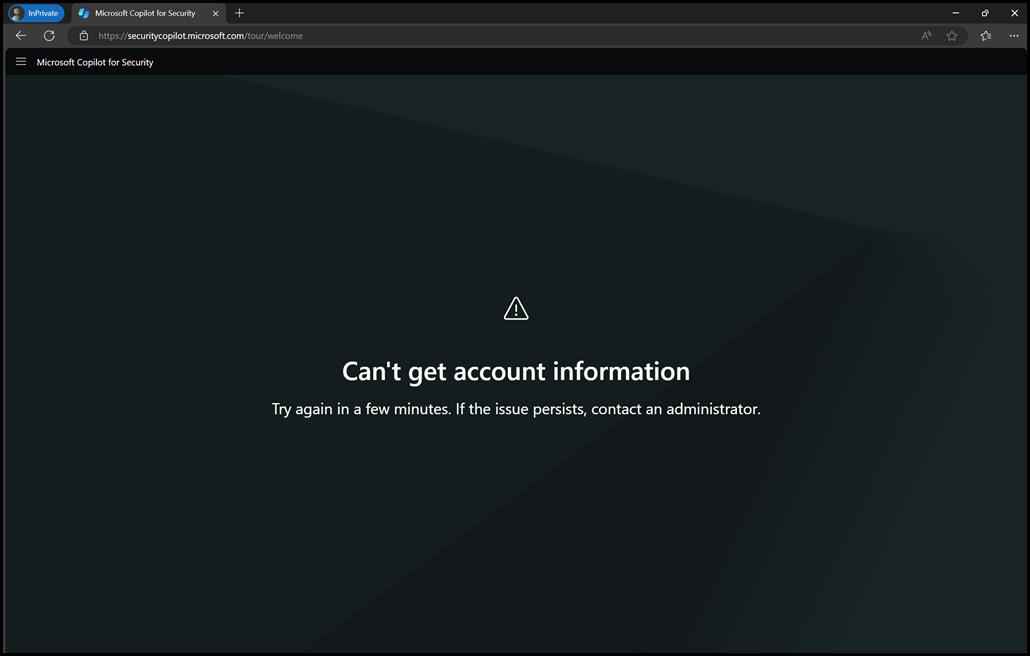
No change.
What’s up with this account? Why is this not working with the direct setup URL. Time to review the account.
Starting GA Account
Note that there is a single Global Admin account in the tenant. The details for the GA are shown below. Some details are redacted - hence the extra bits of white space.
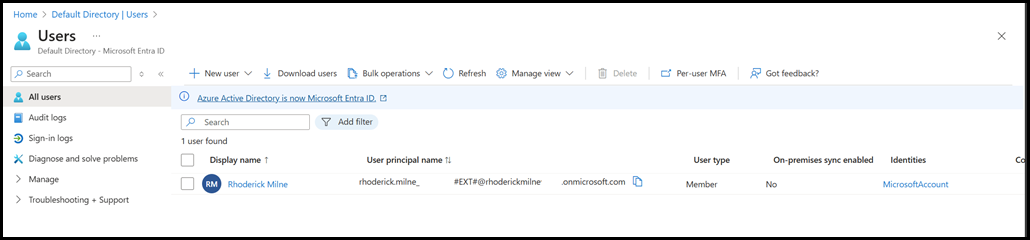
For example certain parts of the UPN are redacted. What is important though is that the account is external - you can see the #EXT as part of the UPN.
This started to make more sense as this a guest account, and not directly a member of the tenant. This was due to how the tenant was originally provisioned.
Let's create a new GA account that is part of the tenant.
New GA Account
Created a new GA account. After completing the first sign-in and registering for MFA let’s navigate to the CfS page at:
https://securitycopilot.microsoft.com
Now we have success. The URL automatically changed to the aforementioned setup prompt. This is shown in the image below:
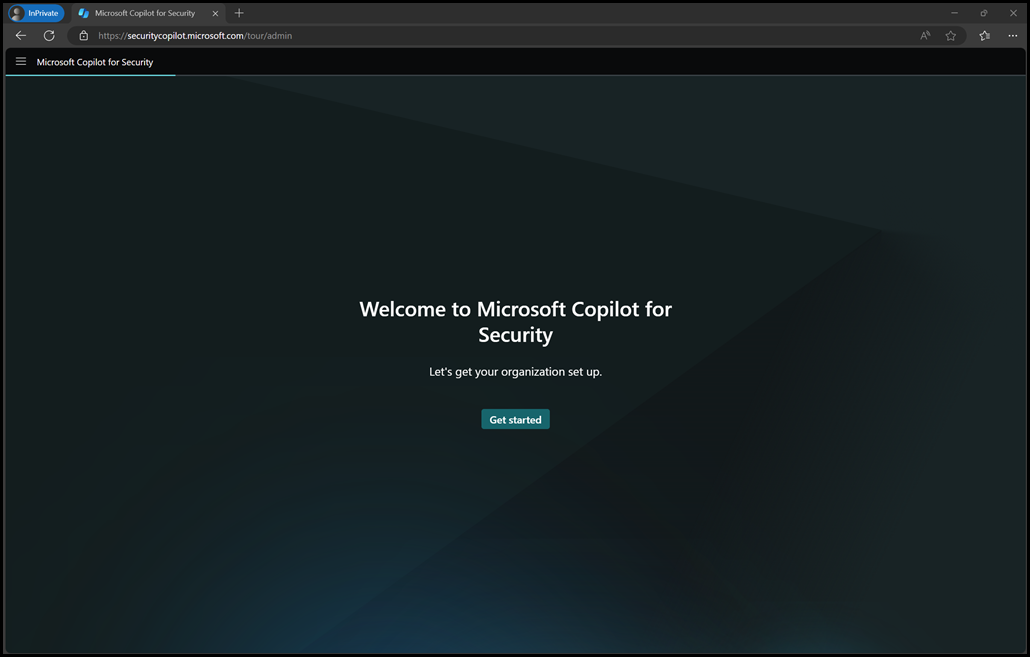
Now we can use the setup prompt to get ourselves started!
https://securitycopilot.microsoft.com/tour/admin
Bootnote
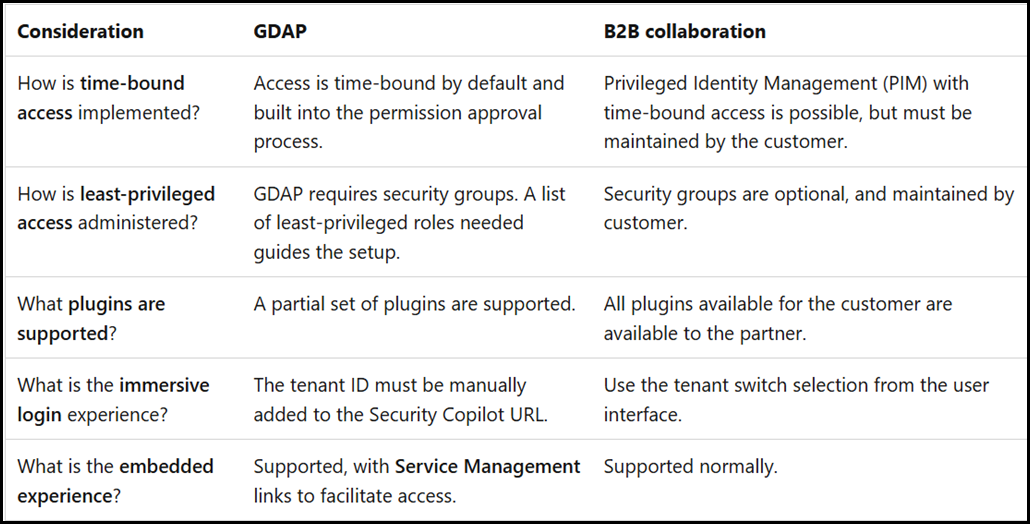
Note that partner access to a CfS instance is supported through multiple mechanisms. At the time of writing there are two. This is documented here:
Grant partners access to Microsoft Copilot for Security
If you're working with a Microsoft Managed Security Solution Provider (MSSP), you can grant them access to your Microsoft Copilot for Security capabilities. When you grant an MSSP access, they're able to sign in and use Copilot for Security just like your security team.
There are two ways to allow a partner to manage your Microsoft Copilot for Security.
- GDAP
Approve your partner to gain Security Copilot permissions for your tenant. They assign a security group the permissions needed using Granular Delegated Admin Privileges (GDAP). - B2B collaboration
Set up guest accounts for individuals from your MSSP to log into your tenant.
There are tradeoffs for both methods. Use the following table to help decide which method is best for your organization. It's possible to mix both methods for an overall partner strategy.
Cheers,
Rhoderick