Exchange 2019 CU15 has been released to the Microsoft Volume Licensing Center and the public Microsoft Download site! Exchange 2019 has a different servicing strategy than Exchange 2007/2010 and utilises Cumulative Updates (CUs) rather than the Rollup Updates (RU/UR) which were used previously. CUs are a complete installation of Exchange 2019 and can be used to install a fresh server or to update a previously installed one. Exchange 2013 and 2016 have the same servicing methodology.
Previously Exchange 2019 updates were only available through the Volume Licensing Centre. This was changed during the March 2021 Hafnium attack.
This is the planned CU which will be released for Exchange Server 2019. Exchange 2019 support ends on the 14th October 2025.
Details for the release are contained in KB5042461.
Previous Updates of Note
As previously promised with CU14 Extended Protection is now required.
CU14 added support for Exchange 2019 to be installed onto Windows Server 2022. CU12 previously added support for Windows Server 2022 domain controllers.
The November 2024 Security Update (SU) added multiple features, which are also included in CU15.
Improvements in Exchange Server AMSI integration
Starting with November 2024 SU release, we have extended the ability of products that use the Exchange Server AMSI integration to perform additional tasks on message bodies. The feature is disabled by default and can be enabled on a per protocol basis.
For more information on AMSI integration please see AMSI integration with Exchange Server | Microsoft Learn
Non-compliant RFC 5322 P2 FROM header detection
To address vulnerability CVE-2024-49040, a new feature was implemented to detect non-RFC 5322 compliant P2 FROM headers in incoming email messages. The P2 FROM header in an email is part of the message header that is displayed to the recipient's email client (for example, Outlook). It's the sender's email address or name (if the sender is internal) that appears in the From field when you view an email in your inbox.
ECC certificate support improvements
November 2024 SU improves support for ECC certificates. ECC certificates can now be used on Edge Transport servers and can be bound to POP and IMAP service. Note that there is a change in how ECC Certificate support can be enabled. In the previous implementation, a New-SettingOverride was needed to enable the feature. Starting with the November 2024 SU, you need to create a registry value instead of the override.
Updates Of Particular Note
This CU contains the latest security updates at the time of release. The latest DST time zone updates are also included.
Exchange Server 2019 CU15 cannot be installed in an organization that has any servers running Exchange 2013. You must deactivate and uninstall all Exchange 2013 servers from your organization before you install CU15. You should also expect a similar requirement with the release of Exchange Subscription Edition (SE) CU1, as all Exchange 2016 and 2019 servers must be removed in order to install SE CU1.
-
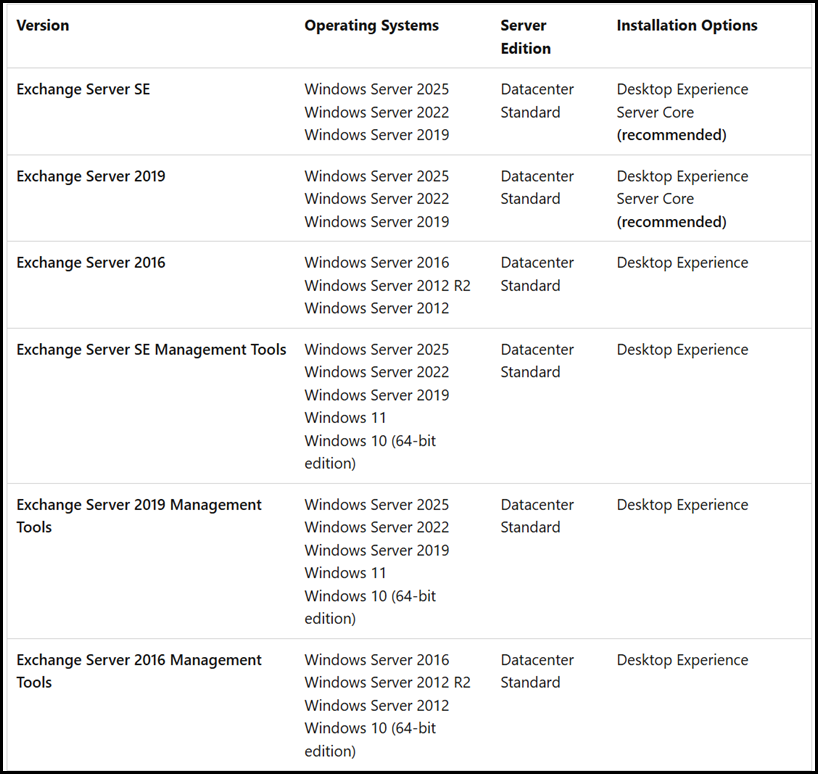
Support for Windows Server 2025 – Details are in the table below:
-
Partial TLS 1.3 support for Exchange Server 2019 - Microsoft Exchange Server 2019 CU15 adds TLS 1.3 support (except for SMTP) to existing Microsoft Exchange Server 2019 on-premises installations that are running on eligible systems (Windows Server 2025 and Windows Server 2022). Note that TLS 1.3 server support is not backported to Windows Server 2019 or older.
-
Certificate management tasks restored to EAC - Previous there was a security concern with certificate management tasks that accepted UNC input which was disabled with Exchange 2019 CU 12. CU15 has restored these tasks to the EAC.
-
OIT module in Exchange Server is replaced by DocParser - Starting in Microsoft Exchange Server 2019 CU15, Exchange Server uses DocParser as a replacement for the "Oracle Outside In Technology" (also known as OutsideInModule or OIT) to perform text extraction workloads when it processes email messages in transport if those messages contain attachments. DocParser is a Microsoft library that's designed to parse various file formats. For supported file types, see the following Learn article: Use transport rules to inspect message attachments.
-
Feature Flighting in Exchange Server - Microsoft Exchange Server 2019 CU15 introduces "Feature Flighting." For more information about the new feature, see Feature Flighting. Feature Flighting provides an additional way for administrators to test and roll out select new features across their Exchange Server organization. Feature Flighting is an optional cloud-based service for on-premises Exchange servers. It uses the
Office Config Service (OCS)- the same endpoint used by the Emergency Mitigation service and Microsoft Office clients—to check for updates from Microsoft related to flighted features
Note that there are no features being flighted in CU15, nor is this change planned for the SE RTM release. This is because of the commitment to code equivalency in CU15 and SE RTM builds.
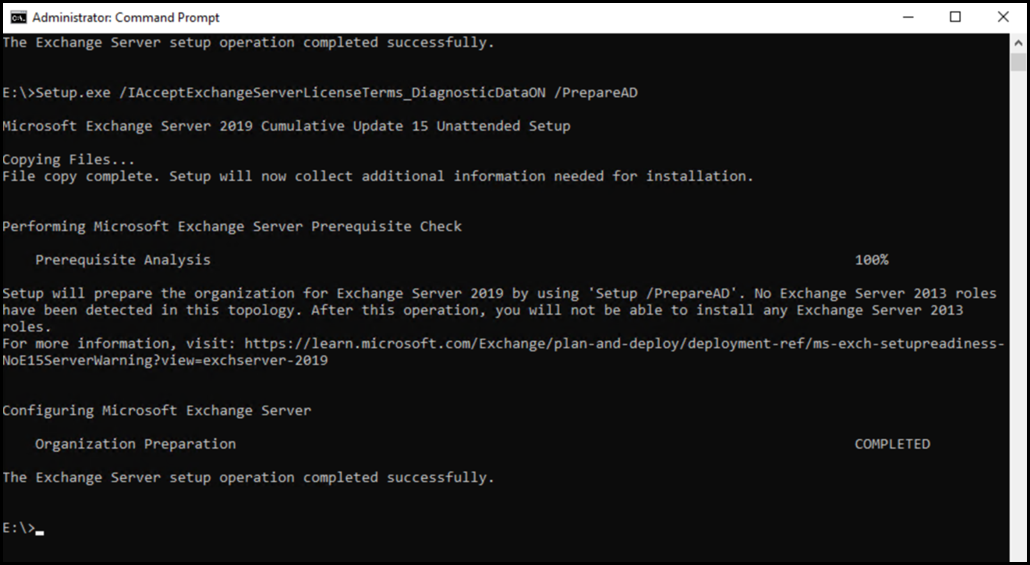
The screenshot below is from an Exchange 2019 organisation when running CU15 /PrepareAD. Only a single Exchange Server 2019 is present.
Issues Resolved
-
5047359 Clean up old Exchange OWA files automatically to free up disk space
-
5047361 Inline images and text attachments are not visible in OWA
-
5047402 Online Archiving bypasses the InternetWebProxy setting in Exchange 2019
-
5047995 MFNs are not sent to remote domains
-
5047997 Wrong server version displayed in POP and IMAP logoff strings
-
5048017 RecoverServer operation fails in Exchange Server 2019
-
5048019 "NullReferenceException" error and Managed Store stops responding
-
5048020 Calendar print doesn't work in OWA from Exchange 2019 CU14 onwards
-
5048021 HTML message is corrupted if <"e;> is included
-
5048072 "Enabled Extended Protection" message when you run setup with prepare* command
-
5047994 German umlauts in the Subject are replaced by a question mark
-
5047358 Group Metrics generation doesn't finish in multidomain environment
Known issues in this cumulative update
-
The Edge Transport service (EdgeTransport.exe) stops responding and then restarts. For more information and a workaround, see Edge Transport service stops responding after installing November 2024 SU or Exchange 2019 CU15.
Some Items For Consideration
Exchange 2019 follows the same servicing paradigm for Exchange 2013 and 2016 which was previously discussed on the blog. The CU package can be used to perform a new installation, or to upgrade an existing Exchange Server 2019 installation to this CU. Cumulative Updates are well, cumulative. What else can I say…
Customers with a hybrid Exchange deployment, must keep their on-premises Exchange servers updated to the latest update or the one immediately prior ( N or N-1). Since this is the last CU, customers will need to move to CU15 in due course.
-
Test the CU in a lab which is representative of your environment
-
Review this post to also factor in AD preparation which is to be done ahead of installing the CU onto the first Exchange server
-
Follow your organisation’s change management process, and factor the approval time into your change request
-
Provide appropriate notifications as per your process. This may be to IT teams, or to end users
-
Run the Exchange Health Check Script against all servers, and ensure there are no issues prior to installing the new CU. Always download the latest version from https://aka.ms/ExchangeHealthChecker -- though the script now does have an update function if your server has Internet access.
-
Generally you do not have to re-run the Exchange Hybrid Configuration Wizard as part of a CU update, thought it is prudent to have this as a contingency aspect of your change. If you do not have the required permission in Exchange Online, list a person who does as part of the change should it be required
-
After you install this cumulative update package, you cannot uninstall the cumulative update package to revert to an earlier version of Exchange. If you uninstall this cumulative update package, Exchange is removed from the server
-
Place the server into SCOM (or whatever is used) maintenance mode prior to installing, confirm the install then take the server out of maintenance mode
-
Place the server into Exchange maintenance mode prior to installing, confirm the install then take the server out of maintenance mode
-
I personally like to restart prior to installing CUs. This helps identifies if an issue was due to the CU or happened in this prior restart, and also completes any pending file rename operations. 3rd party AV products are often guilty of this
-
Restart the server after installing the CU
-
Ensure that any Exchange security updates are installed
-
Ensure that all the relevant services are running
-
Ensure that event logs are clean, with no errors
-
Re-Run the Exchange Health Check Script
-
Ensure that you consult with all 3rd party vendors which exist as part of your messaging environment. This includes archive, backup, mobility and management services
-
Ensure that you do not forget to install this update on management servers, jump servers/workstations and application servers where the management tools were installed for an application. FIM and 3rd party user provisioning solutions are examples of the latter
-
Ensure that the Windows PowerShell Script Execution Policy is set to “Unrestricted” on the server being upgraded or installed. See this article on setting PowerShell to Unrestricted
-
Disable file system antivirus prior to installing. Do this through the appropriate console. Typically this will be a central admin console, not the local machine
-
Verify file system antivirus is actually disabled
-
Once server has been restarted, re-enable file system antivirus
Please enjoy the update responsibly!
What do I mean by that? Well, you need to ensure that you are fully informed about the caveats with the CU and are aware of all of the changes that it will make within your environment. Additionally you will need to test the CU your lab which is representative of your production environment.
Cheers,
Rhoderick