You will have seen the multiple posts and communications around the Hafnium Exchange security issue. One of the most disconcerting issues has been the number of Exchange installs that have not been patched in several years. Once the storm has abated, I'll put down some thoughts and talk through some of the most problematic issues, but for now let's focus on the task in hand. Security updates are released only Exchange builds that are available for servicing, and typically this is N and N-1. Though an exception was made for this security issue. Please note this does not fundamentally change what unsupported customers need to do, it is only short term relief.
Since many Exchange servers have not been kept at the current Cumulative Update (CU), this means that many customers have had to install a CU in order to be in a position to then install the Security Update (SU). An additional complication is that the .NET Framework also requires an update. In many cases this has resulted in three major tasks per server rather than one, which would have been the SU installation.
Exchange 2013 has a couple of nuances that are not present with Exchange 2016 or 2019.
- Firstly only CU23 is supported at this time.
- Secondly .NET Framework 4.7.2 and 4.8 are supported, though 4.8 is recommended.
Some of the initial publications stated that in order to install Exchange 2010 SP3 RU32 you must already be on RU31. That is not correct.
A similar item was posted on Exchange 2013 CU23 where .NET 4.8 was required. This is not the case. It is recommended, and you will also see this in the HealthCheck script output at the end of this post.
Exchange 2013 supports .NET Framework 4.7.2 and 4.8 – this is noted in the Microsoft Exchange Support matrix's Microsoft .NET Framework section. Specifically the .NET topic for Exchange 2013.
Lab Example
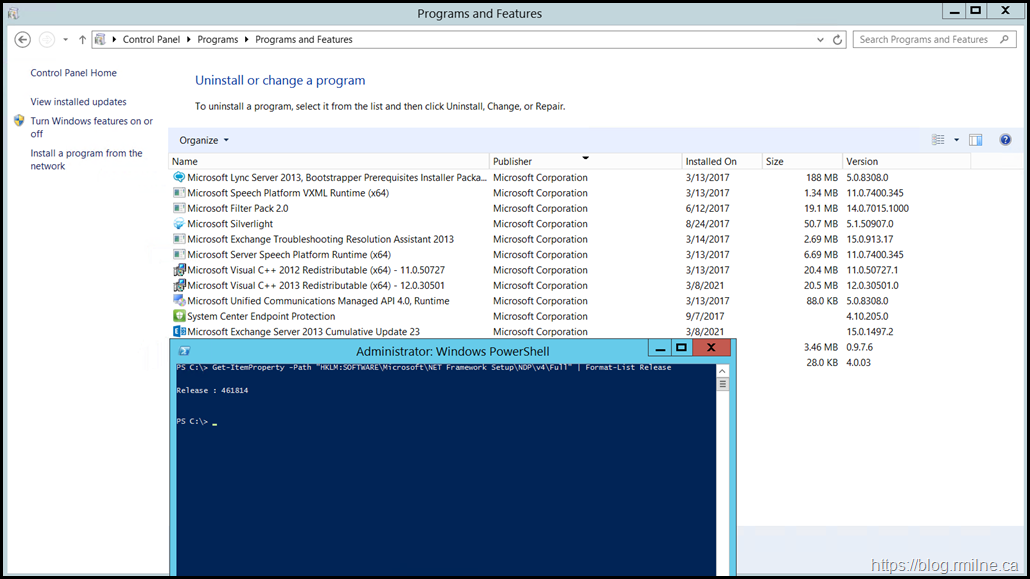
In the below lab server, note that Exchange 2013 CU23 is installed along with .NET Framework 4.7.2 0 this post includes the registry key to check the .NET version.
The value returned with the query is 461814 which indicates that this is .NET Framework 4.7.2 on Windows Server 2012 R2.
Installing March 2021 Security Update
The March 2021 SU must be install installed, it is currently missing. Please note that this is done from an elevated CMD prompt. This is probably the biggest issue that I've seen with the recent updates causing issues.
I will *ALWAYS* tell you to use an elevated CMD prompt rather than PowerShell as it helps prevent issue #6 here in the future.
The install process starts, and goes through the normal steps to verify that the SU is actually applicable to this installation of Exchange.
Once the checks have completed, then we can complete the installation.
The below indicates that the install has completed successfully. It is important to read what is written to ensure that you do not skip over a potential error.
That has happened unfortunately.
The server was restarted, and post-installation tasks completed.
Running Validation Script
Since there have already been multiple scripts released to help look for Indicators of Compromise (IOC), and since they will likely change again, I will not link to a specific script.
Please check the HAFNIUM targeting Exchange Servers with 0-day exploits post for the latest validation scripts, processes and tools.
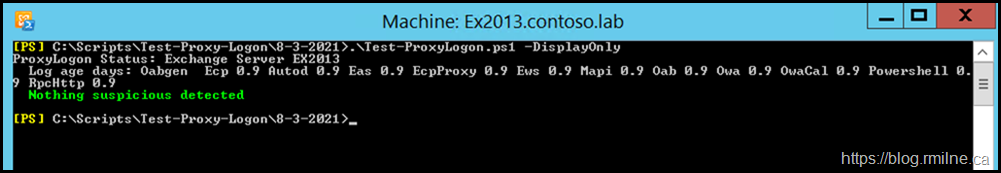
The below is the Test-ProxyLogon.ps1 as of 8th March 2021.
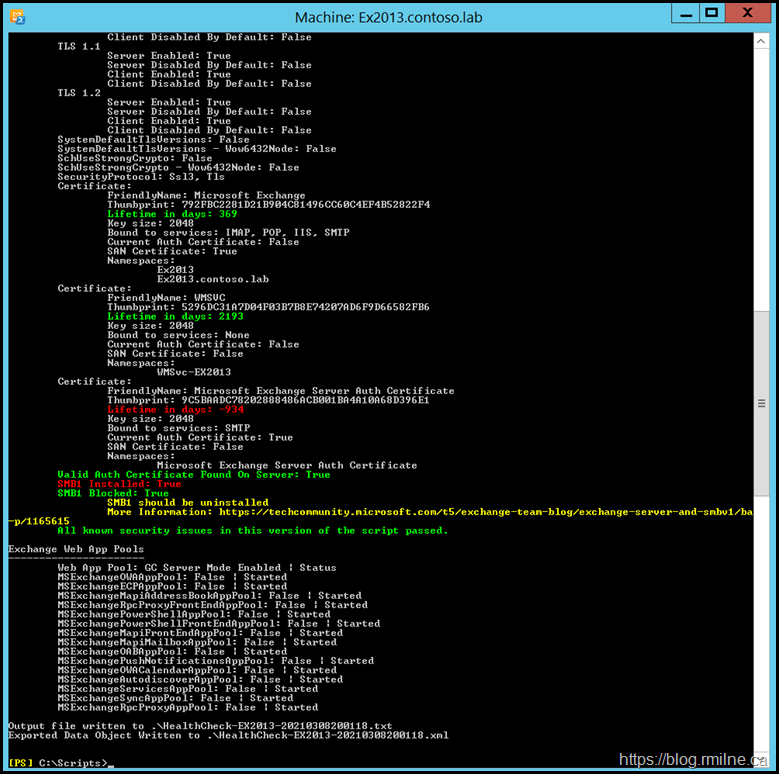
HealthChecker.ps1 is shown below, note that no security issues are noted.
The Exchange server auth certificate has expired as this is an old on-premises lab.
Cheers,
Rhoderick