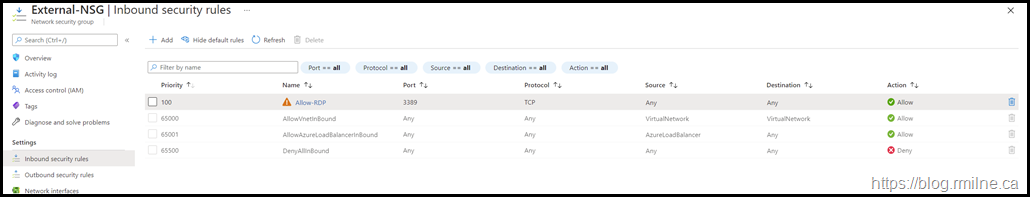
The below is from a customer situation where an Azure Network Security Group (NSG) firewall rule entry was not working as they expected. This was was created to allow RDP connectivity for some of their test servers.
However they were not able to connect to the server, and were being blocked by the NSG.
Ideally we do not want to allow RDP to our Azure VMs are there are more secure methods such as client VPN, site to site VPN and Azure Bastion. For this reason the portal displays the orange warning triangle on rules which permit RDP.
In this case though the actual issue will impact the NSG rules in general no matter what the service type. An example of this is shown at the end of the post.
What Was Observed
In the list of allowed rules, an orange triangle was present on the RDP rule. As we noted, RDP access should be restricted it is expected to see the orange warning triangle.
The customer was used to this warning and grew familiar to it. Maybe too familiar.
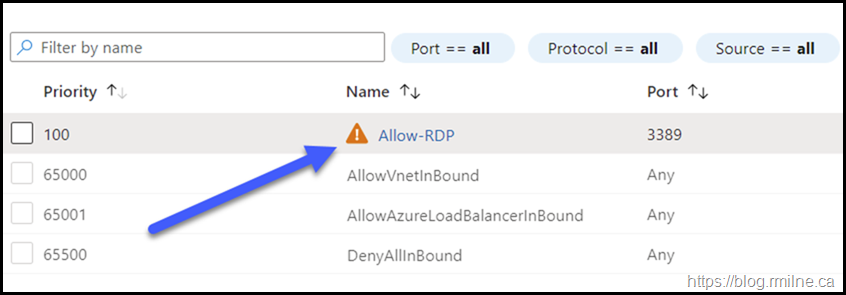
If we zoom in, the arrow highlights the rule entry and the orange triangle warning.
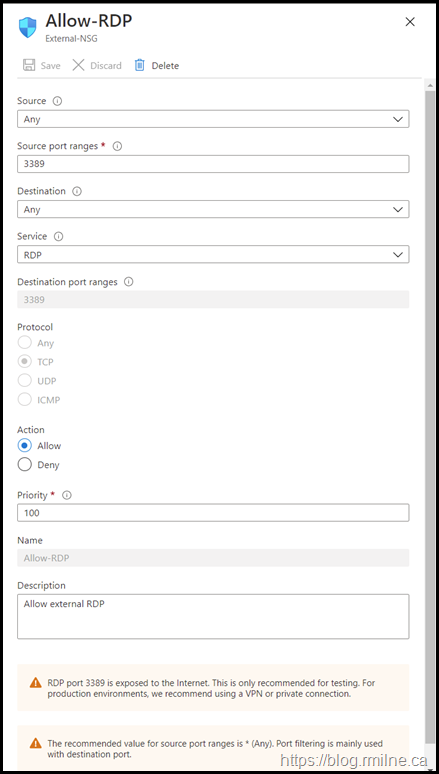
Looking at the details of the rule which they had created, we see the below. Does anything seem wrong in the rule?
Hint: Think of how TCP/IP works.
Breaking The Rules
The issue is almost hidden in plain sight. Why almost? There is also a warning along the bottom which explains it.
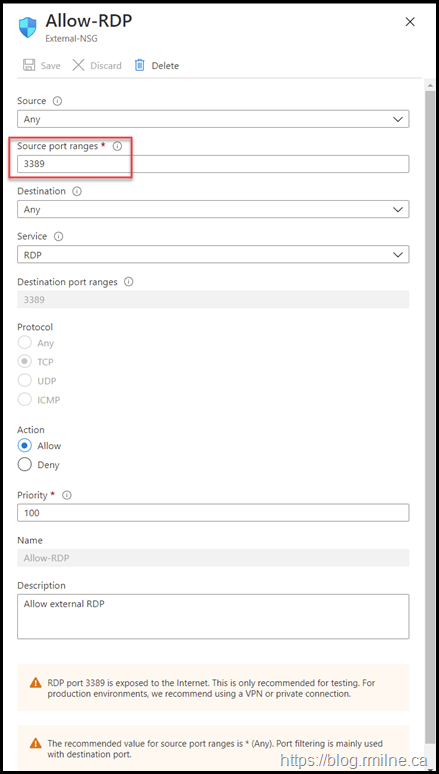
Highlighted below is what they configured as the source port. A mistake was made and port 3389 was entered into the source port configuration
This is not the expected TCP/IP flow. We would expect the client machine to use a random port in the ephemeral port range (49152 – 65535 as per the IANA recommendation) as the source port. Since the rule allowed only connects from TCP 3389 on the client to connect to the server side port of TCP 3389, the rule conditions were never met so access was not allowed and the traffic was denied.
From the warning along the bottom:
The recommended value for source port ranges is * (Any). Port filtering is mainly used with destination port.
While the UI does warn if RDP is being used as a security caution, specifying a specific source port in a rule will also cause the orange warning triangle.
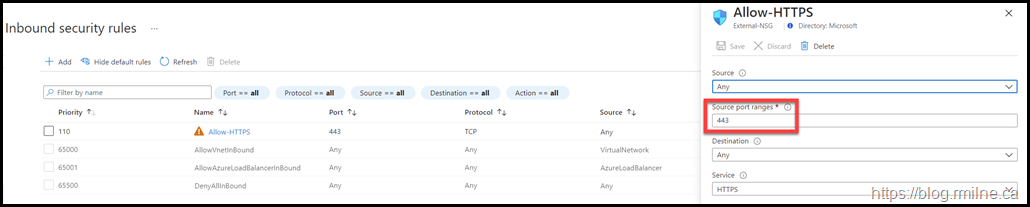
This is show in the rule below for HTTPS. Note the source port is shown as 443.
Cheers,
Rhoderick
love it !!!