After doing Exchange Risk Assessment (ExRAP) and Exchange Risk Assessment As A Service for almost four years, one thing continues to irritate my OCD personality! When I look at the event logs on an Exchange server, the logs should be a sea of blue. That is there should be no errors as that indicates something is not quite right and should be addressed.
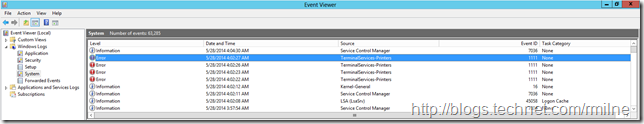
Opening up the system event log on numerous customer’s servers I’m pretty much guaranteed to see errors related to mapping printer drivers in the Terminal Services/Remote Desktop session. As you would expect, this is fluff that I just do not want to see. How to make this disappear then?
Since our venerable friend, Windows Server 2003, is going to exit extended support in a little over a year, I’ve based this post on a Server 2012 R2 box, but the principles still hold true for our trusty friend!
Let’s look at manually getting rid of the errors, and then using Group Policy to effectively manage multiple servers. First up, let’s see the error:
Opening up the system event log, we are greeted with the below errors:
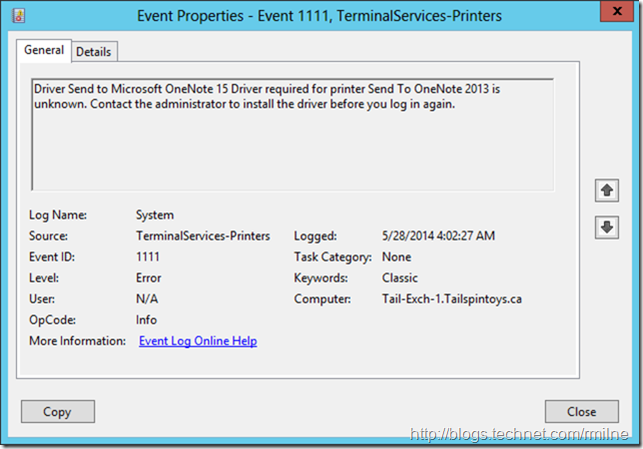
This is EventID 1111 on a Windows Server 2012 server. In this case the Exchange server does not have a printer driver for OneNote installed (as expected), and is unable to create a printer mapping to the printer that is installed on the workstation that just RDP’ed to the Exchange server.
Manually Controlling Printer Mapping On Server 2012 R2
If you look for the Remote Desktop Session Host Configuration tool in Windows Server 2012 R2, you will not find it present. Either set the desired configuration using the registry directly or the Local Group Policy Object which is located here:
Computer Configuration –> Administrative Templates –> Windows Components –> Remote Desktop Services –> Remote Desktop Session Host -> Printer Redirection > Do not allow client printer redirection
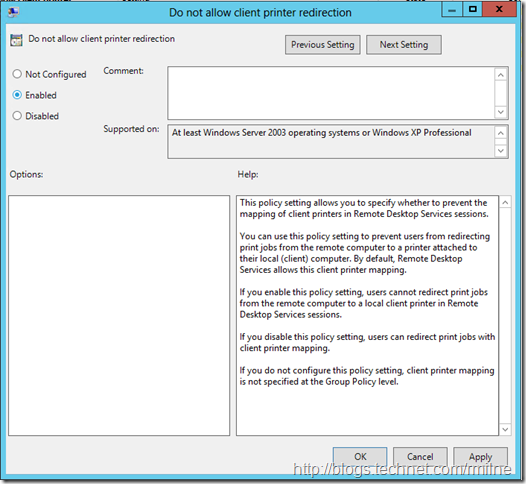
The below is a screenshot of the Local Group Policy Object where we can configure printer redirection:
Select Enabledto activate the policy setting and click OK.
This will set the following registry key for fDisableCpmwhich we can also set manually.
HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services
RegDWORD fDisableCpm 1
To automate this we can use reg.exe – note that the command is a single line and may wrap.
REG.exe ADD "HKLM\Software\Policies\Microsoft\Windows NT\Terminal Services" /V fDisableCpm /t REG_DWORD /D 1 /F
To check the status of the Registry value we can run:
REG.exe QUERY "HKLM\Software\Policies\Microsoft\Windows NT\Terminal Services" /V fDisableCpm
That’s great for a couple of test boxes, but we do not want to do that on 100,000 servers in the enterprise and we will typically look to Group Policy in such cases.
Controlling Printer Mapping On Server 2012 R2 Using GPO
In a typical enterprise environment we do not want to change lots of individual servers when it is easy to leverage GPO for this purpose. Again the configuration is stored in the same location as the Local GPO discussed above. Open the Group Policy Management Console, create a new GPO or edit an existing one – the choice is yours! Navigate to:
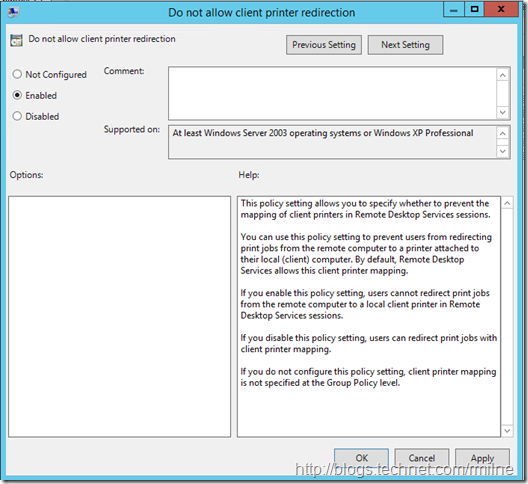
Computer Configuration –> Administrative Templates –> Windows Components –> Remote Desktop Services –> Remote Desktop Session Host -> Printer Redirection > Do not allow client printer redirection
Select Enabled to activate the policy setting and click OK.
Once the GPO has refreshed on the Exchange server, the pesky printer mapping errors should be banished!
Bonus Tip
There are many settings contained in GPO that can be applied to an Exchange server to tune the Windows installation that it sits upon. One other area that is typically identified in a ExRAP/ExRaaS is that of event log size and retention. We can set the maximum size of Event logs and how to retain data under the following GPO location:
Computer Configuration –> Policies –> Windows Settings –> Security Settings –> Event Log
Again we can use local policies, command line tasks and PowerShell to configure this but GPO will typically be the best bet for larger customers.
Cheers,
Rhoderick