I was recently reminded of a simple yet effective Event Viewer filtering tip. If you have thousands of event entries that are pollution/flooding the log it becomes very difficult to see the actual real issues.
For example this tip has proved very useful when the application event log is full of these types of noise:
-
EventID 1 from MSExchange Autodiscover stating Unhandled Exception "User setting 'PreferredSite' is not available." This was an issue resolved in Exchange 2010 SP2 RU5.
-
VMware tools warnings stating “Error in the RPC receive loop: RpcIn: Unable to send”. Please see VMware KB 2036350 for details on the issue.
-
Default McAfee implementation reports that the server is sending SMTP email. This is EventID 258 from McLogEvent stating “Would be blocked by access protection rule(rule is in warn-only mode) (Antivirus Maximum protection prevent mass mailing warms from sending mail.)”
The third example will log once a minute if it detects that the server was sending SMTP email. If the server is an Exchange box then SMTP is its raison d'être. Logging one of these a minute will generate 1440 events a day that you then have to ignore. Talk about seeing not seeing the trees for the wood.
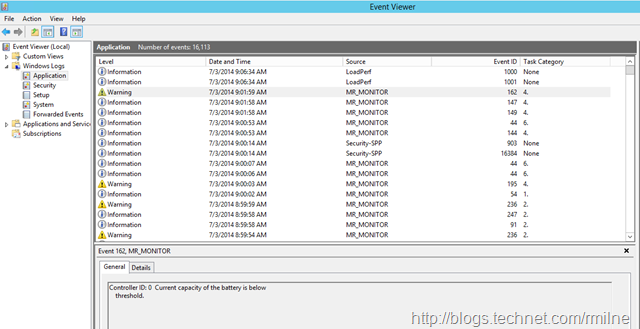
This all came to mind from looking one of my lab servers that has a very chatty RAID card. The application event log typically looks like this from source MR_Monitor
In amongst all of this, how to narrow down and just look for the relevant information?
Filter Options Basics
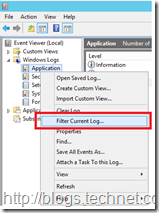 Right clicking the event log name and selecting the “Filter Current Log” will then display the various options which are shown in the screen capture below.
Right clicking the event log name and selecting the “Filter Current Log” will then display the various options which are shown in the screen capture below.
There are various options for filtering the event log, and depending upon your exact circumstance different options will make sense.
There are options to filter based on, which are fairly self explanatory:
-
Time logged: There are pre-canned filters for the last hour, last 12 hours, last 24 hours, last week and last 30 days. Additionally you can specify a custom range.
-
Event level: Choose to show only events that match the specified level critical, warning etc.
-
Event Source: Select to only see events from MSI Installer, DHCP client etc.
-
EventID: Specify the event ID.
-
Keywords: Specify filters based on Audit Failure, Audit success
-
User
-
Computer(s)
You can also flip to the XML tab and specify an event filter in XPath, but we can leave that for another post.
Filter Option Tips
There are a few things that I have a habit of doing in here.
Exclude The Offending EventIDs
As discussed at the start of this post, how to we stop the noise events from showing up in the list? Quite simply we can punch these events out by use the EventID field. This is documented right in the middle of the above screen capture but people tend not to read it for whatever reason.
Using this filed we can include/exclude:
-
Individual events
-
Ranges of events
If you know the EventID(s) that you want to see then simply specify them as the only included ones. All others will filtered out. This is great if you know that, but as mentioned above we want to remove the noise from the long and see all the other events. In that case we will exclude only the noise EventIDs.
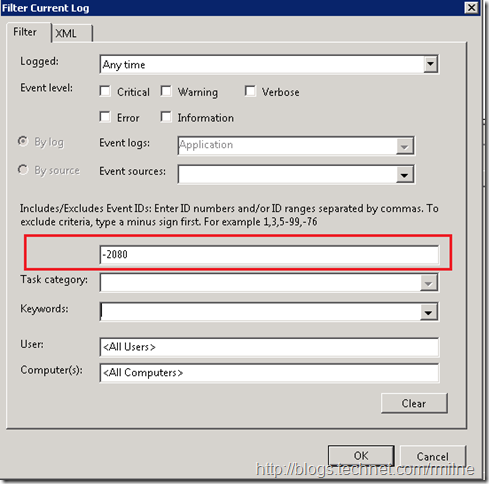
Events are excluded by using the negative operator – the minus sign. If we want to filter the EventID 2080 MSExchange ADAccess information events from the log, specify –2080 as the filter:
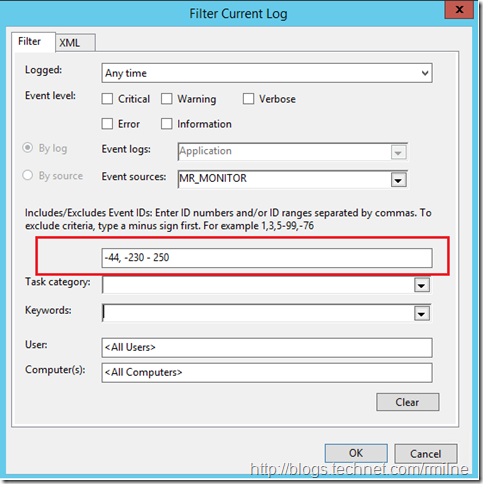
Using the above example of the chatty RAID card, I want to see all messages relating to the battery and nothing about disk detection. The disk detection events are EventID 247 and 236. Another one that I’d like to suppress is EventID 44 as that reports the runtime of the card. To exclude Event ID 44 and the range of 203 to 205 the below filter can be used:
-44, -230 - 250
Use The Built In Filters
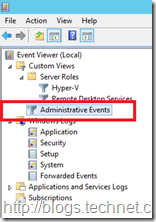 When first looking at a server with issues I like to use the Administrative Events view. This is a built in view that surfaces warnings, error and critical events from all administrative logs on the server.
When first looking at a server with issues I like to use the Administrative Events view. This is a built in view that surfaces warnings, error and critical events from all administrative logs on the server.
This allows me to get a decent overview before diving into one specific log.
Learn Some Comment Event IDs & Sources
Knowing some EventIDs helps when investigating issues.
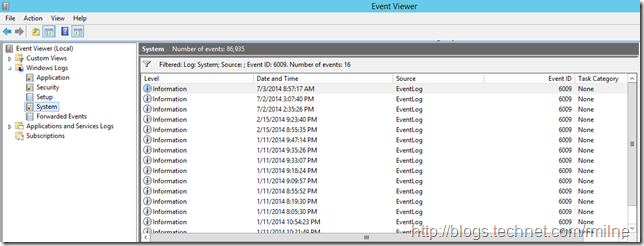
For example, knowing to filter the system log looking for EventID 6009 shows immediately the server restart dates.
What other filtering tips do you have? Care to share?
Cheers,
Rhoderick
great tip - thank you