Being able to retrieve DNS TXT records is very useful in multiple scenarios. In this post we will look at checking the TXT domain verification record for Office 365 and also for the Sender protection Framework .
In addition to a MX record, we also have the option to prove domain ownership to Office 365 by using a TXT record. Why do we want to manually check for these Office 365 TXT records? Rather than blindly running the HCW and getting multiple failures, we can check that the correct record is present. This can help prevent the MaxUriReached: Same URI cannot be attached to different AppId on a single day error, which is discussed in KB 3027942.
When configuring the Sender Protection Framework (SPF), we need to create then add the SPF record into the external DNS zone file for a given domain. This is of type TXT nowadays. This allows external mail servers to consume the SPF record and make an intelligent decision based upon who the sender purports to be.
If we want to ensure that these records are correct, and available in public DNS we can use the nslookup tool. This is very useful if we do not have direct access to the DNS provider, as that may be owned by a different team within the organization.
As mentioned in How To Check Exchange Autodiscover SRV Record Using Nslookup, there are two ways to run nslookup – interactive and noninteractive. Noninteractive is good when you know that you only want to query a single piece of data. Interactive allows multiple queries using a single instance of nslookup, and options can be toggled on and off as needed.
Using Nslookup – NonInteractive
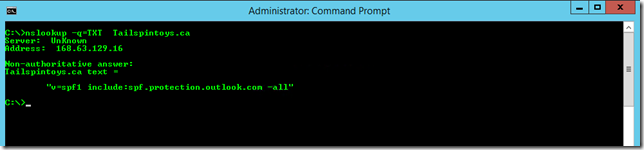
A quick query to check for TXT records in the Tailspintoys.ca domain could look like:
NSLookup.exe -q=TXT Tailspintoys.ca
For the remaining examples, interactive mode will be used.
Using Nslookup To Quickly Check TXT Records
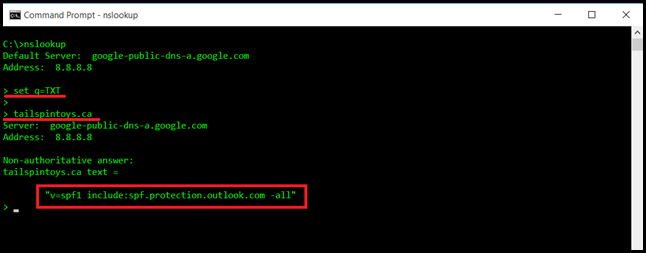
Launch nslookup in interactive mode. Then set the query type to be TXT:
set q=TXT
Then we look for the TXT records for the given domain. In this case we are looking for TXT records present in the Tailspintoys.ca domain. The public Google DNS server was used so everyone can easily access it, and follow along with the steps in this post. You will find many open WiFi spots also using it.
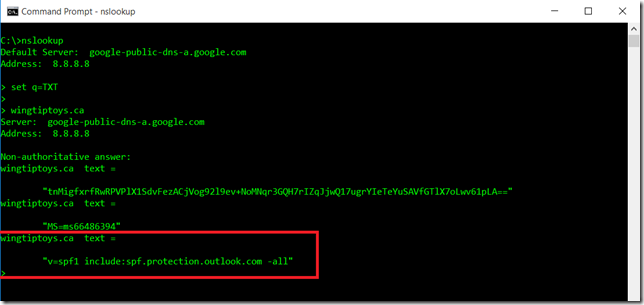
Repeating the test for the Wingtiptoys.ca domain shows additional TXT records that are present. There are three TXT records returned. The highlighted one is the SPF record, and the one immediately above that is the proof of domain ownership from Office 365.
Non-Authoritative Vs Authoritative
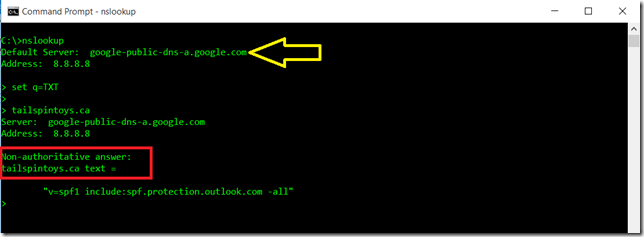
The eagle eyed reader will have noted that the queries returned are listed as non-authoritative. This is highlighted in the below red box.
Why is this? The big yellow arrow above shows that we are querying against the Google DNS server. This DNS server is not authoritative for the zone, and has performed a recursive query on our behalf.
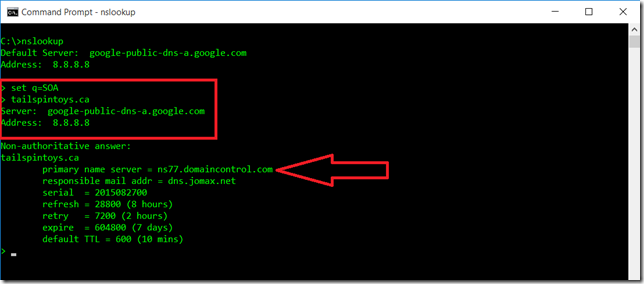
If we want to talk to the authoritative server directly, we can do so. We just need to know who that is. For redundancy purposes there should be at least two authoritative DNS servers specified in the DNS zone. While we can look for the SOA record, we should query for the Name Server (NS) record.
Note that the query type is now NS, which stands for “Name Server”.
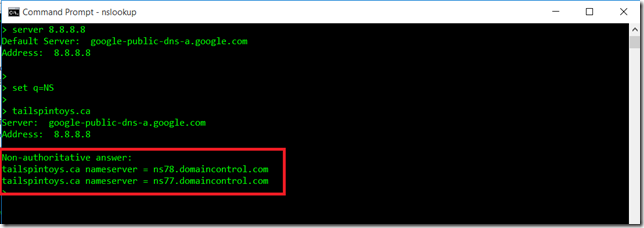
Now we know that for the tailspintoys.ca domain the two authoritative DNS servers are called ns78.domaincontrol.com and ns77.domaincontrol.com, we can query them directly. The IPv4 Addresses for those name servers are:
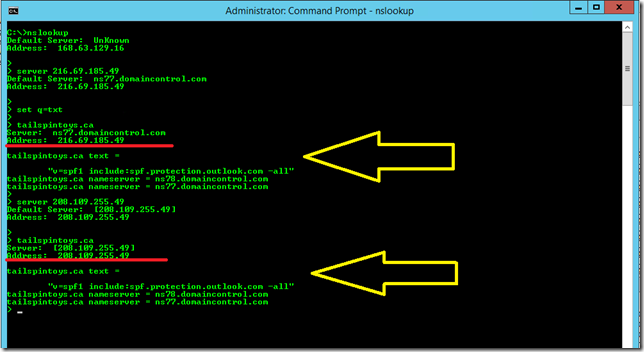
ns77.domaincontrol.com 216.69.185.49
ns78.domaincontrol.com 208.109.255.49
Note in the below screenshot, when we directly target those specific name servers, there is no mention of non-authoritative.
SPF Reference
For a quick reference, Microsoft has multiple SPF resources. The SPF wizard below helps to construct the content of your SPF record.
Update 17-11-2016 - Looks like the Microsoft SPF wizard has gone the way of the dinosaurs...... Take a look at some of the other tools out there.....
All SPF records contain three parts: the declaration that it is an SPF record, the domains & IP addresses that should be sending email, and an enforcement rule. You need all three in a valid SPF record. Here’s an example of the most common SPF record for Office 365:
TXT Name @ Values: v=spf1 include:spf.protection.outlook.com include:sharepointonline.com -all
Do not simply copy the above SPF record into your DNS zone. You need to plan to correctly implement SPF.
DNS Query Issues
Some issues that you might run into are listed below. It is not an exhaustive list.
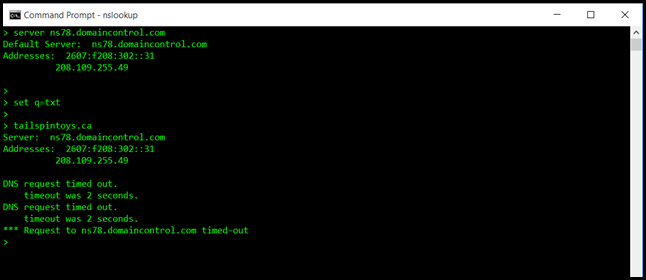
Issue #1 – Use IPv4
One of my European colleagues noted they were having issues with NSlookup. They were seeing the below where every lookup was saying DNS request timed out.
This was a weird one. Netmon never lies. But when I sniffed the traffic from my Windows 10 laptop and a Windows Server 2012 R2 VM, no packets were visible on the wire.
To resolve this, get the IPv4 Address of the DNS server and use that specifically in the server command. This is shown below.
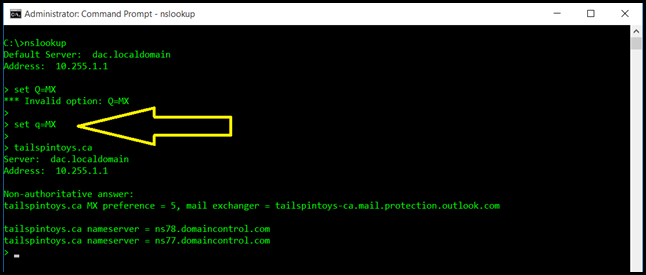
Issue #2 - Do Not Anger the Case Sensitivity Gods
In Windows there are very few things that are case sensitive. Because of this we tend to get careless with case sensitivity. Take the below example when trying to set the query type:
Note that the Q in query type is in capitals. This must be in lower case. Yes. Really.
The big yellow arrow (is it big enough??) shows that the working option is in lowercase.
Issue #3 – Beware Caching Devices
Multiple locations have implemented DNS caching devices that may or may not follow RFC standards. It is regrettable and quite common to find that some DNS caching device is quite happily ignoring the TTL on a DNS record and caching it for several days. Yes that does happen. Take the below example. This is written from some airport lounge in Canada that serves Glenfiddich. Though the amount of single malt consumed has nothing to do with any spelling mistak3s in this post!
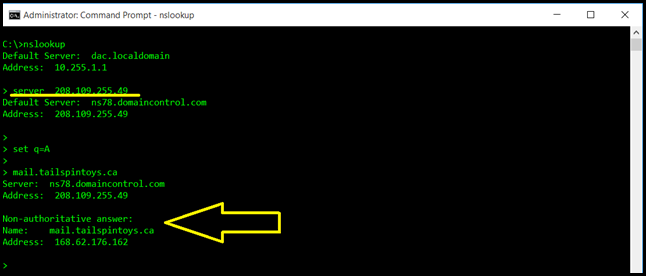
In the below example we target the authoritative name server for the tailspintoys.ca domain. But note that we only get a non-authoritative answer.
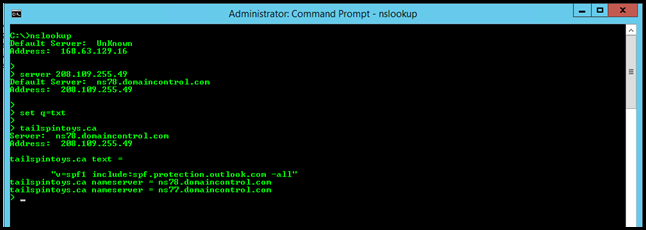
Compare this to running exactly the same commands from a VM in Azure with no DNS shenanigans:
Those are indeed authoritative replies!
Issue #4 – Driving me Dotty
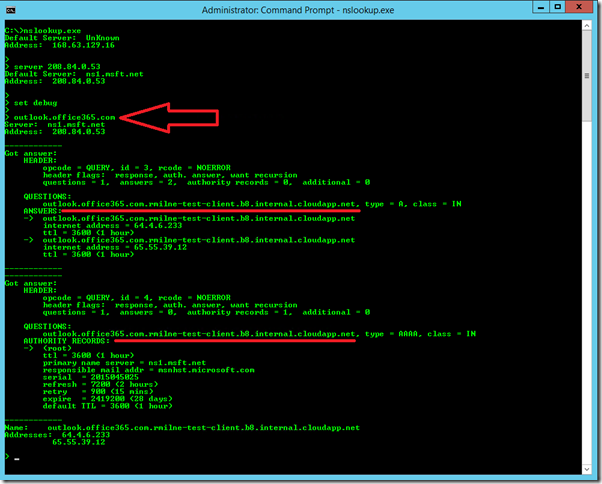
The devil is in the details, and also the dot sometimes. Note that in the below example, when we query for outlook.office365.com the query has the local computer’s DNS search suffix appended to it.
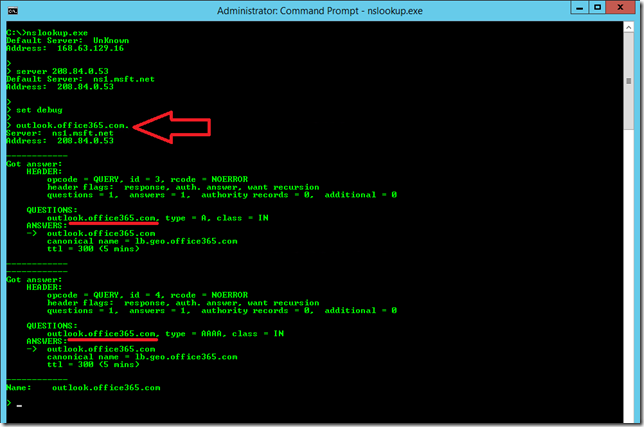
Compare the above queries (underlined in red) to the below screenshot. What is the difference? Note that the query below has a dot at the end of the query. This tells nslookup not to append the domain suffix.
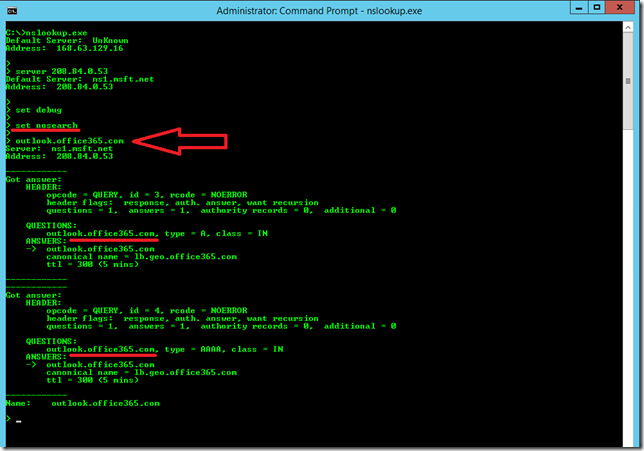
Alternatively, we can tell nslookup not to add the DNS suffix by specifying the nosearch option. This is shown below, note that there is no dot after the search term “outlook.office365.com”.
Cheers,
Rhoderick


Is there any way to check CNAME records?