The below is a repro of a customer issue where they were unable to RDP to an Azure RM VM from the Internet. Previously this was not something they had setup as connecting to VMs was provided by a site to site VPN. There was no requirement to provide RDP access from the Internet, until they wanted to allow connectivity from one specific business partner to some VMs. The partner is not part of their network.
There are a couple of ways that this could be done, for example:
- Provide client VPN to partner
- Assign an additional external IP to the required VMs, and allow connectivity
- Add a NAT mapping on a public Azure Load Balancer and allow connectivity
Since they already had the public Azure RM Load Balancer deployed, they plumped for the last option. While they did not get it working initially, only a minor tweak was required to get things going.
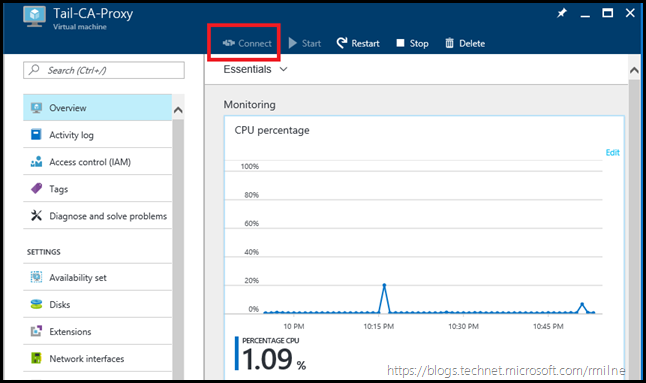
The below screen shots were taken from some of my lab VMs after I reproduced the starting configuration. Note that the Connect button is disabled:
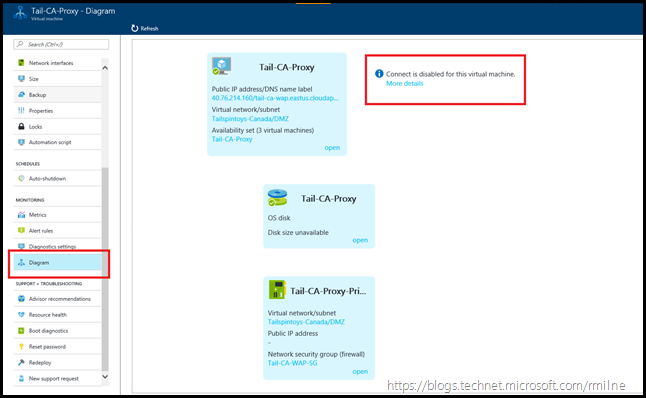
The Azure Portal does not believe there is a way to connect to the VM. If we scroll down, and select Diagram, a graphical representation of the VM is produced showing the relationship between the Virtual Network, VM and IP Configuration. The highlighted error on the right states that connect is disabled for this VM.
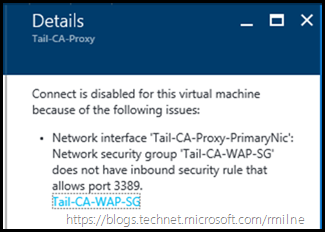
Clicking more details furnishes the below:
Connect is disabled for this virtual machine because of the following issues:
- Network interface 'Tail-CA-Proxy-PrimaryNic': Network security group 'Tail-CA-WAP-SG' does not have inbound security rule that allows port 3389.
No inbound rule for the RDP port, that would break it….
Mind the Gap
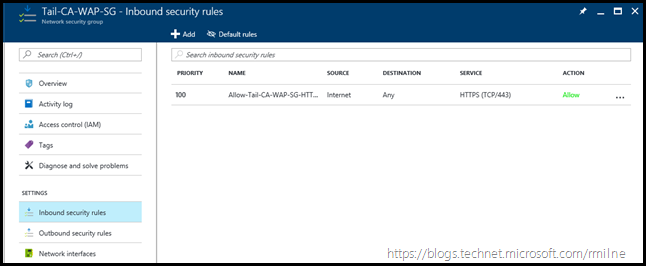
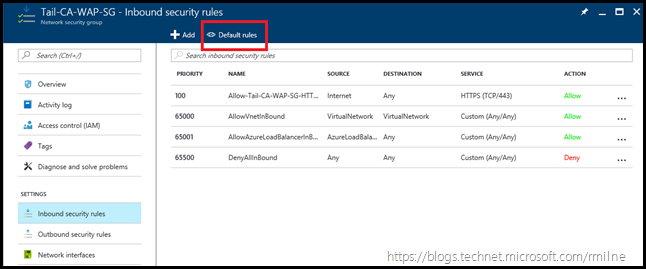
The Network Security Group configuration is replicated below. There was one rule created, which is for external access to HTTPS. It does not allow RDP traffic on TCP 3389.
Click the Default Rules button, to see the default rules.
It was a misunderstanding of the default rules which led to this pickle. Note that one of the default rules is called AllowAzureLoadBalancerInBound.
The admin thought that this would allow all traffic which traversed the Load Balancer. Well, not so much. The traffic may be NAT’d on the Load Balancer, but the source is from a remote IP on the Internet. There was no allow rule, so it was dropped.
Making It Right
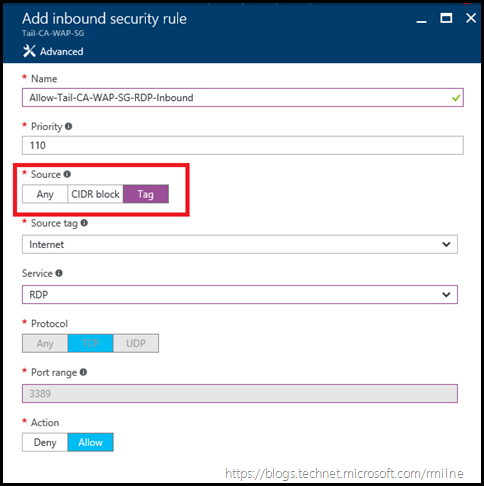
Now that this gap was identified, it was quick to then create an allow rule to permit inbound RDP from the relevant source IP/IP range. In this case the source tag was set to Internet. A rule called Allow-Tail-CA-WAP-SG-RDP-Inbound was created to permit TCP 3389 inbound.
The RDP allow rule is added to the Network Security Group.
After a few seconds, verify that access is working from the outside. You should be good to go!
Cheers,
Rhoderick