The below is an issue which caused this week’s customer a little stress. They wanted to review the current AD FS configuration, but were not able to successfully run the Get-AdfsPropeties cmdlet.
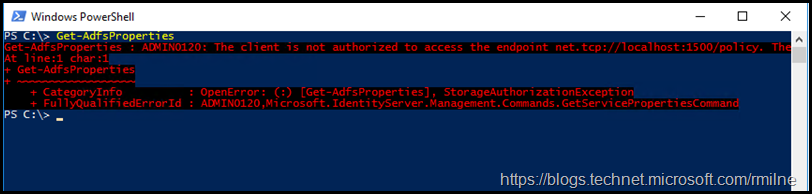
The Get-AdfsProperties cmdlet would generate the error below.
For make most glorious benefit of search engines:
Get-AdfsProperties : ADMIN0120: The client is not authorized to access the endpoint net.tcp://localhost:1500/policy. The client process must be ru
At line:1 char:1
+ Get-AdfsProperties
+ ~~~~~~~~~~~~~~~~~~
+ CategoryInfo : OpenError: (:) [Get-AdfsProperties], StorageAuthorizationException
+ FullyQualifiedErrorId : ADMIN0120,Microsoft.IdentityServer.Management.Commands.GetServicePropertiesCommand
They focused on the localhost:1500/policy portion of the message, and thought that the AD FS service was not running. It was. So what was up?
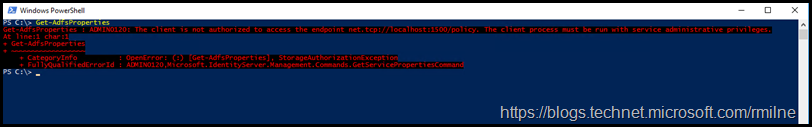
Part of the issue was that the PowerShell result text was truncated. If the window was resized, does the below shine additional light?
Get-AdfsProperties : ADMIN0120: The client is not authorized to access the endpoint net.tcp://localhost:1500/policy. The client process must be run with service administrative privileges.
At line:1 char:1
+ Get-AdfsProperties
+ ~~~~~~~~~~~~~~~~~~
+ CategoryInfo : OpenError: (:) [Get-AdfsProperties], StorageAuthorizationException
+ FullyQualifiedErrorId : ADMIN0120,Microsoft.IdentityServer.Management.Commands.GetServicePropertiesCommand
Bootnote
This was classic case of not elevating the cmd prompt or PowerShell instance.
See this post for an easy way to elevate.
Cheers,
Rhoderick
Hm... this does not actually explain how to grant access to the service, only that you can simply be a full sysadmin to have access. How do I assign rights to specific accounts? Any ideas?
Hi Andrew,
Take a peek at this please for specific delegation examples:
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/delegate-ad-fs-pshell-access
Cheers,
Rhoderick