The May 2022 security update for Exchange Server 2013, 2016 and 2019 resolved CVE-2022-21978. A common issue is that admins are only doing part of the work to address this CVE. Yes they are installing the update, but are not reading the rest of the documentation which states that an additional command must be run.
The FAQ states:
Do I need to take further steps to be protected from this vulnerability?
Because of additional security hardening work for CVE-2022-21978, the following actions should be taken in addition to application of May 2022 security updates:
Setup.exe /IAcceptExchangeServerLicenseTerms_DiagnosticDataON /PrepareAllDomains
or
Setup.exe /IAcceptExchangeServerLicenseTerms_DiagnosticDataOFF /PrepareAllDomains
This is the step that is missed in many of the customer environments that I have recently seen. There is an assumption that since the security update was installed that's it. In most cases yes that is correct, but not here. There is more work to do.
Below are lab screenshots detailing the issue, remediation and showing completion.
Lab Environment
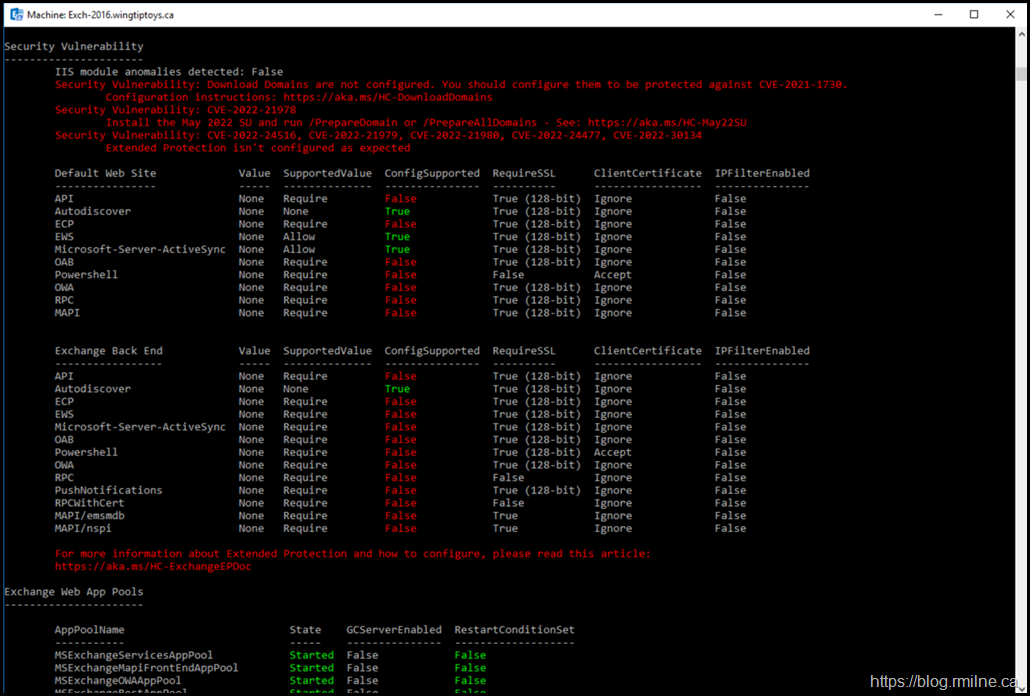
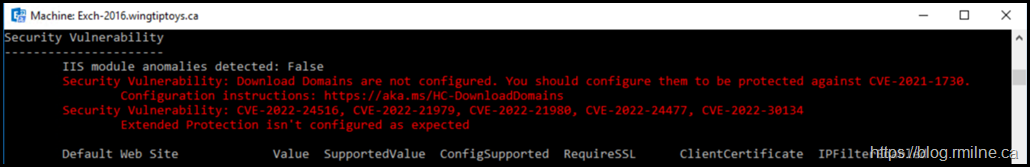
This is an Exchange 2016 CU23 based lab. It consists of a single AD DS Forest with a single domain. All Exchange security updates have been installed. However the HealthChecker script has detected that there are three security issues. These are:
- Download Domains
- Extended Protection
- May 2022 Security (Update requires /PrepareAD)
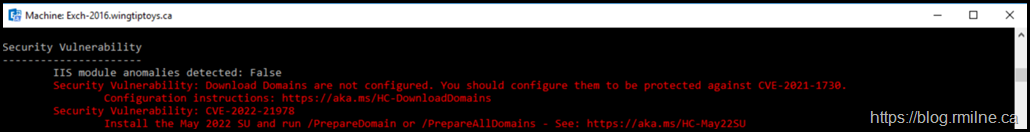
If we zoom in on just the last security issue we see:
Remediating Issue
Since this is a single domain lab, we only need to run /PrepardAD. If you have multiple domains with Exchange objects then you can run /PrepareAllDomains once or repeate /PrepareAD for each domain.
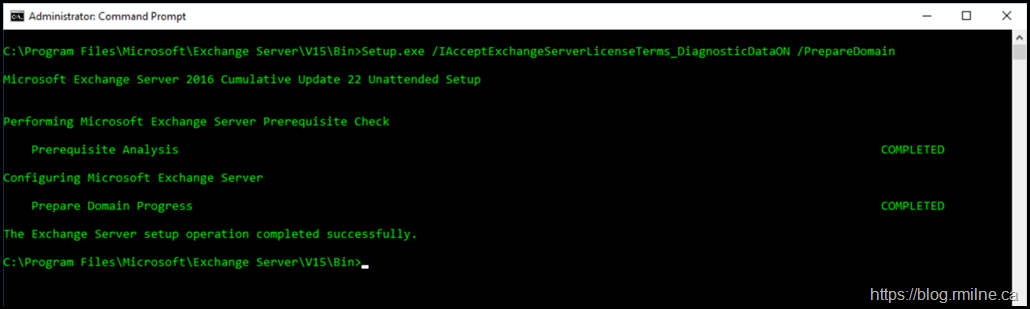
In light of the common Exchange CU mistakes to avoid post, we will perform this action in an elevated cmd prompt.
Setup.exe /IAcceptExchangeServerLicenseTerms_DiagnosticDataON /PrepareDomain
Why an elevated cmd prompt? The details are in the CU mistakes to avoid post. People run the command in PowerShell and hope to get this
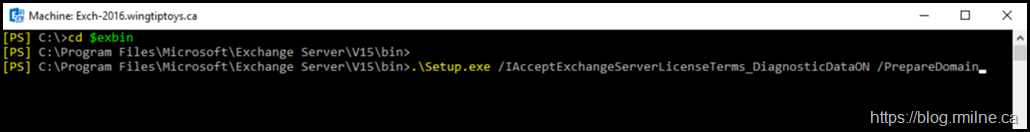
.\Setup.exe /IAcceptExchangeServerLicenseTerms_DiagnosticDataON /PrepareDomain
But in most cases they forget to start the PowerShell command with the required .\ syntax. Note though that we can cheat a little and use the Exchange Management Shell’s variable called $EXBin.
Verify Change Complete
Once the /PrepareAD command completes and AD replicates we verify that the issue is no longer reported by the HealthChecker script.
One issue down. Two to go.
To address the other issues please see these posts:
Cheers,
Rhoderick