Controlling connections to Azure VMs using the just in time (JIT) policy of Microsoft Defender for Cloud (MDC) certainly improves the overall security of the Azure resource. However, then having to enable JIT on a given VM runs into issues pretty quickly.
Azure Portal Too Permissive
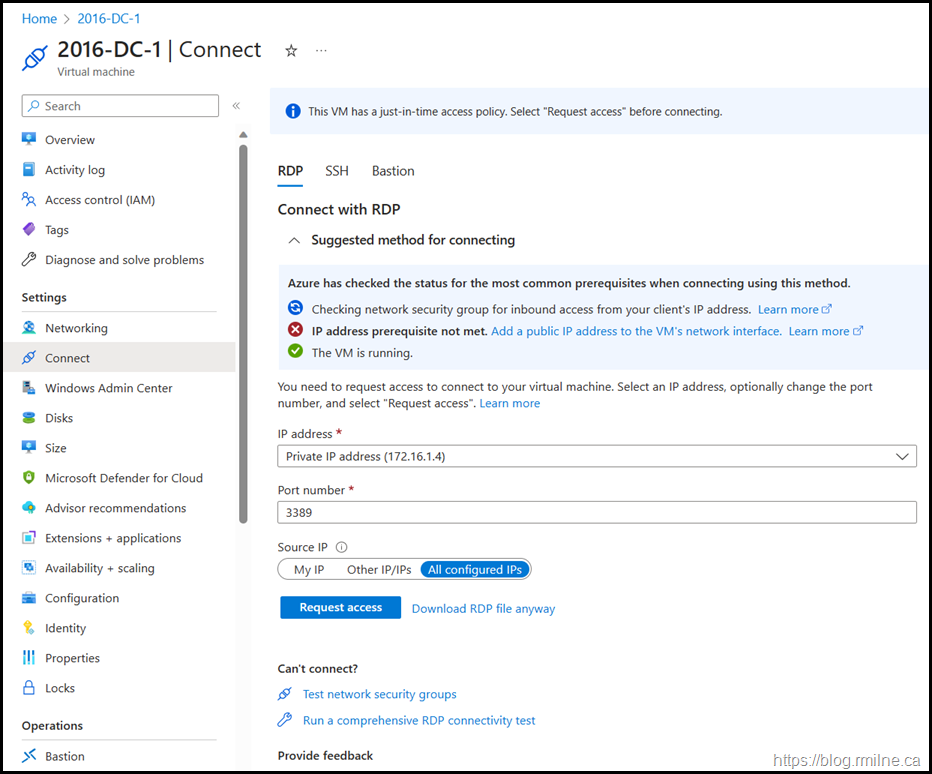
Who thought it was a great idea to have “All configured IPs” as the default option? No thanks – I do not want to enable RDP to the Internet…..
MDC Portal Lacks Detail
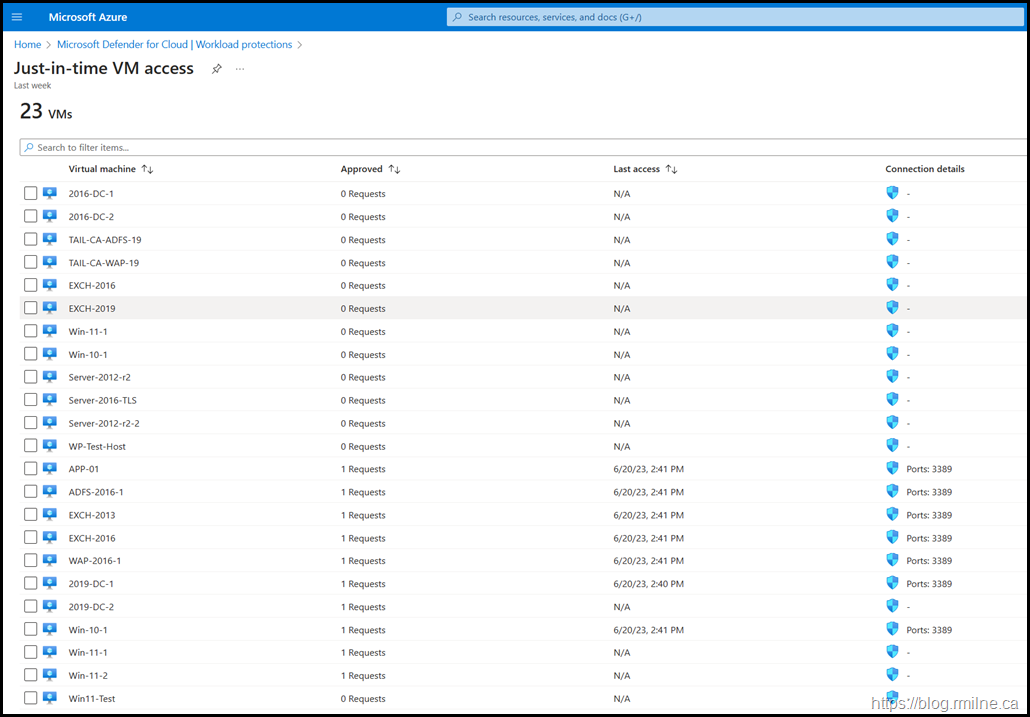
The MDC portal does not indicate which resource group a given VM actually belongs to. Unless there is a unique name per VM, you are guessing.
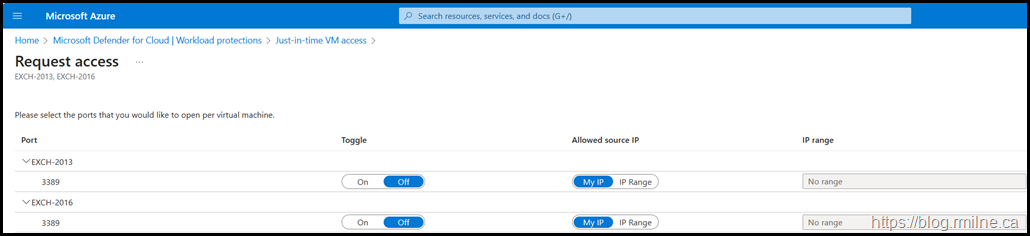
In addition to the lack of clarity, multiple clicks are required to select the VMs to enable then toggle the connection per VM to enable it.
At least this portal defaults to “My IP”…..
Azure PowerShell Is Gnarly
As we have seen the UI is not fantastic for its intended purpose. So what about using PowerShell?
Regrettably it has the same issue – it is not as easy as it really should have been. It is NOT as simple as just saying “Hey, enable that thing I already configured for the next hour from my IP”.
You need to define the VM access request policy, squirrel that into an array and finally send the access request to the VM.
This noted in the documentation to allow connections to Azure VMs via PowerShell. It has three discrete steps:
1 - Configure the VM request access policy properties
$JitPolicyVm1 = (@{
id="/subscriptions/SUBSCRIPTIONID/resourceGroups/RESOURCEGROUP/providers/Microsoft.Compute/virtualMachines/VMNAME";
ports=(@{
number=3389;
endTimeUtc="2020-07-15T17:00:00.3658798Z";
allowedSourceAddressPrefix=@("131.107.2.200")})})
2 - Insert the VM access parameters in an array
$JitPolicyArr=@($JitPolicyVm1)
3 - Send the request access using the resource ID from step #1
Please note the below is one line that will most likely wrap.
Start-AzJitNetworkAccessPolicy -ResourceId "/subscriptions/SUBSCRIPTIONID/resourceGroups/RESOURCEGROUP/providers/Microsoft.Security/locations/LOCATION/jitNetworkAccessPolicies/default" -VirtualMachine $JitPolicyArr
Making This A Bit Easier…
While we can tweak the request policy so it is a single line, that's just cosmetic and is only one VM. How do we represent multiple VMs, or all of them in a given Resource Group?
And this is something that you probably will be using multiple times, so how about we automate this using PowerShell as simply as we can?
Download the sample script from GitHub. You can edit that locally before uploading to Azure Cloud Shell or using Cloud shell’s native editor. Choice is yours.
You will want to edit the variable that defines the Resource Group. Additionally the public IP options should also be reviewed. If you plan to use Cloud Shell, the IP variable can be directly specified.
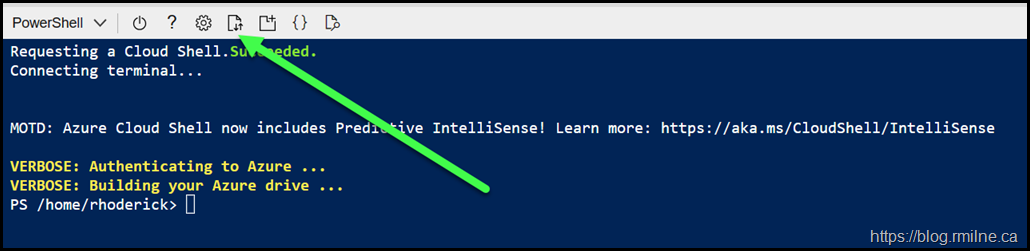
Once the changes have been made, hit the upload button to upload to Cloud Shell, this is shown below with the green arrow. Remember Azure Cloud Shell is based on Linux so case sensitivity matters for file uploads and downloads!
For more details on the file storage please see Persist files in Azure Cloud Shell | Microsoft Learn.
Errors
If the access request exceeds the allowed policy then you will not be able to sucessfully submit the JIT request. Reduce the time so that it is allowed by the policy limit.
Bootnote
Note that you must have configured the access policy and enabled JIT for the VM as well. That can be done via the portal, PowerShell or Graph.
But again PowerShell does not make this easy. Some comments on the timespan for the request policy. The values for maxRequestAccessDuration are currently:
-
-
Minimum 5 minutes
-
-
-
Maximum 24 Hours
-
-
-
Specify the time in ISO 8601 duration format
-
More on ISO 8601 here. If you want to easily render a date time value into UTC using Get-Date, please note that PowerShell 7 is needed for the -AsUTC paramater of Get-Date or use Azure Cloud shell
Cheers,
Rhoderick