After upgrading Web Application Proxy (WAP) to Windows Server 2019 you may run into an issue with certain applications that are published via WAP to the Internet.
In the below example the AD FS upgrade went well with no issues. The AD FS farm and WAP servers were upgraded to Windows Server 2019 and all appeared to be going well. Too well that was, as when the external tests were validated against WAP 2019 they did not sucessfully complete.
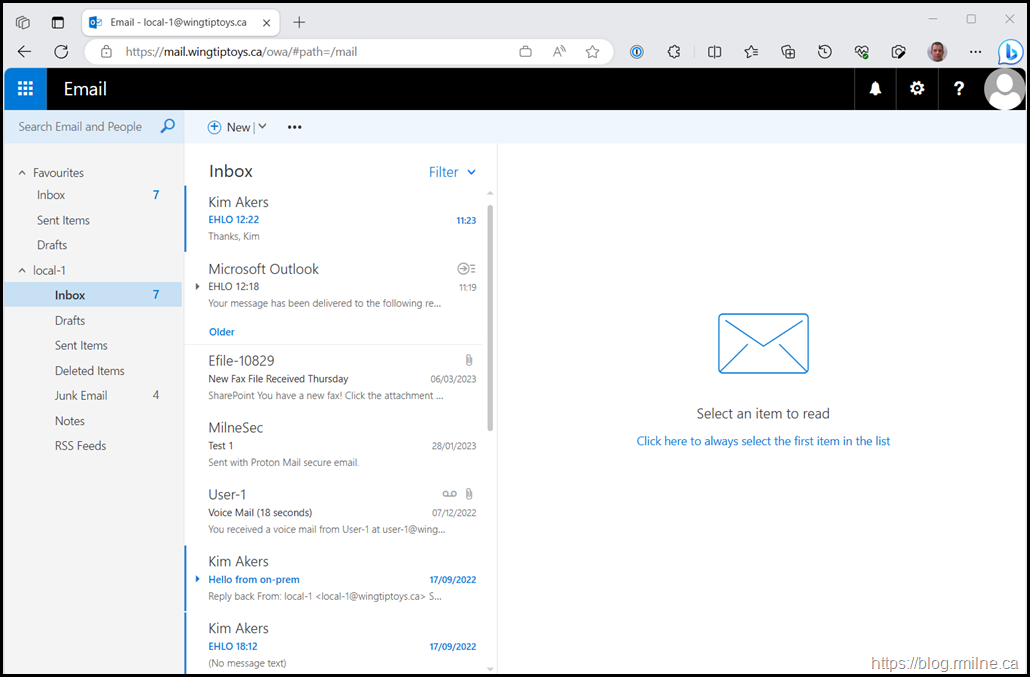
The initial logon to OWA was fine and the user could authenticate with no issues. But after the authentication was complete, the page just say there with a “Still working on it…” message.
Everything was fine internally. Outlook and OWA would load for this account with no issues.
Since WAP is responsible for publishing OWA to the Internet, what is up on those machines?
Initial Troubleshooting
Some of the initial items that were reviewed:
-
All WAP and AD FS services were running
-
No errors were logged
-
The correct certificates were installed with the necessary private key. The certificates also chained as expected
-
No issues internally at all. Only via WAP. This was confirmed to help isolate the issue
-
Servers fully patched
-
Expected firewall rules in place
-
WAP able to retrieve configuration from AD FS with no issues
WinHttp Issues On Windows Server 2019
After experiencing issues with Windows Server 2019 and WinHttp when deploying Azure AD App Proxy in a separate engagement, that could also cause issues here as well if the client and server could not negotiate as expected.
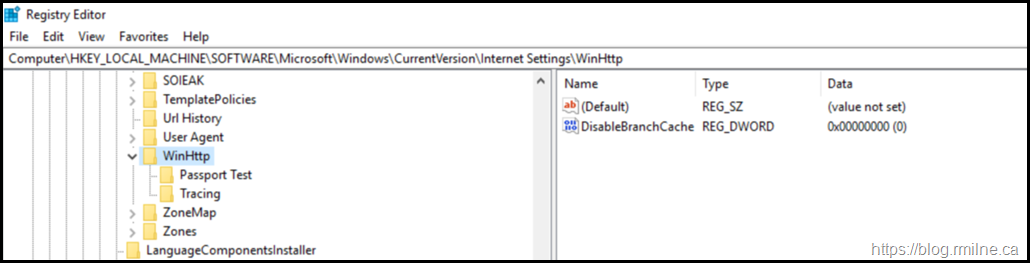
By default, the key to disable WinHttp is not present. This is shown below:
It can be added manually or by Using PowerShell:
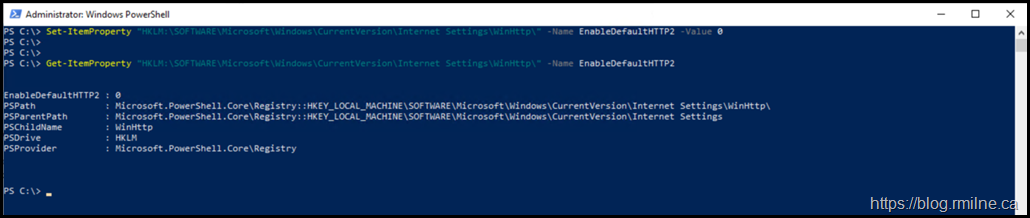
Set-ItemProperty “HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp\” -Name EnableDefaultHTTP2 -Value 0
In the above example, we then check that the value was added with a value of zero.
Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp\" -Name EnableDefaultHTTP2
After adding the registry value, restart the server. Repeat for the other WAP servers.
Relief Obtained
After restarting the WAP servers, the external clients were then able to access OWA with no issues.
OWA would load as expected.
Additional Relief Obtained
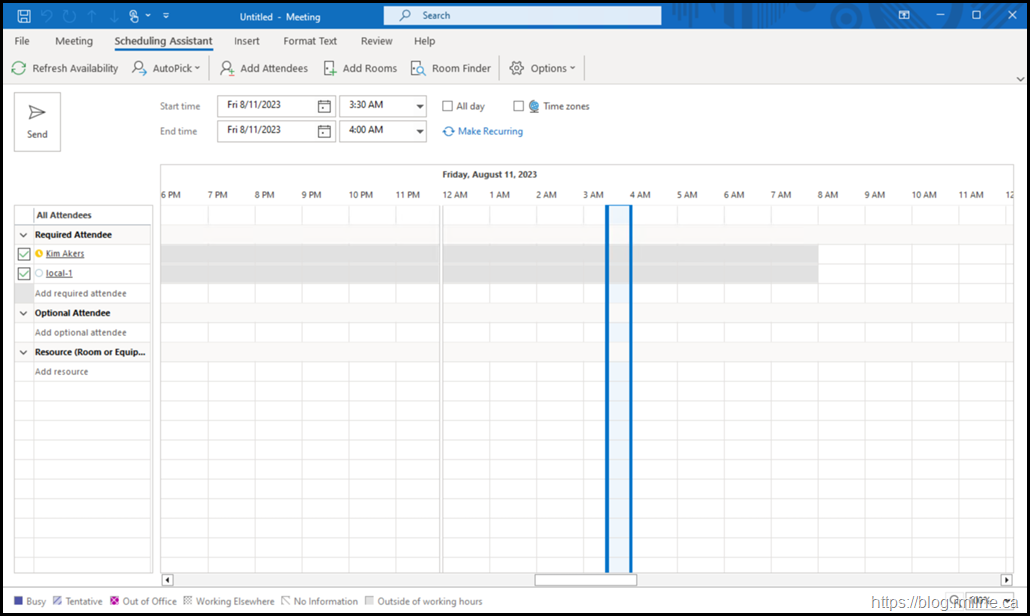
A separate issue was previously noted where Exchange Online users were unable to obtain free/busy information for on-premises mailboxes. That was parked until the OWA issue was resolved.
Well, it was the same issue. Disabling HTTP2 on WAP also corrected this issue.
It is likely that additional products will be affected by this. Some examples may include:
- SharePoint 2016
- Skype for Business 2016 and 2019
- Office Online Server
- Remote Desktop web client
Cheers,
Rhoderick