Unfortunately waves of spam from various onmicrosoft.com domains are a thing. The volume waxes and wanes over time, but this was an annoyance many years ago and remains so even today. Given that any meaningful organisation on the Internet will have their own brand and identity, it is highly unlikey that legitimate email from customers and partners will originate from an onmicrosoft.com address. There will be some very small shops which do send from their onmicrosoft.com domain, but those folks are in the definite minority. But it does happen!
Rather than suffer through yet more tranches of spam from these domains, how about we block it?
Before we start to block there are a few things to do:
- Initial review of senders using onmicrosoft.com domains
- Update the domain used by M365 products to send emails to your users
- Ensure your postmaster address has been changed
- Many other tenants will NOT have changed their postmaster address so we may want to exclude those from our planning exercise
- Plan how to monitor the change. Do not want to negatively impact the environment
EOP Background Notes
Assumption is that you are aware of how EOP routes messages and how connectors function. The below are included for awareness. Skip if you have not reviewed.
Office 365 Message Attribution
Advanced Office 365 Routing: Locking Down Exchange On-Premises when MX points to Office 365
Set up connectors to route mail between Microsoft 365 or Office 365 and your own email servers
Bypassing 3rd Party Mail Gateway
Note that if your MX record does NOT point to EOP, then you should have already blocked systems on the Internet from sending directly to the tenant.
Manage mail flow using a third-party cloud service with Exchange Online | Microsoft Learn
For those cases where the MX points to a 3rd party solution, it would be expected to see a connector created along the lines of:
New-InboundConnector -Name "Block Direct Delivery" -ConnectorType Partner -SenderDomains * -TlsSenderCertificateName *.wingtiptoys.ca -RestrictDomainsToCertificate $true -RequireTls $true
That would look something like this:
Name SenderDomains SenderIPAddresses Enabled
---- ------------- ----------------- -------
Block Direct Delivery {smtp:*;1} {} True
Note that you could also restrict via an IP address. Using either RestrictDomainsToCertificate or RestrictDomainsToIPAddresses can be used depending on the environment.
Initial Review Of Senders Using onmicrosoft.com Domains
There are a few ways to do this. This is not meant to be an exhaustive list.
Advanced Hunting
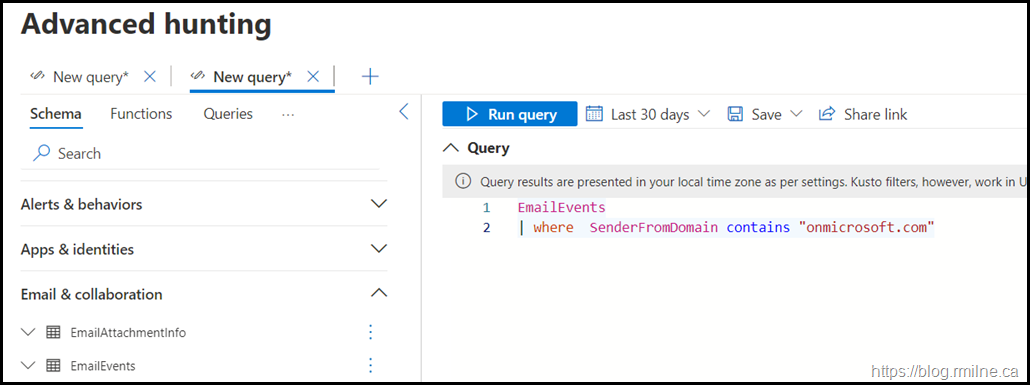
Given all of the recent work I've been doing with Defender, this is now my preference. It is very quick and convenient!
If you have MDO Plan 2 then Kusto Query Language (KQL) can be used to rapidly hunt through the data.
The below is very simply KQL that will show incoming email from the onmicrosoft.com domain. This can be fleshed out to suit.
EmailEvents | where SenderFromDomain contains "onmicrosoft.com"
Note that the time filter is set to 30 days in the UI – change that to suit or add in the ago KQL function.
Some examples to make the base query a bit more useful:
Filter Out Your Tenant’s OnMicrosoft.com Domain
EmailEvents
| where Timestamp > ago(30d)
| where SenderFromDomain contains "onmicrosoft.com"
| where SenderFromDomain !contains "wingtiptoyscanada.onmicrosoft.com" // Change to your tenant domain
Review DeliveryAction Action Taken
DeliveryAction could be Delivered, Junked, Blocked or Replaced. You can get this by looking at the table’s schema.
EmailEvents
| where Timestamp > ago(30d)
| where SenderFromDomain contains "onmicrosoft.com"
| where SenderFromDomain !contains "wingtiptoyscanada.onmicrosoft.com" // Change to your tenant domain
| where DeliveryAction == 'Delivered'
Filter On Certain Columns
EmailEvents
| where Timestamp > ago(30d)
| where SenderFromDomain contains "onmicrosoft.com"
| where SenderFromDomain !contains "wingtiptoyscanada.onmicrosoft.com" // Change to your tenant domain
| where DeliveryAction == 'Delivered'
| project SenderFromAddress, SenderFromDomain, SenderDisplayName, Subject, DeliveryAction
Summarise By Count of DeliveryAction
EmailEvents
| where Timestamp > ago(30d)
| where SenderFromDomain contains "onmicrosoft.com"
| where SenderFromDomain !contains "wingtiptoyscanada.onmicrosoft.com" // Change to your tenant domain
| where DeliveryAction == 'Delivered'
| project SenderFromAddress, SenderFromDomain, SenderDisplayName, Subject, DeliveryAction
| summarize count() by DeliveryAction
Ignore Postmaster Addresses
EmailEvents
| where Timestamp > ago(30d)
| where SenderFromDomain contains "onmicrosoft.com"
| where SenderFromDomain <> "wingtiptoyscanada.onmicrosoft.com" // Change to your tenant domain
| where SenderFromAddress !has "postmaster"
| where DeliveryLocation != "Blocked"
| project SenderFromAddress, SenderFromDomain, SenderDisplayName, Subject, DeliveryAction
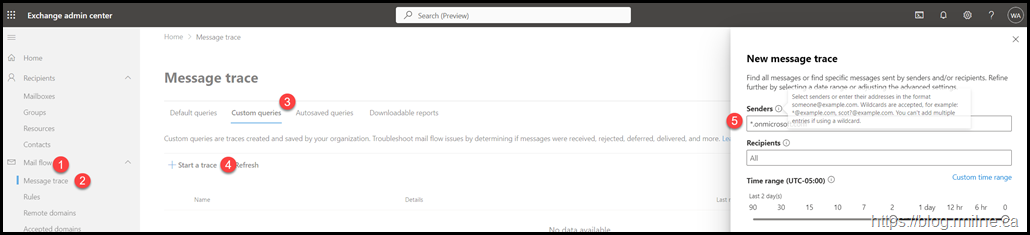
Exchange Message Trace
If you do NOT have the required licenses for Advanced Hunting, then we can use Exchange Message Trace.
Navigate to Mail Flow, Message Trace then Custom Queries and click “+Start a trace”. In the right hand pop-up window you can enter a domain to search for.
In the screenshot below, the mouse over text on the information icon is displayed. Note that only a single wildcard is permitted, and the UI is not very flexible.
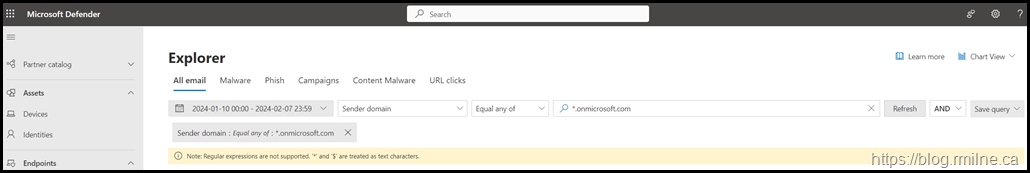
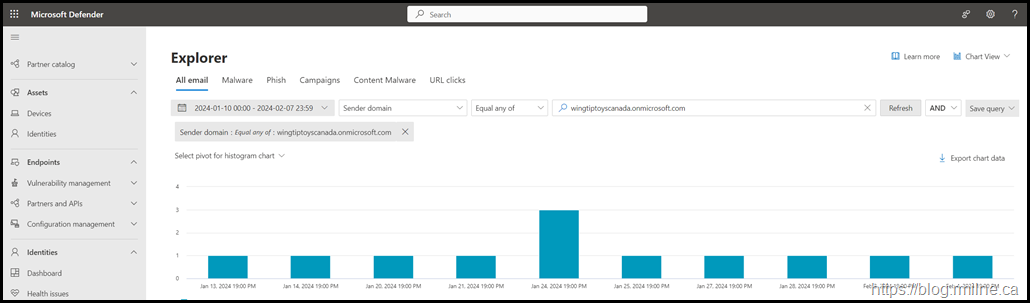
Threat Explorer
Note that this also a MDO P2 feature.
The Sender Domain requires an exact match. Wild cards are not accepted in the domain field 🙁
Select Domain Used For Email From M365 Products
Multiple components in M365 send out legitimate emails to you and your users. For example a “no-reply” style of address is used to send news, comments, system notification emails. They could be addresses such as:
no-reply@sharepointonline.com, no-reply@planner.com, no-reply@project.com
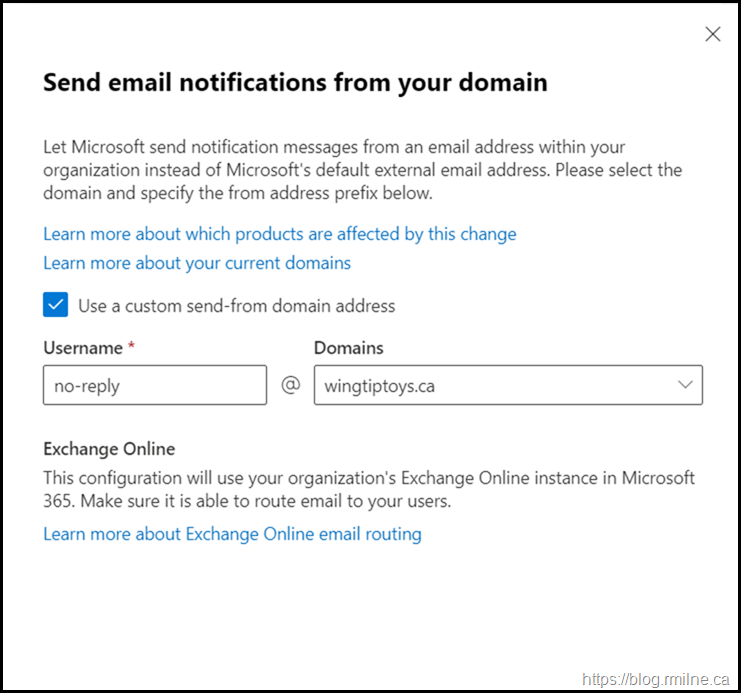
They are received as external notifications by default, though this can be changed to something like no-reply@wingtiptoys.ca and will be treated as internal communication.
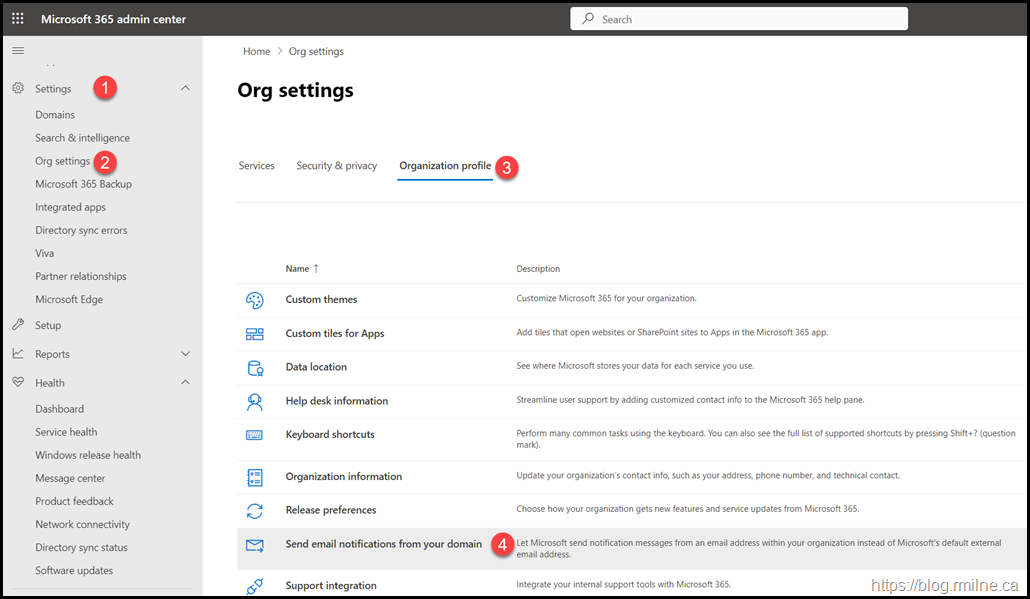
In the M365 Admin Portal (https://admin.microsoft.com) go to Settings, Org Settings, Organisation Profile then “Send email notifications from your domain”.
Enter your desired no-reply address:
Then click Save.
Please note that there is a limited list of products that support this change - they are documented here.
Postmaster Consideration
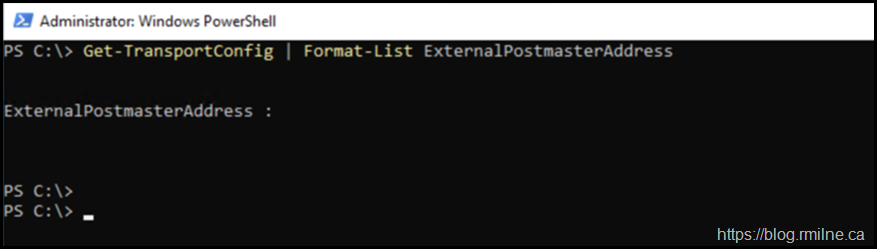
By default, the external postmaster address will be postmaster@<tenantname>.onmicrosoft.com and this really should have been changed.
Connect to Exchange Online PowerShell and run:
Get-TransportConfig | Format-List ExternalPostmasterAddress
If the entry is blank then you are using the default address. Time to change that!
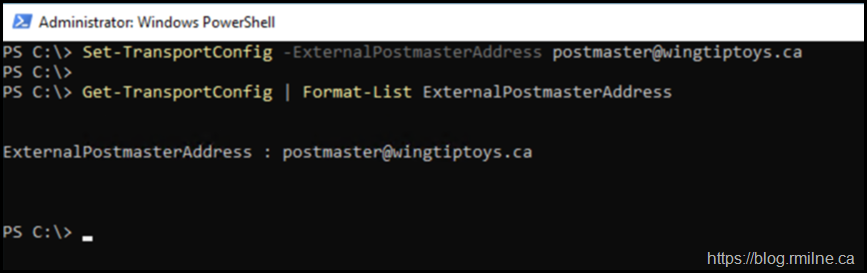
For example:
Set-TransportConfig -ExternalPostmasterAddress postmaster@wingtiptoys.ca
Ensure that the mailbox exists so you can monitor it. The command will allow you to set a random address.
Now that we have looked at the starting situation, time to move on a create an Exchange Transport Rule!
Create Exchange Transport Rule Via PowerShell
The below example create an Exchange Transport Rule (ETR) that moves email from onmicrosoft.com domains to the quarantine. Note that the rule is set to a disabled state by default, so you will need to enable it. The rule’s mode is set to audit so you have the opportunity to review its behaviour before changing it to Enforce.
Also to err on the side of caution, there is an exemption for your tenant’s onmicrosoft.com domain.
To summarise:
- The rule mode is audit. Change to Enforce only when ready and the rule's behaviour has been evaluated
- Change the tenant name exclusion to your tenant
- Change the rule priority accordingly
- Only when happy with the settings, enable the rule
New-TransportRule -Name "Block Delivery From onmicrosoft.com Domains" -Enabled $False -Mode Audit -Quarantine $True -SetAuditSeverity Low -FromAddressMatchesPatterns "onmicrosoft.com" -ExceptIfFromAddressMatchesPatterns "wingtiptoyscanada.onmicrosoft.com" –Comments “Rule to Block External onmicrosoft.com Traffic”
If you wanted to apply to messages sent from outside of the organisation:
New-TransportRule -Name "Block Delivery From onmicrosoft.com Domains" -Enabled $False -Mode Audit -Quarantine $True -SetAuditSeverity Low -FromAddressMatchesPatterns "onmicrosoft.com" -FromScope "NotInOrganization"-ExceptIfFromAddressMatchesPatterns "wingtiptoyscanada.onmicrosoft.com" –Comments “Rule to Block External onmicrosoft.com Traffic”
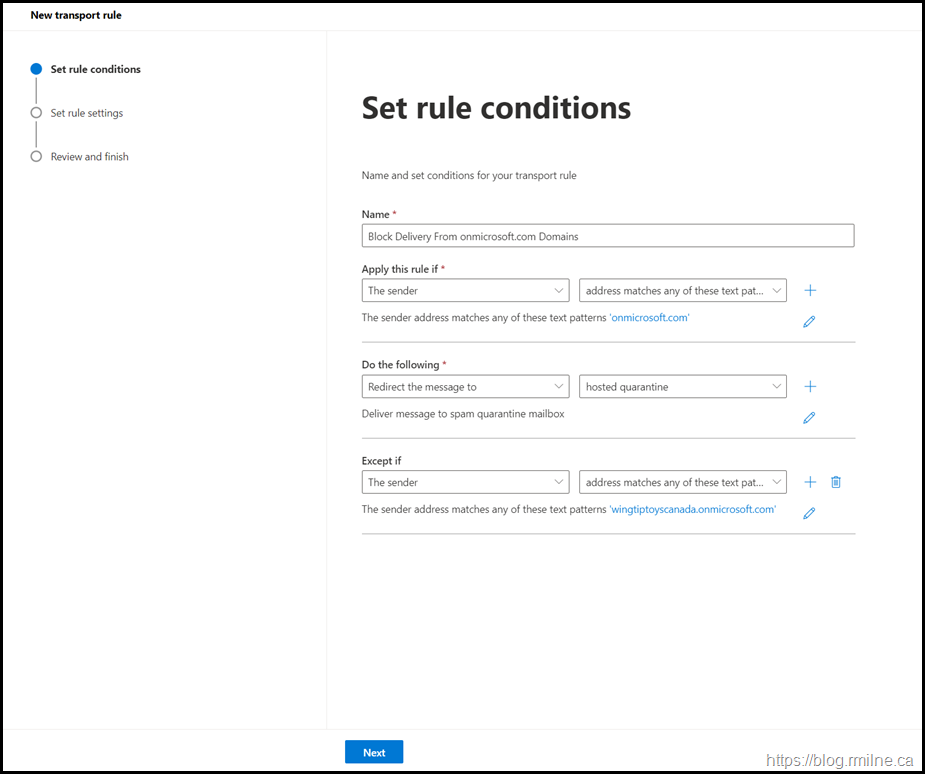
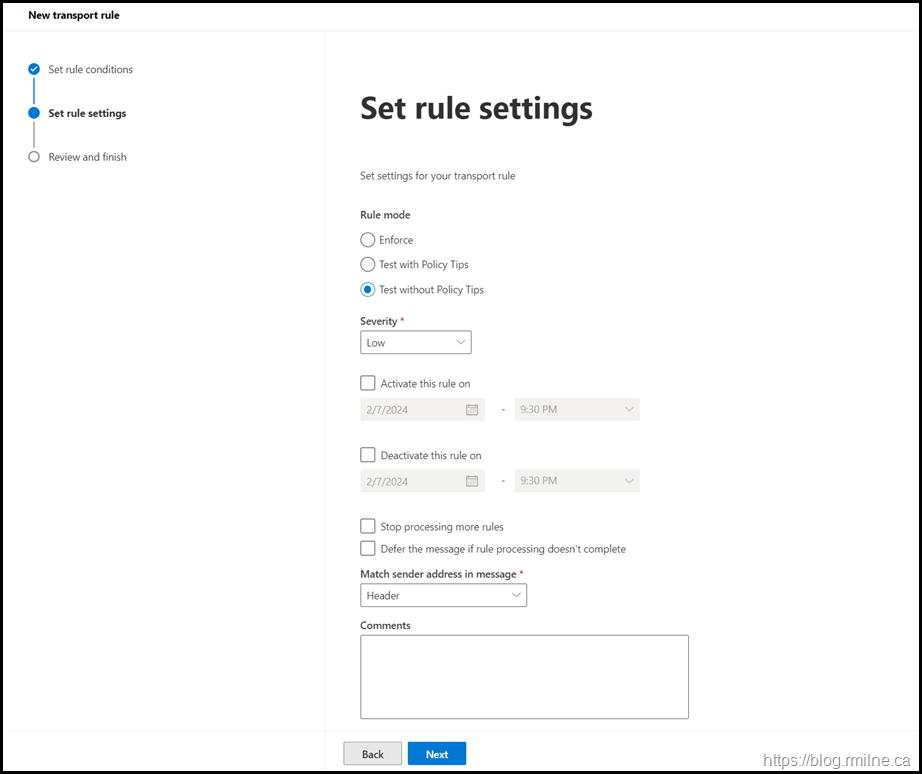
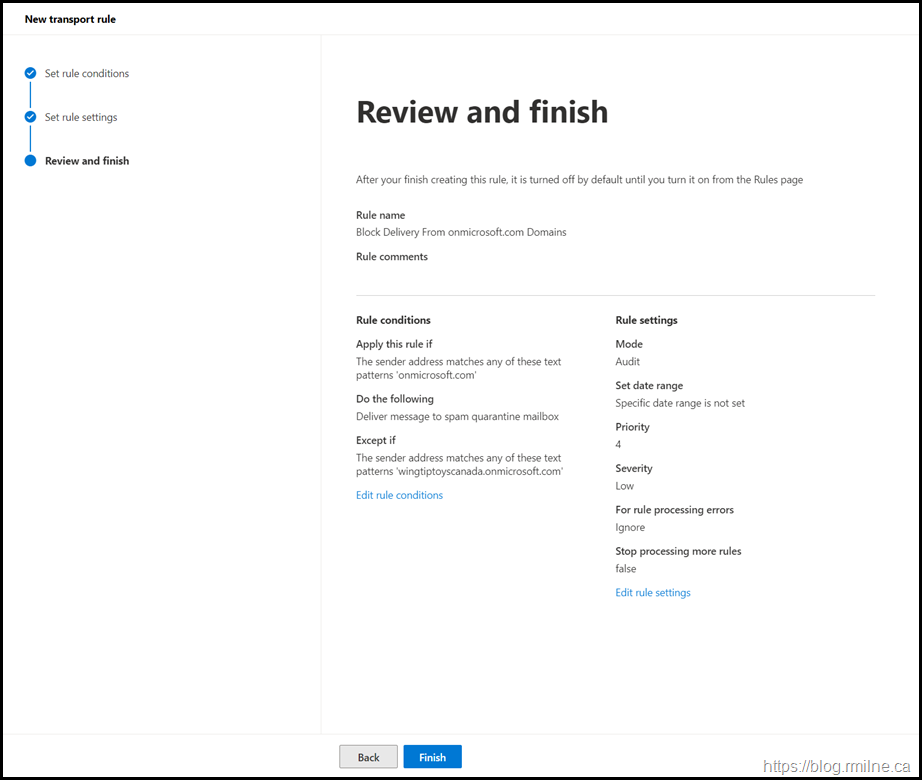
Create Exchange Transport Rule Via UI
If you want to use the Exchange Admin Centre, then you can mimic the settings below.
As noted above:
- The rule mode is audit. Change to Enforce only when ready
- Change the tenant name exclusion to your tenant
- Change the rule priority accordingly
- When happy with the settings, enable the rule
Bootnote
In the above examples, and they are just that, the detected messges were yeeted to the quarantine so that they are not totally discarded. No NDR was sent back to the originator. As part of your implementation you can determine what you want to do in your environment.
Reviewing Contents of Quarantine
You can go directly to the quarantine using the link below.
https://security.microsoft.com/quarantine
Cheers,
Rhoderick