Install the Microsoft Defender for Identity (MDI) sensor onto a newly built DC? Easy you say, and that should only take 5 minutes. Well, if that was the case there would be no need for this post, and as my Dad would say, there is no such thing as a 5 minute job.
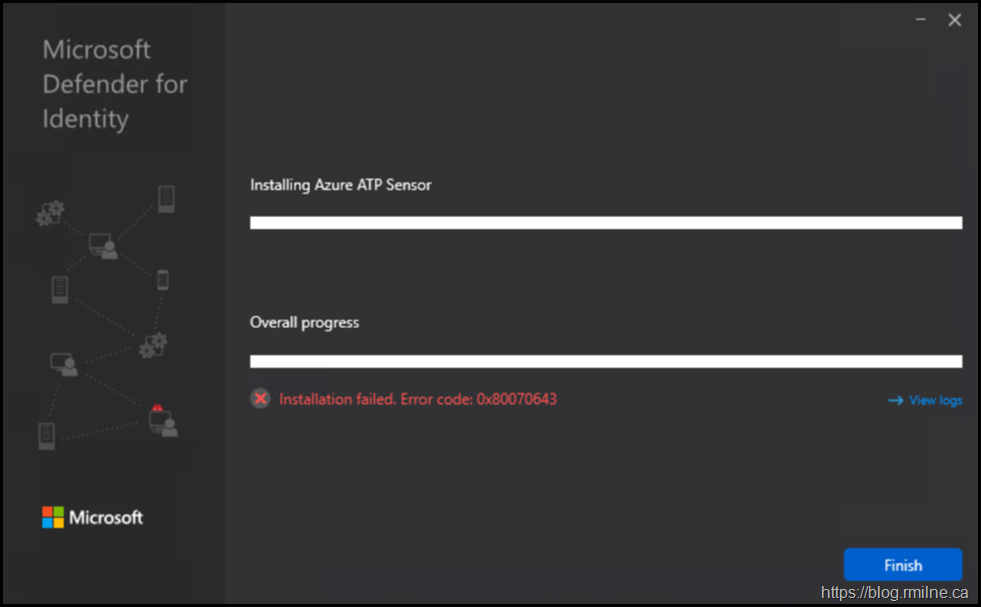
The below is a brand new Windows Server 2019 DC. It was built, fully patched and then promoted. Next up is to install the standard Microsoft Defender components, in this case the Microsoft Defender for Identity (MDI) sensor was installed first. That did not go so well, and we got error 0x80070643.
The server would show up briefly in the MDI Console, as the sensor tried to install, and then disappear as the install was backed out since it failed.
You can see that in the animated GIF below. Maybe play this song as you watch it?
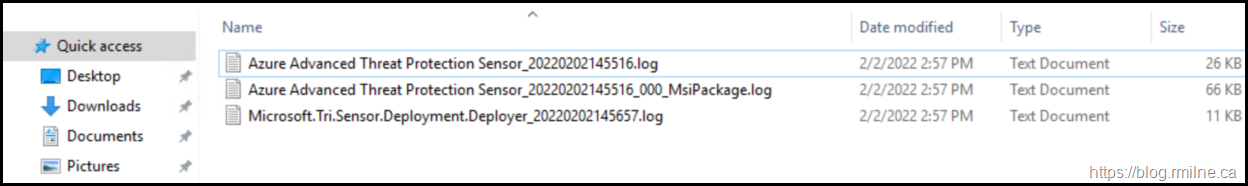
Clicking the view logs link in the install screen takes us to the %TEMP% location for my account, since it is running under my context. The full path is:
C:\Users\%UserName%\AppData\Local\Temp
Where we can see these three log files.
Error codes were visible, but no real data as to what caused it and a root cause.
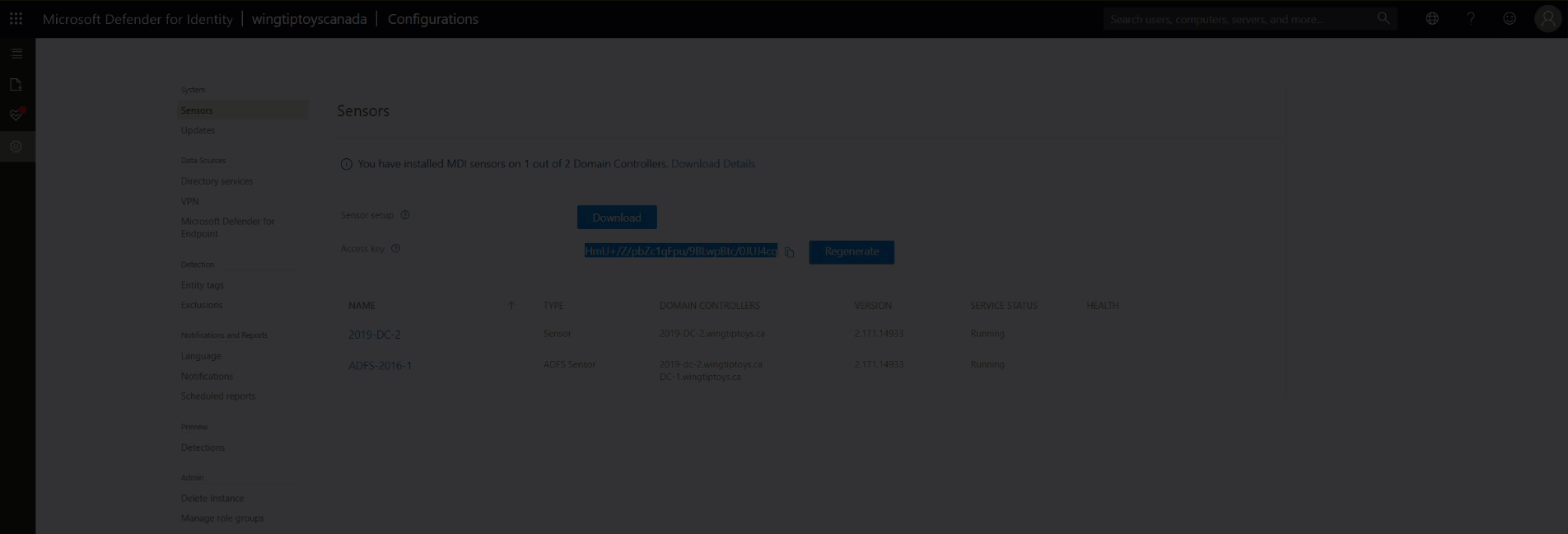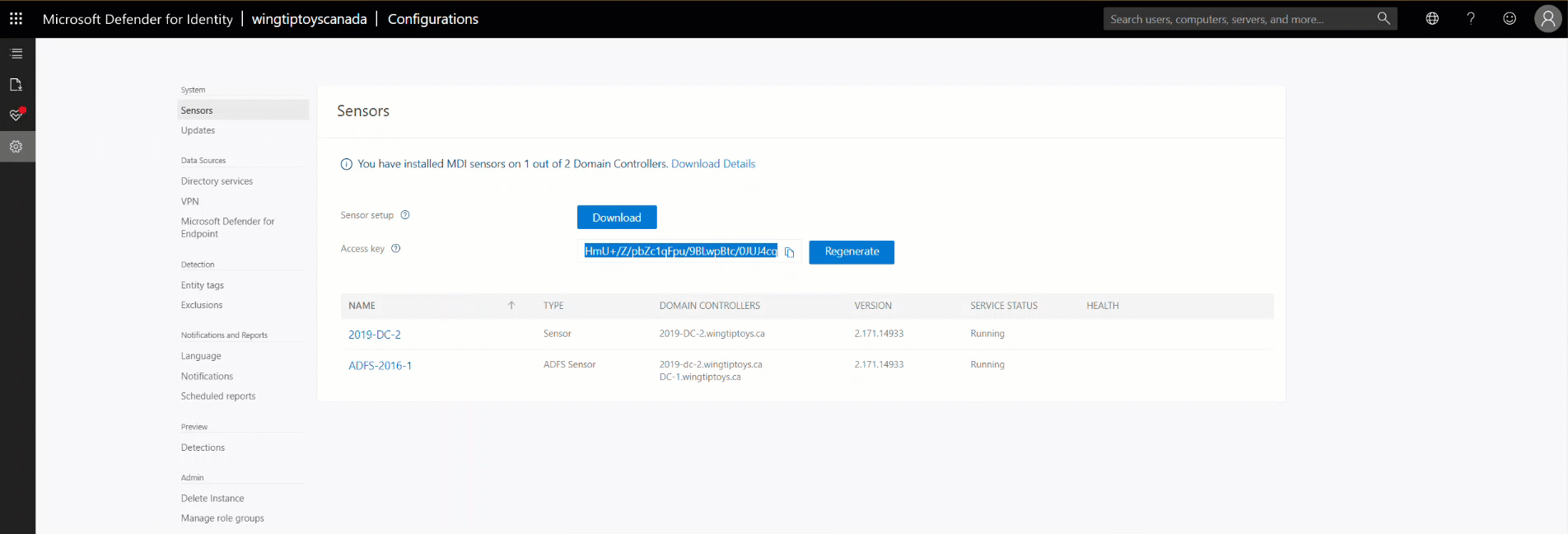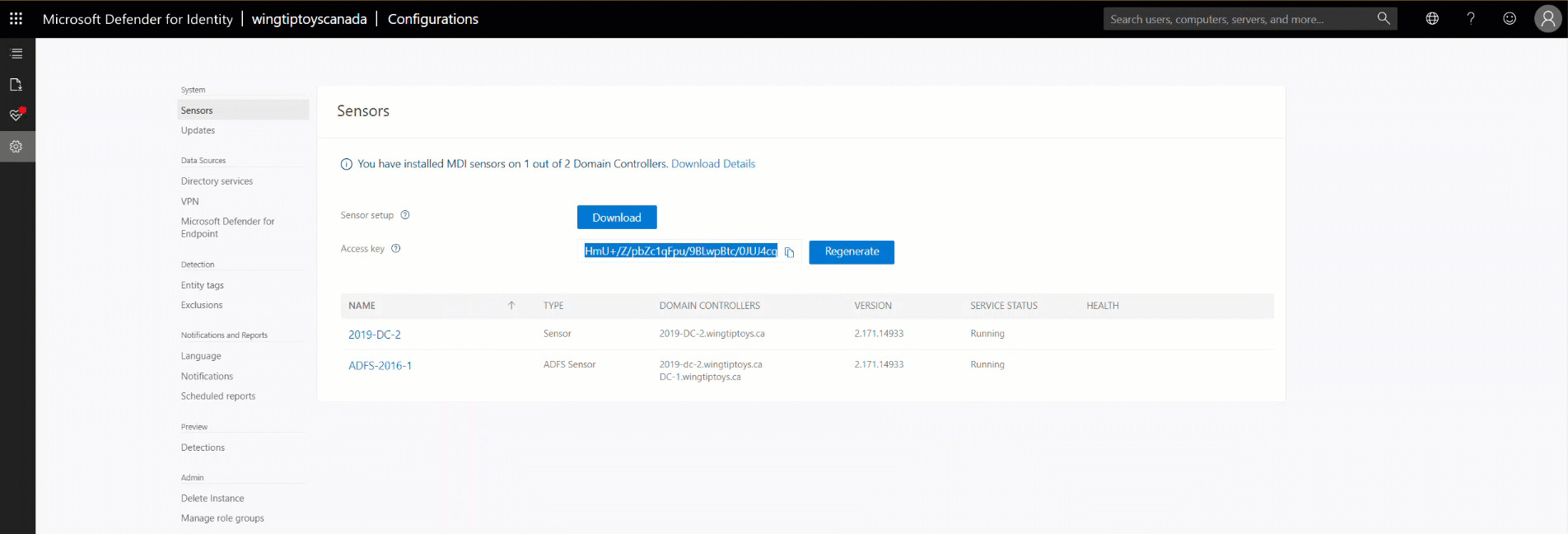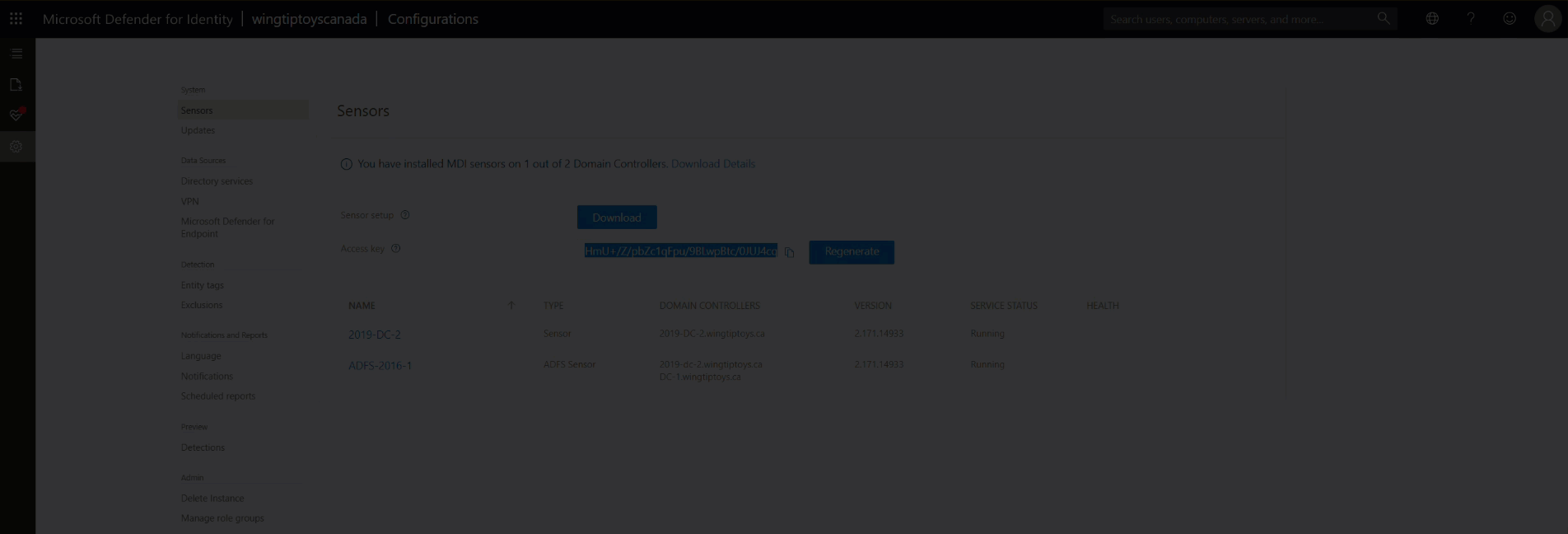
For example from the Sensor setup log we can see the error 0x80070643
[19D0:1E80][2022-02-02T14:56:47]i301: Applying execute package: MsiPackage, action: Install, path: C:\ProgramData\Package Cache\{71F587F0-93D5-47EE-A7BE-A47459662585}v2.0.0.0\Microsoft.Tri.Sensor.Deployment.Package.msi, arguments: ' ARPSYSTEMCOMPONENT="1" MSIFASTINSTALL="7" ACCESSKEY="*****" InstallationPath="C:\Program Files\Azure Advanced Threat Protection Sensor" InstalledVersion="" PROXYCONFIGURATION="*****" WixBundleOriginalSourceFolder="S:\Source\MDI Install Package\Azure ATP Sensor Setup\"'
[19D0:1E80][2022-02-02T14:57:02]e000: Error 0x80070643: Failed to install MSI package.
[19D0:1E80][2022-02-02T14:57:02]e000: Error 0x80070643: Failed to execute MSI package.
[1854:2214][2022-02-02T14:57:02]e000: Error 0x80070643: Failed to configure per-machine MSI package.
[1854:2214][2022-02-02T14:57:02]i000: 2022-02-02 14:57:02.5752 Error Model LogError [\[]methodName=BootstrapperApplication_ExecutePackageComplete status=-2147023293 exception=[\]]
[1854:2214][2022-02-02T14:57:02]i319: Applied execute package: MsiPackage, result: 0x80070643, restart: None
[1854:2214][2022-02-02T14:57:02]e000: Error 0x80070643: Failed to execute MSI package.
At the end of Deployer Log, an EventLogException Deployer failed message was logged. A couple of interesting things are highlighted.
Error EventLogException Deployer failed [arguments=ZBCwFTnuF52g2nKKvNKOdQ==]
System.UnauthorizedAccessException: Attempted to perform an unauthorized operation.
at void System.Diagnostics.Eventing.Reader.EventLogException.Throw(int errorCode)
at void System.Diagnostics.Eventing.Reader.NativeWrapper.EvtSaveChannelConfig(EventLogHandle channelConfig, int flags)
at bool Microsoft.Tri.Sensor.Deployment.Deployer.ConfigureVirtualServiceAccountAction.ApplyInternal()
at void Microsoft.Tri.Sensor.Common.DeploymentAction.Apply(bool suppressFailure)
at void Microsoft.Tri.Sensor.Common.DeploymentActionGroup.Apply(bool suppressFailure)
at int Microsoft.Tri.Sensor.Deployment.Deployer.Program.Main(string[] commandLineArguments)
This is interesting as it is an unauthourized access statement. If your audit policy is set to include failures, you will see an audit failure associated to the install. The Event log shows an Audit Failure getting the “Act as part of the operating system” (SeTcbPrivilege) privilege
The account running this is a full EA. Why?
Well this is a known issue on Windows Server 2019 with KB 5009557 installed.
The Windows update broke event viewer permissions to standard admin accounts.
The current workaround is to install the sensor in system context using either:
- PsExec -s to execute in system context
- Scheduled task set to run as LocalSystem
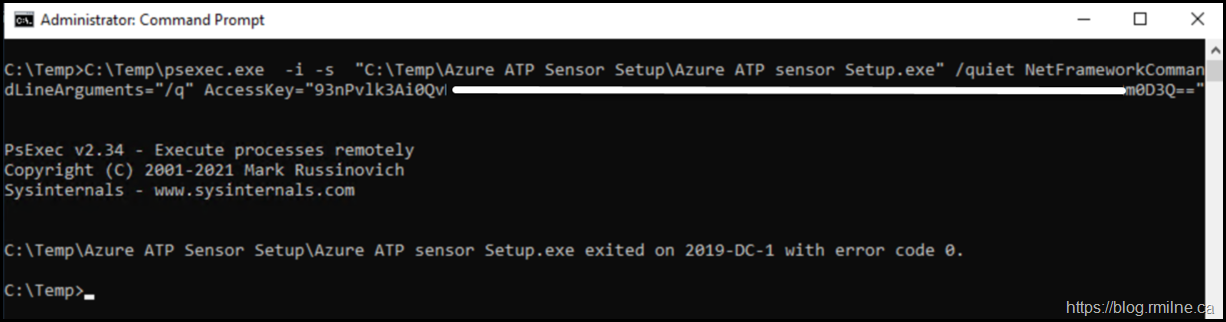
In the example below we will use PsExec.
Adding All The Permissions
This is an example of where the Sysinternals tools can be useful (yet again!).
To elevate to system context we can use PSExc.exe from the Sysinternals suite. Personally I prefer the https://live.sysinternals.com site to just grab what is needed.
PSExec was downloaded onto the system and it could be used as a one-liner or interactively.
Since we are installing using the command line, the Defender for Identity Silent option was used.
The syntax is:
"Azure ATP sensor Setup.exe" /quiet NetFrameworkCommandLineArguments="/q" AccessKey="<Access Key>"
In the example below, note that the AccessKey is redacted. It was also changed prior to publishing this post.
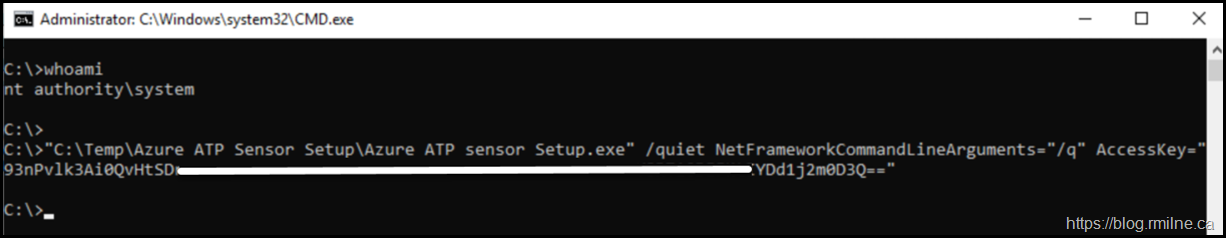
If you would prefer to run the command in an interactive manner, just launch a new cmd.exe process using PsExec as shown below.
The spawned CMD window will launch, and to prove that we are in system context, a WhoAmI was used prior to running setup.
Now that the sensor is finally installed, we can see it on the dashboard.
Assorted Troubleshooting Things
This post focusses on a particular issue with MDI and Windows Server 2019, but this is not the first time that error code has surfaced. There are multiple issues which may cause an error code such as this.
Some of the other MDI troubleshooting steps that I've used on other cases include:
-
Elevated cmd prompt - to mitigate UAC issues
-
Verified gMSA - ensure new DC has access to the credential
- Clear kerberos ticket cache if new machine added to gMSA
-
Chckdsk & SFCScan – ran full check and scan
-
Eliminate CBS corruption – DISM scan performed
- .NET Framework – Repair performed
-
PCAP – manually installed. Same issue
-
Re-Downloaded install package – install package not a corrupt download
-
Access key is correct
Cheers,
Rhoderick

Hi,
I was having the same problem and was reading your article for solutions.
When ever I try to run the Silent option command " "Azure ATP sensor Setup.exe" /quiet NetFrameworkCommandLineArguments="/q" AccessKey="" ",
I get the following message: "Azure ATP sensor Setup.exe"' is not recognized as an internal or external command, operable program or batch file.
Do you have any idea why this occured by any chance?
Thank you in advance,
Hey Shawn,
Are you using CMD or PowerShell?
Cheers,
Rhoderick
Hi,
I used CMD when this happened
However, I retried again and the installation went fine without using the script. (error 0x80070643 didnt pop up)
Not sure what the cause was..
Not sure what the problem was..
I suspect that would likely be a path issue, where it is not finding the package. SysInternals process monitor should show that, but since its good no need to worry this time.
PowerShell has the requirement to always fully qualify the path which is why I asked about that. Even if you change to the folder with the package you need to use the .\ prefix.
Cheers,
Rhoderick
Thanks a lot, same problem.
https://docs.microsoft.com/en-us/defender-for-identity/configure-proxy
Thank you very much, i have installed the agent as per your guide and the installation completed successfully.