A base Web Application Proxy (WAP) provides AD FS proxy capability in addition to also publishing on-premises web applications to the Internet. This can be used to publish services such as Exchange OWA and Autodiscover.
Publish Applications using AD FS Preauthentication can used in certain situations to pre-authenticate the incoming request before it is passed onto the internal server. Alternatively, pass-through can be used which will simply pass the traffic as-is to the destination server.
Some publishing examples are Using Application Proxy to Provide Access to SharePoint Server and Exchange Server. This is different from publishing using claims-based authentication which is an Exchange 2013 SP1 an newer feature and is documented in Using AD FS claims-based authentication with Outlook Web App and EAC.
In the case below, we are publishing OWA using the below namespace:
https://owa.tailspintoys.ca/owa
All was good, until a certificate was not renewed...
The below examples are from a Windows Server 2012 R2 WAP instance, though the process will be the same for newer versions. The name of the published application was as redacted, just in case you were wondering why there were so many spaces...
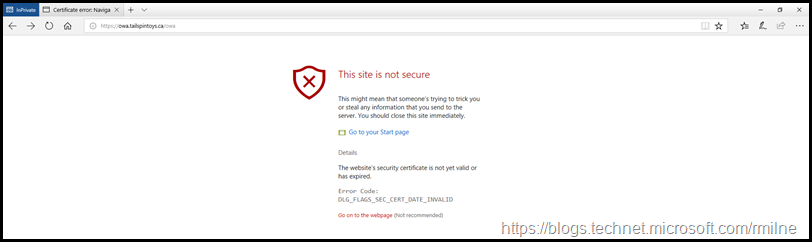
Expired Certificate
While it is expected that admins will renew certificates proactively, this is not always done. Sometimes the renewal process fails, and in other cases the certificate is renewed but some locations are missed.
Either way, there is user impact. The below are screenshots which are typical in this situation.
The SEC_CERT_DATE_INVALID message indicates that the valid from and valid to dates on the certificate have an issue.
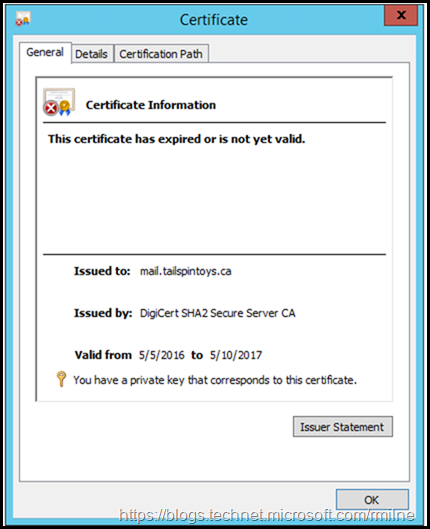
If we check the certificate store on a WAP server, it is clear that the certificate has expired.
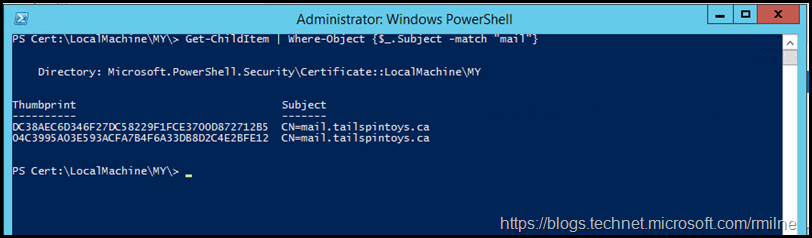
The thumbprint of the expired certificate is 04 c3 99 5a 03 e5 93 ac fa 7b 4f 6a 33 db 8d 2c 4e 2b fe 12.
We will come back and refer to this later in the post.
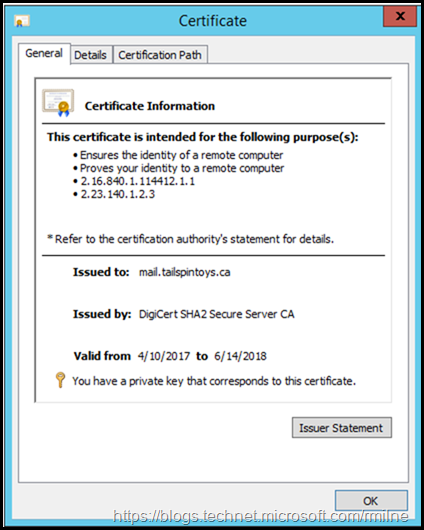
New Certificate Installed
A new certificate was installed and verified. Note that this must be done on all of the WAP servers. Certificates and the associated private keys are stored locally on each WAP server.
The published app configuration is shared between all WAP servers. This is because it is saved to the AD FS database, and each WAP server will periodically retrieve the configuration.
This new certificate has a thumbprint of: dc 38 ae c6 d3 46 f2 7d c5 82 29 f1 fc e3 70 0d 87 27 12 b5
Updating Published Application
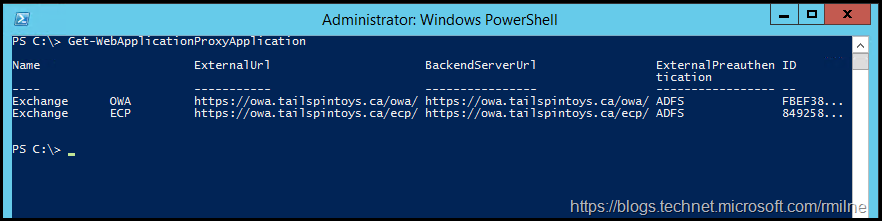
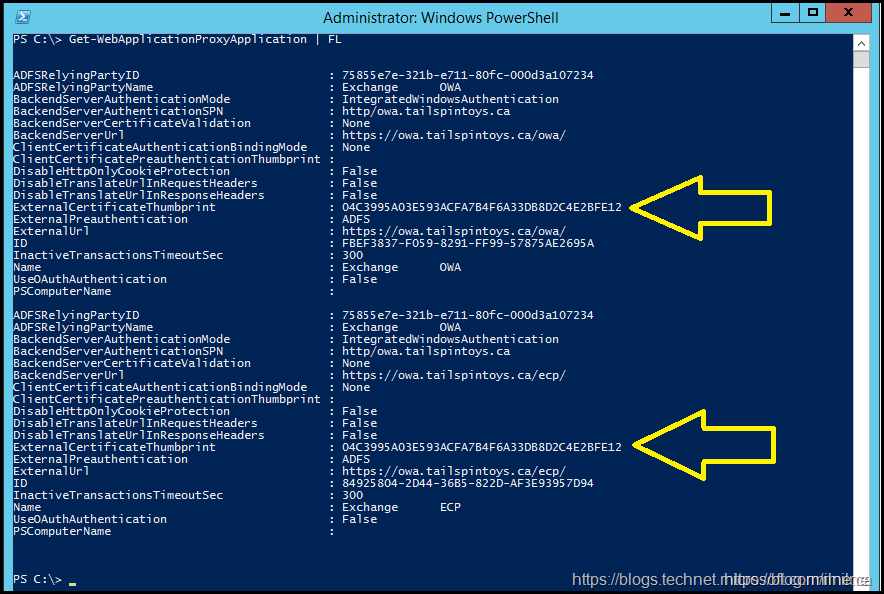
We can list the published applications using Get-WebApplicationProxyApplication cmdlet.
Get-WebApplicationProxyApplication
We can see there are two published applications /OWA and /ECP
We can see the certificate which is used for an application by looking at the detailed output from the cmdlet.
Get-WebApplicationProxyApplication | FL
As noted above:
The old certificate's thumbprint is: 04 c3 99 5a 03 e5 93 ac fa 7b 4f 6a 33 db 8d 2c 4e 2b fe 12
The new certificate's thumbprint is: dc 38 ae c6 d3 46 f2 7d c5 82 29 f1 fc e3 70 0d 87 27 12 b5
[note that when we reference the certificates in PowerShell, the spaces must not be present]
We can see these certificates in the local store. We could navigate to the CERT: PSDrive, the change to Cert:\LocalMachine\My and run the below command.
Get-ChildItem | Where-Object {$_.Subject -match "mail"}
Alternatively, use this post Easy Way To Retrieve Certificate Thumbprint Using PowerShell.
Updating Web Proxy Application
We can update the previously published application by running the Set-WebApplicationProxyApplication cmdlet.
The new certificate thumbprint will be referenced. This can be done as in the example below:
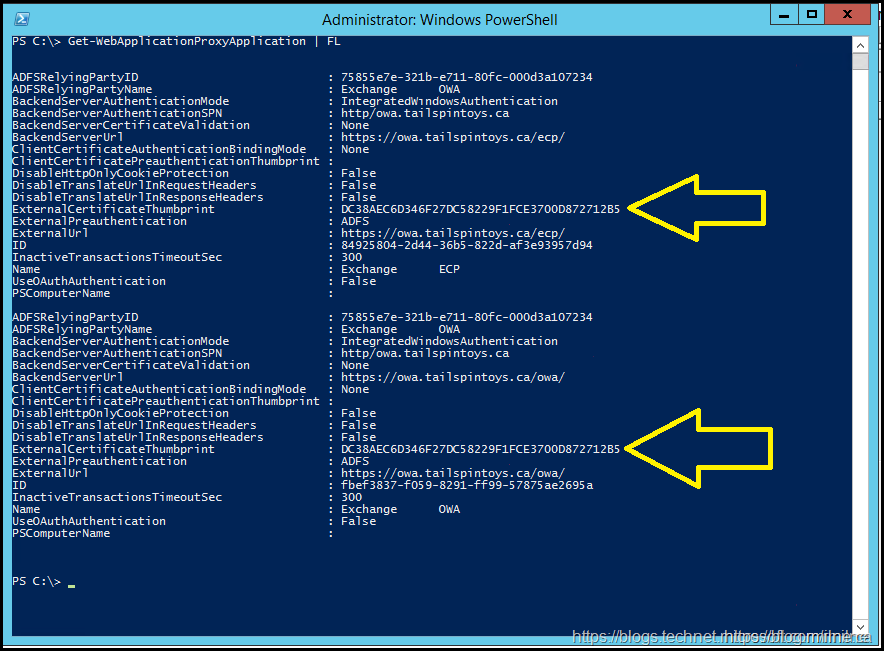
Set-WebApplicationProxyApplication -ID 84925804-2D44-36B5-822D-AF3E93957D94 -ExternalCertificateThumbprint DC38AEC6D346F27DC58229F1FCE3700D872712B5
Repeat this for all other required applications.
Updated values now present in the ExternalCertificateThumbprint entries. They are highlighted by the yellow arrows below.
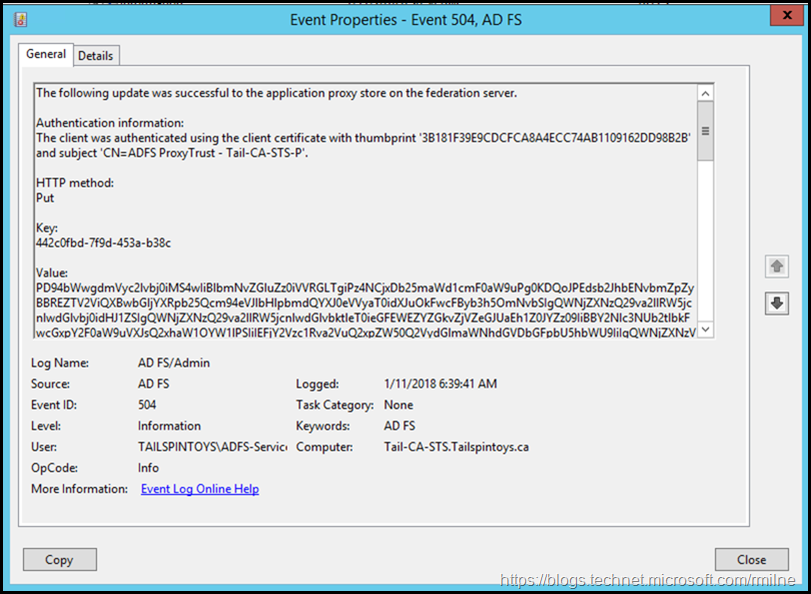
When the certificate binding was updated, EventID 504 was logged on AD FS farm.
To help with accessibility, the text from the image above is included below.
The following update was successful to the application proxy store on the federation server.
Authentication information:
The client was authenticated using the client certificate with thumbprint '3B181F39E9CDCFCA8A4ECC74AB1109162DD98B2B' and subject 'CN=ADFS ProxyTrust - Tail-CA-STS-P'.
Now that we have updated the published application, we can test and verify that we are back in business!
Cheers,
Rhoderick