When deploying AD FS and Web Application Proxy it is common to run into some networking issues. Normally this is due to firewall rules not being set correctly.
However we need to be aware of the default behaviour of WAP and factor that into our deployment.
When WAP is installed, it will write additional firewall rules into the Windows firewall. However, the default rules do not cover all monitoring eventualities.
As we discussed in Load Balancing Azure AD FS Services there is an option to monitor AD FS and WAP using HTTP on TCP 80. This will work out of the box on AD FS.
However you will need to adjust the WAP servers default Windows firewall configuration to allow the HTTP traffic. It is blocked by default.
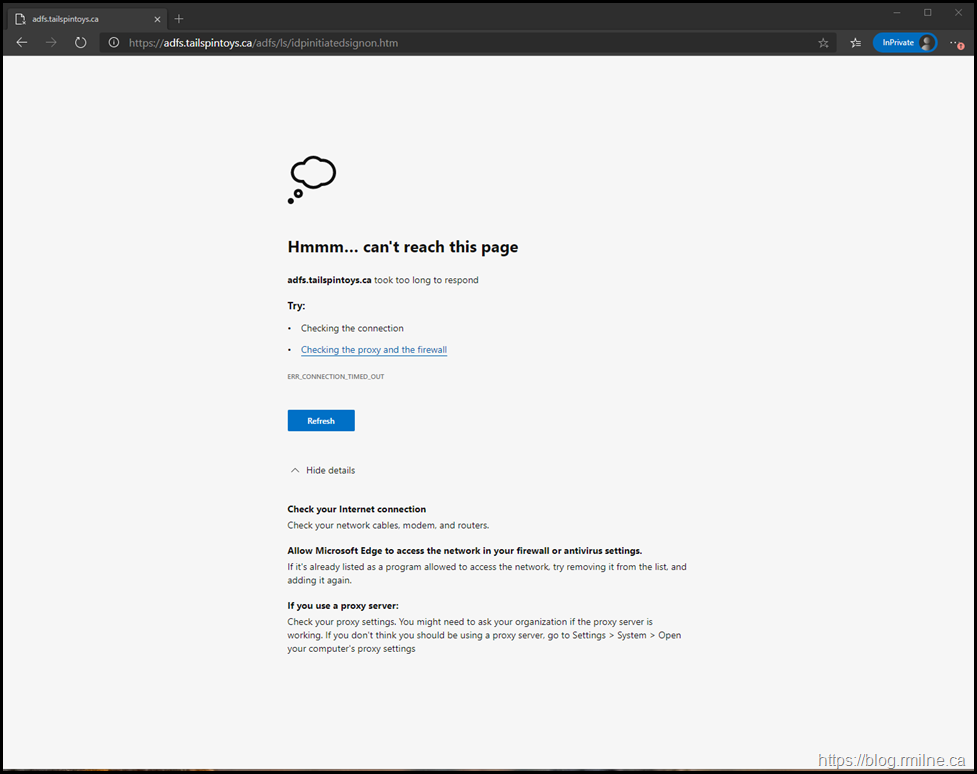
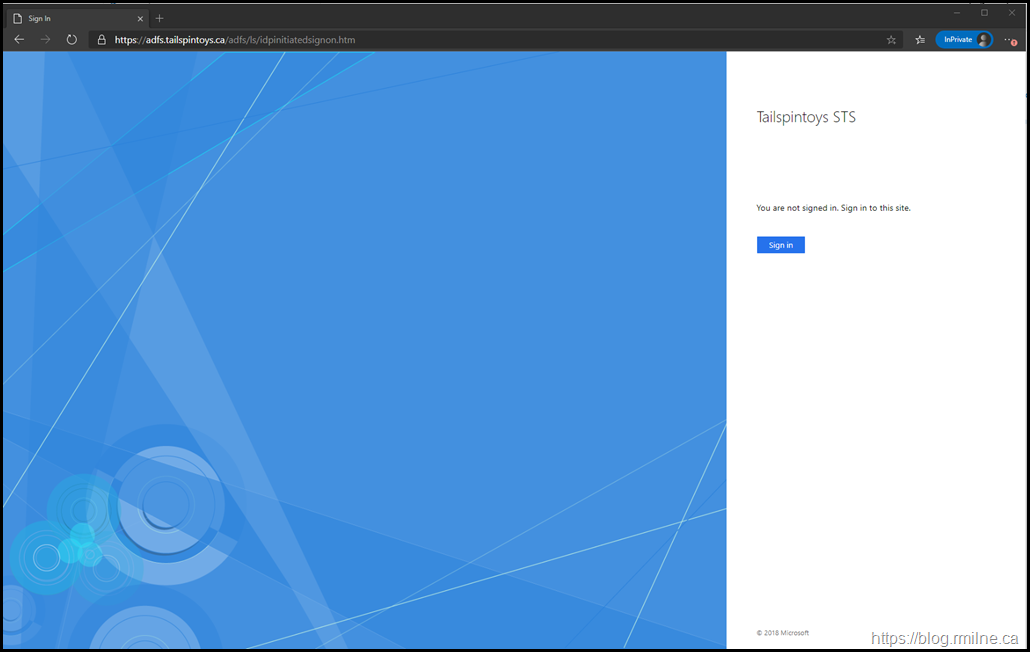
When deploying the new WAP server, it is likely that you will encounter the issue by seeing an error such as the screenshot below or have failing health monitors on the load balancer.
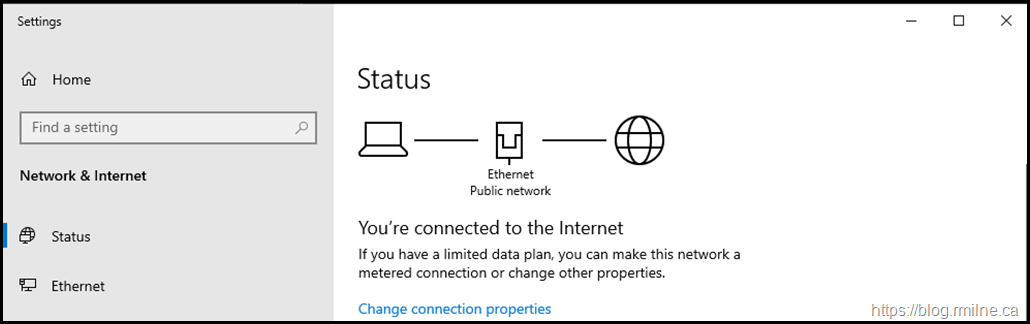
As is standard practice, the WAP servers are located in the DMZ and are not joined to the domain. Thus the Windows firewall will use the Public profile.
The reason that you cannot access WAP or a published application is potentially due to Windows Firewall blocking the traffic. Disabling Windows Firewall is not the correct defense in depth approach. Rather we need to verify the firewall profile in use, and what ACLs may need to be added.
This can be seen below on a Windows Server 2019 WAP, as the Ethernet network location is set to Public.
Reviewing Default WAP Firewall Rules
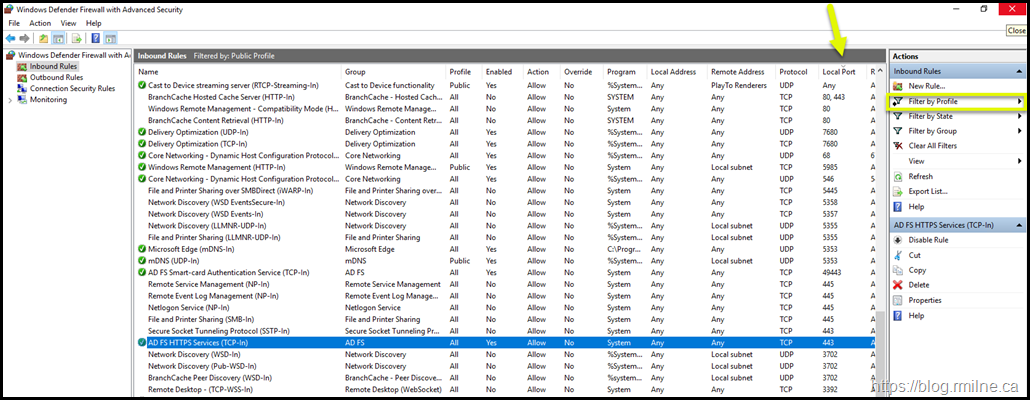
In the Windows Defender Firewall with Advanced Security from the same Windows Server 2019 machine, we have filtered by network profile. This is the highlighted option on the right hand side.
Then the Local Port column was used to sort the rules in ascending order. This allows us to easily see the rules that apply for TCP 80 and TCP 443.
You will note that there is no applicable WAP rule for TCP 80. There is only an "AD FS HTTPS Services (TCP-In)" rule for TCP 443.
Adding WAP Firewall Rule To Allow TCP 80 Monitors
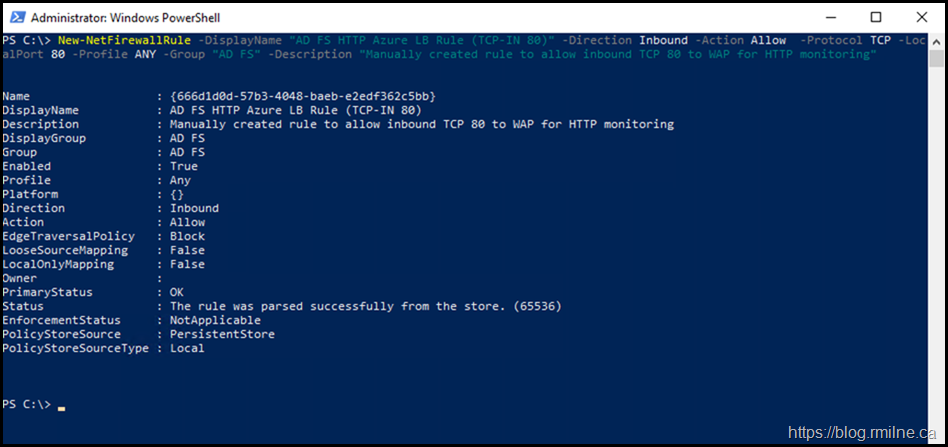
The below PowerShell oneliner will create a sample Firewall rule that will permit inbound TCP 80 traffic.
New-NetFirewallRule -DisplayName "AD FS HTTP Azure LB Rule (TCP-IN 80)" -Direction Inbound -Action Allow -Protocol TCP -LocalPort 80 -Profile ANY -Group "AD FS" -Description "Manually created rule to allow inbound TCP 80 to WAP for HTTP monitoring"
WAP Server Now Functional
Now that the health probes are allowed, the server is marked as healthy and is now accessible.
Rinse and repeat for the remaining WAP servers.
Cheers,
Rhoderick
I'm having almost the same issue but in my case my Proxy2 is letting me access the link.
do you have any knowledge on how to reconnect the WAP back to the ADFS server with this Load balancer not allowing traffic.
is there some sort of an exception that we have to do to get it to reconnect?
I would do a Wireshark trace on the proxy and AD FS server (if you can host file to one server to troubleshoot) else do a PCAP on the LB - it should be able to do that.
Cheers,
Rhoderick