There have been some recent feature additions to Azure AD Connect. If we look at the Azure AD Connection Version History after a brief hiatus, there are newer versions as of March 2021. At the time of witing, the latest version is 1.6.4.0 and was released on the 31st May 2021.
There are multiple new features and changes in this build.
-
Updated ADSyncTools PowerShell module
-
Defaults to V2 synchronisation endpoint
-
Updated sync rules for V2 Group Witeback
-
Selective Password Hash Sync
-
Single Object Sync cmdlet added for troubleshooting
-
Supports Hybrid Identity Administrator role
-
Updated AADConnectHealthAgent
Back Away From AD FS
In addition to the features noted above, there is a huge new feature to drive Password Hash Synchnonisation (PHS) and to move away from AD FS.
Staged Rollout is now generally available as of May 2021. For details and more information, please review the staged rollout interactive guide
There are many more resources to help with the move away from AD FS.
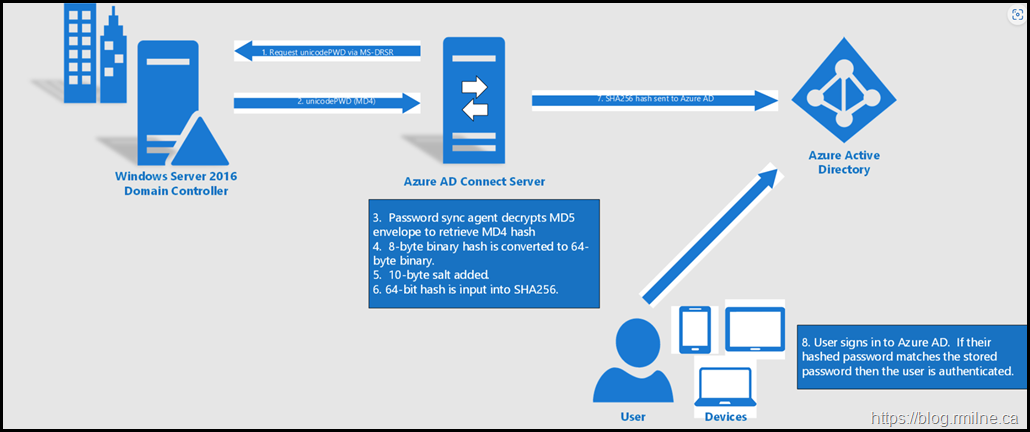
We can start an overview Password Hash Sync with Azure AD Connect and then walk through Tutorial Password Hash Sync
How PHS works lists the technical operation of the feature.
Selective Password Hash Synchronization Configuration
As noted at the start of this post, selective password hash sync is not a supported feature.
Please see:
Selective Password Hash Synchronization for Azure AD Connect | Microsoft Docs
By default, once it has been setup, password hash synchronization will occur on all of the users you are synchronizing.
If you'd like to have a subset of users excluded from synchronizing their password hash to Azure AD, you can configure selective password hash synchronization
To reduce the configuration administrative effort, you should first consider the number of user objects you wish to exclude from password hash synchronization. Verify which of the scenarios below, which are mutually exclusive, aligns with your requirements to select the right configuration option for you.
-
If the number of users to exclude is smaller than the number of users to include, follow the steps in this section.
-
If the number of users to exclude is greater than the number of users to include, follow the steps in this section.
Both scenarios rely on setting the adminDescription attribute of users to a specific value. This allows the rules to be applied and is what makes selective PHS work.
The adminDescription attribute can be set via:
-
Active Directory Users and Computers
-
Set-ADUser PowerShell cmdlet. For more information see Set-ADUser.
EnforceCloudPasswordPolicyForPasswordSyncedUsers
PHS authentication is performed against Azure AD. This feature is not applicable to federated domains since Azure does NOT authenticate users in the federated scenario, it is the federation provider which performs this task.
a user is in the scope of password hash synchronization, by default the cloud account password is set to Never Expire.
You can continue to sign in to your cloud services by using a synchronized password that is expired in your on-premises environment. Your cloud password is updated the next time you change the password in the on-premises environment.
If there are synchronized users that only interact with Azure AD integrated services and must also comply with a password expiration policy, you can force them to comply with your Azure AD password expiration policy by enabling the EnforceCloudPasswordPolicyForPasswordSyncedUsers feature.
It is recommended to enable EnforceCloudPasswordPolicyForPasswordSyncedUsers, prior to enabling password hash sync, so that the initial sync of password hashes does not add the DisablePasswordExpiration value to the PasswordPolicies attribute for the users.
The default Azure AD password policy requires users to change their passwords every 90 days. If your policy in AD is also 90 days, the two policies should match. However, if the AD policy is not 90 days, you can update the Azure AD password policy to match by using the Set-MsolPasswordPolicy PowerShell command.
Azure AD supports a separate password expiration policy per registered domain.
Caveat: If there are synchronized accounts that need to have non-expiring passwords in Azure AD, you must explicitly add the DisablePasswordExpiration value to the PasswordPolicies attribute of the user object in Azure AD. You can do this by running the following command.
ForcePasswordChangeOnLogOn
It is typical to force a user to change their password during their first logon, especially after an admin password reset occurs. It is commonly known as setting a "temporary" password and is completed by checking the "User must change password at next logon" flag on a user object in Active Directory (AD).
The temporary password functionality helps to ensure that the transfer of ownership of the credential is completed on first use, to minimize the duration of time in which more than one individual has knowledge of that credential.
To support temporary passwords in Azure AD for synchronized users, you can enable the ForcePasswordChangeOnLogOn feature, by running the following command on your Azure AD Connect server:
Set-ADSyncAADCompanyFeature -ForcePasswordChangeOnLogOn $true
Since users are authenticating to Azure, we need to provide a mechanism to to allow the password to be changed and also to write it back to on-premises AD.
This will be Self Service Password Reset (SSPR) coupled with Password writeback.
Account Expiration
Account expiration is not synchronised to Azure AD. This is the accountExpires attribute of the object.
As a result, expired accounts are still able to authenticate to Azure AD. To manage this behaviour, user accounts should be disabled on to block the sign in.
This can be an automated or manual process.
Cheers,
Rhoderick