In the Tailspintoys environment the AD FS Proxy was offline for month. It was unable to contact the AD FS server on the internal network, and this allowed the short lived authentication certificate to expire. At this point the AD FS Proxy was "dead to me" as far as the AD FS server was concerned. The internal AD FS server was OK, the issue was just with the proxy.
Bummer....
How do we fix this? Actually before we dive into that, lets see what was going on first. Please note that this post is for AD FS 2012 R2 onwards. It does not aim to cover AD FS 2.0 or 2.1 at all.
This is an updated post from the original one back in April 2015. The original will remain as it is still relevant, and some folks may have linked or bookmarked it.
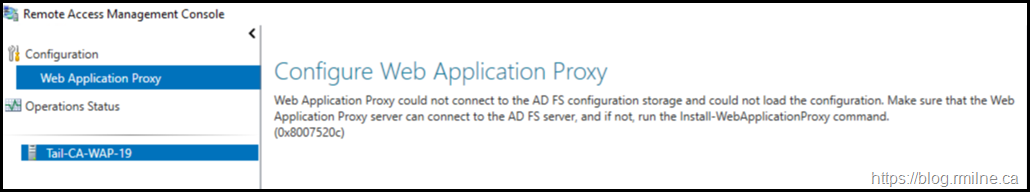
Starting Point – What The AD FS Proxy Saw In WAP Remote Management Console
On the WAP server, the Remote Access Management Console was not happy. It was reporting error code 0x8007520C.
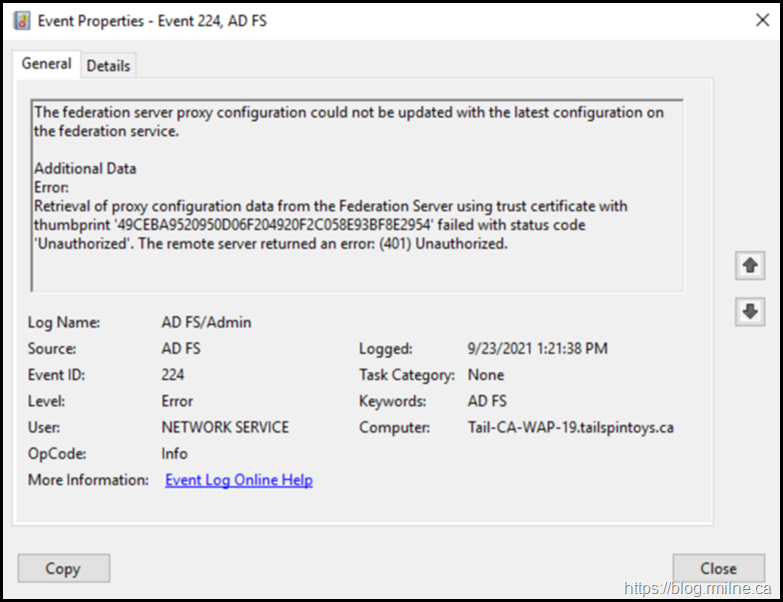
On the WAP server, EventID 244 was logged into the AD FS/Admin EventLog stating that it was unable to retrieve proxy configuration data from the Federation Service. The details in the event stated: System.Net.WebException: The remote server returned an error: (401) Unauthorized. This was EventID 422 as noted in the previous post.
There will also be errors present in the Microsoft-Windows-Web Application Proxy/Admin EventLog.
Starting Point – What AD FS Saw
On AD FS we can see what it really though about the AD FS proxy.
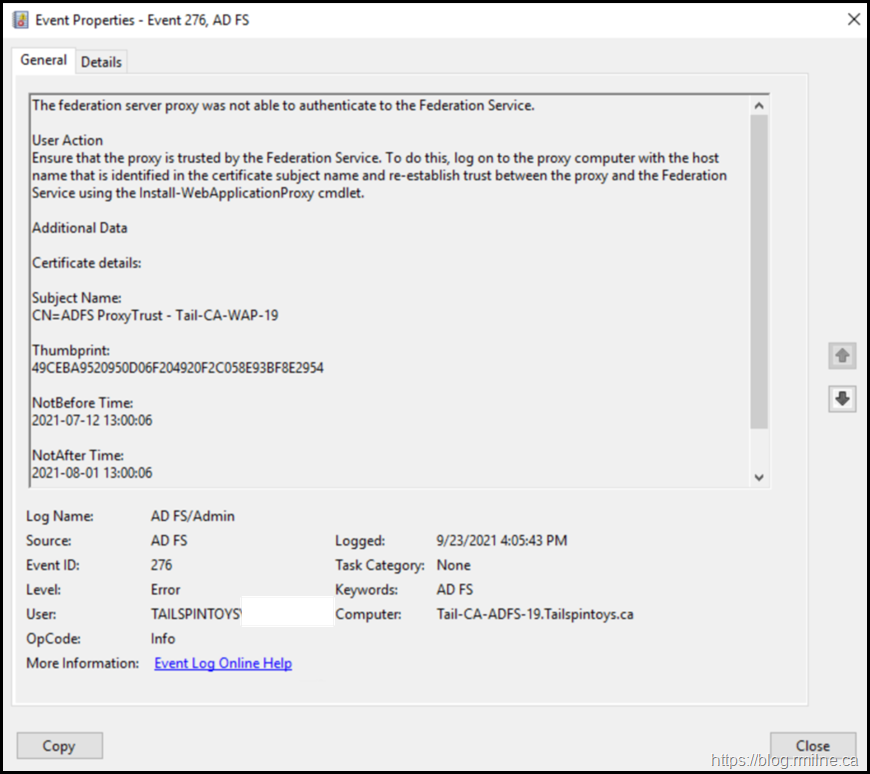
Since the federation server proxy could not renew its trust with the Federation Service, the recommended user action was: To ensure that the federation server proxy is trusted by the Federation Service. If the trust does not exist or has been revoked, establish a trust between the proxy and the Federation Service using the Federation Service Proxy Configuration Wizard by logging on to the proxy computer. This is detailed in EventID 276, which is again logged on the AD FS server.
The proxy trust certificate specified by thumpbrint has expired. Note that you can also see the calling IP listed at the bottom of the event message.
OK – so we need to re-establish the trust between the AD FS proxy and AD FS server. How do we go about doing that?
Re-Establish AD FS Proxy Trust Using Remote Access Management Console
Interestingly enough there is no option presented initially in the GUI to re-configure the AD FS proxy.
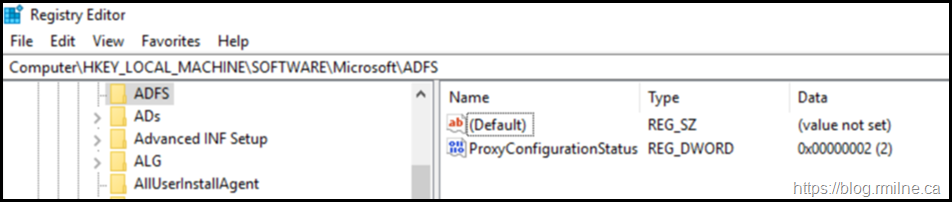
Currently it knows that the wizard was previously executed, and this fact is stored in the registry. As Georg discussed at MEC to allow the Remote Access GUI to re-run the wizard again, we need to edit the registry. The registry value that we need to change is:
HKLM\Software\Microsoft\ADFS\ProxyConfigurationStatus
We need to set the ProxyConfigurationStatus REG_DWORD to a value of 1 (meaning “not configured”) instead of 2 (“configured”). Once that change is made, re-open the GUI. No reboot is required.
After changing the ProxyConfigurationStatus to a value of 1, the Remote Access Manager should now allow you to re-run the configuration wizard.
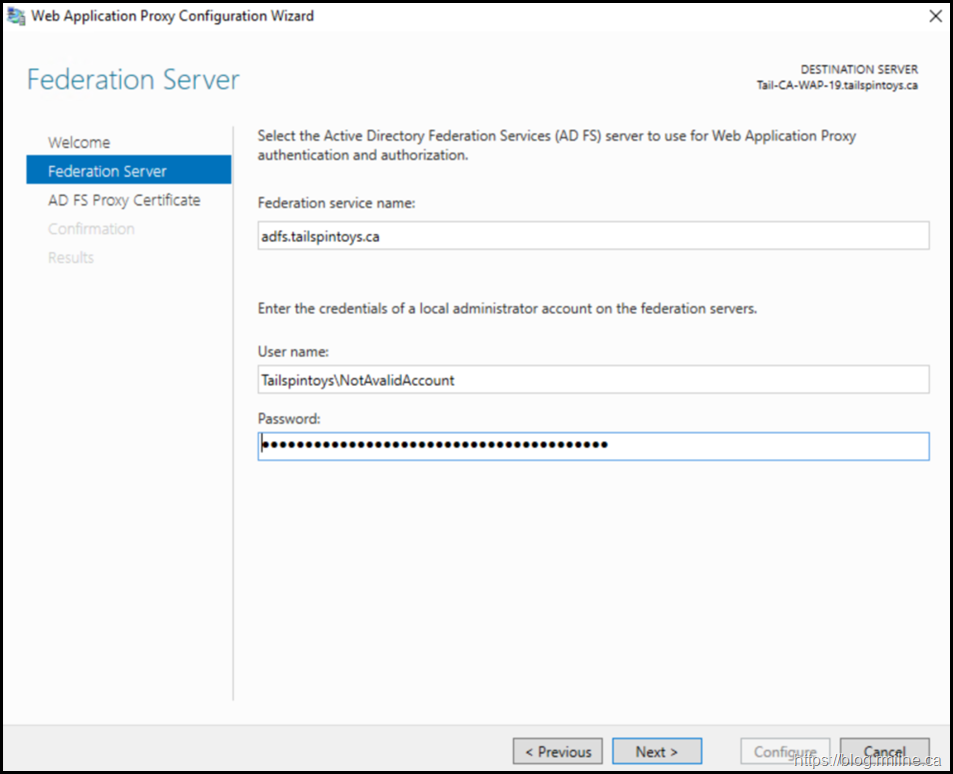
For full details on this process, please see this post. As a brief recap, we need to ensure that the federation service name is the AD FS endpoint that we defined when initially building the environment.
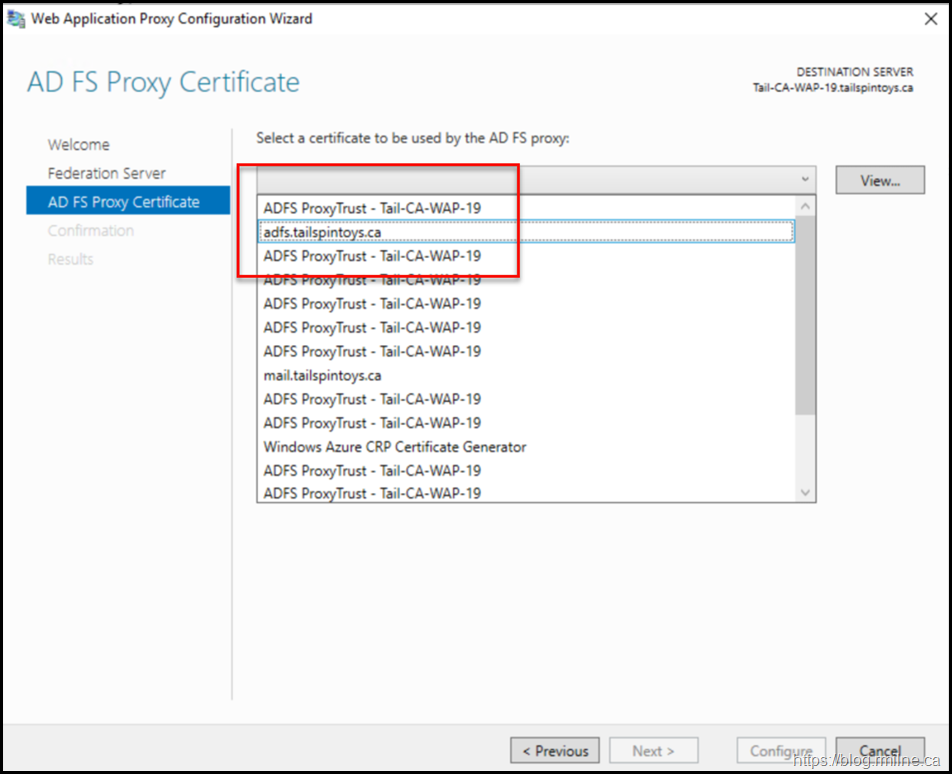
Since there may have been certificate replacement/renewal since the initial server was deployed, be careful to select the correct certificate:
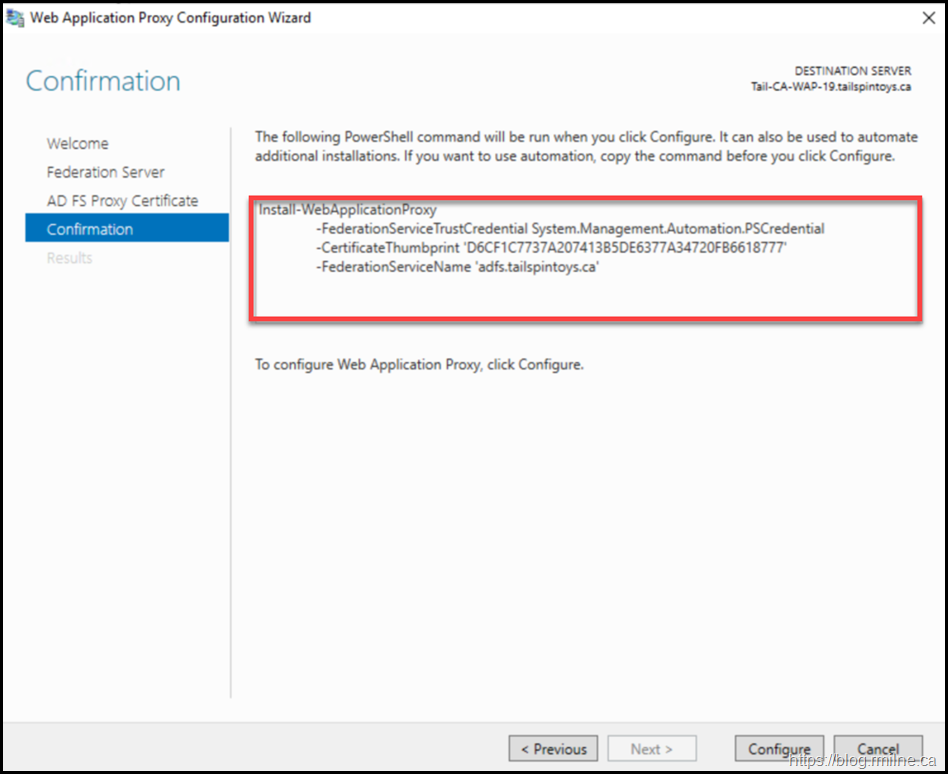
The summary screen indicates the PowerShell code that will be executed. This is also captured later in the post for reference.
And when complete, the trust is now re-established.
Now restart the AD FS service on the Proxy server, and check the AD FS event logs to ensure that they are all green ticky ticky!
Alternatively, this can be done from PowerShell, this is shown below. Typically this is what I normally use as it is faster, and does not require the registry modification.
Re-Establish AD FS Proxy Trust Using PowerShell
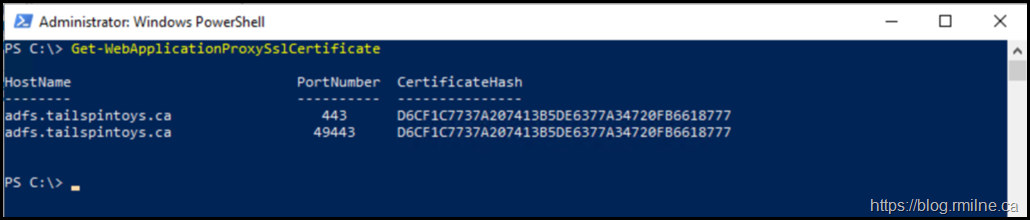
EventID 276 shown above, notes that we can run the Install-WebApplicationProxy cmdlet to re-establish trust between the AD FS server and the WAP. Docs discusses this in the Install and Configure the Web Application Proxy Server section. The certificate we want to use is already installed onto the server. In my case it has the thumbprint of D6CF1C7737A207413B5DE6377A34720FB6618777– note that yours *WILL* be different. To obtain your certificate thumbprint you can look at the certificate MMC or alternatively run:
Get-WebApplicationProxySslCertificate
In this lab, the command executed was:
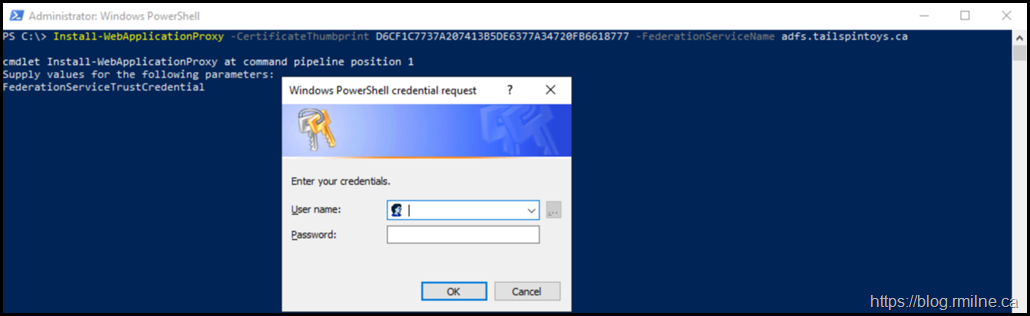
Install-WebApplicationProxy –CertificateThumbprint D6CF1C7737A207413B5DE6377A34720FB6618777 -FederationServiceName adfs.tailspintoys.ca
Note that the username and password were not specified, since the cmdlet knows it needs an account that has permission on the AD FS server and it prompts for this required information. This is the Tailspintoys administrator account as shown below:
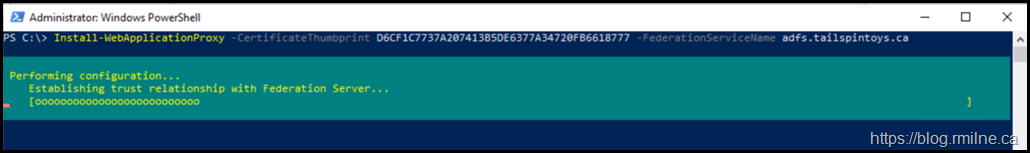
After providing the credentials, the cmdlet does it’s thang:
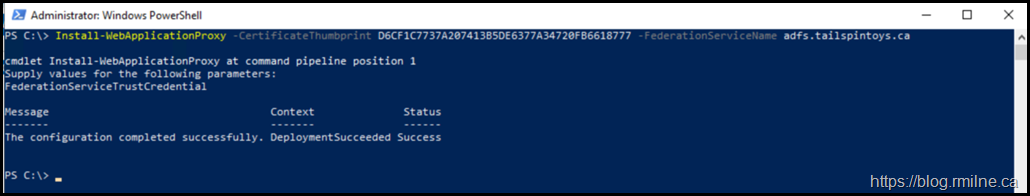
Finally finishing up with a Deployment Succeeded message.
Checking For Success
After the restarting the AD FS service on the proxy, success messages were then logged on both the AD FS server and the proxy.
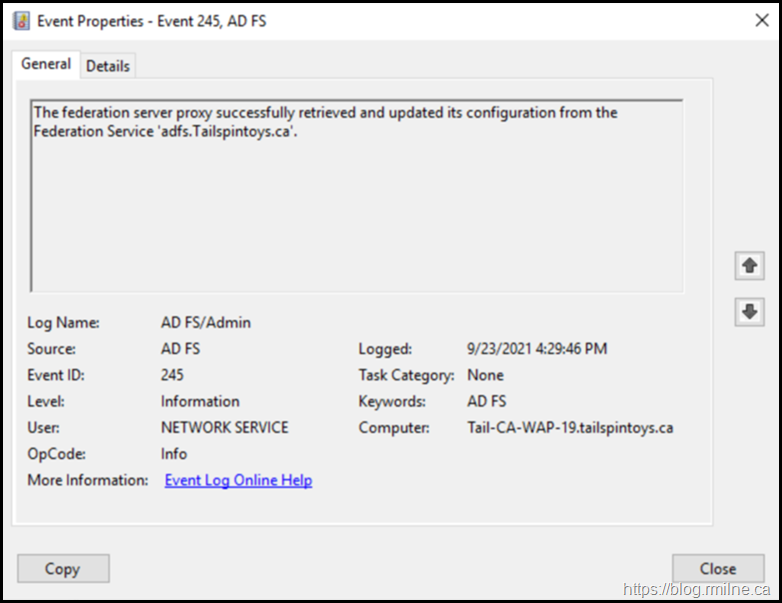
On the AD FS proxy EventID 245 noted that the proxy was able to successfully retrieve its configuration:
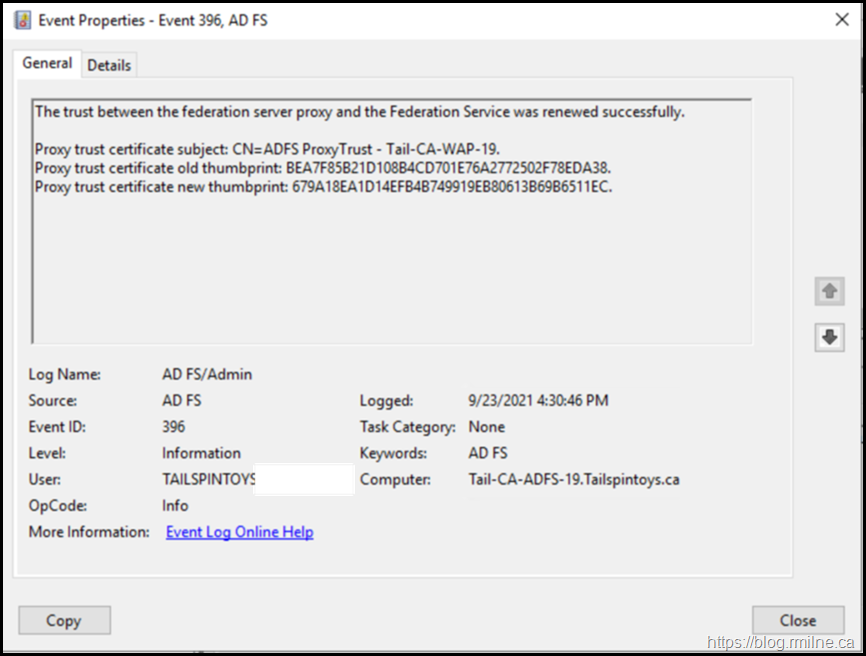
And on the AD FS server EventID 396 was logged stating that the trust between the proxy and AD FS server was renewed.
Clients were now able to successfully authenticate through the AD FS proxy from the Internet.
Good job. Time to go home for tea and medals!
Cheers,
Rhoderick

I'd love to get you thoughts on this. I have tried to resestablish trust on my ADFS proxy but no matter what I do it times out and gives me an error that it is Unable to retrieve proxy configuration data from the Federation Service. I've tried both the GUI and Powershell options on your blog and still cannot get it to work.
Any ideas you can share?
Thank you
Jeremy Leigh
Hi Jeremy,
Ensure that the TLS settings on both the AD FS farm and WAP are aligned. Seen that a few times lately after hardening was done only on one side.
The same is also true if you have a load balancer in front that has its own separate TLS configuration, make sure the network team have done the necessary there.
If the LB is present, can you bypass via hosts file direct to AD FS?
Trace out the packets using Wireshark to see whats happening on the wire.
Cheers,
Rhoderick
For mi not work:
Install-WebApplicationProxy : An error occurred when attempting to establish a trust relationship with the federation
service. Error: Unable to connect to the remote server
At line:1 char:1
+ Install-WebApplicationProxy -CertificateThumbprint ' ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Install-WebApplicationProxy], ProxyTrustException
+ FullyQualifiedErrorId : DeploymentTask,Microsoft.IdentityServer.Management.Proxy.Commands.InstallProxyCommand
That sounds more like a network connectivity issue, or your TLS settings are not aligned.
Check and verify that first please.
Cheers,
Rhoderick
Such a good article! Kudos
I'm running into the same thing. I have two ADFS servers internally and Two WAP servers. I have an AWS NLB doing UDP/TCP 443 in front of the Internal ADFS and WAP servers.
When I installed the 2nd WAP server I get errors
"The federation server proxy configuration could not be updated with the latest configuration on the federation service." But it worked a few minutes prior. because it logged
"The trust between the federation server proxy and the Federation Service was renewed successfully. "
The MS Docs aren't very clear about adding additional WAP servers with a load balancer. I get that they use the proxy trust cert but it seems like both WAP servers want to use their own Proxy Trust cert??
After just a few minutes of installing the 2nd wap I'm getting errors every minute now on Both WAP server
The federation server proxy configuration could not be updated with the latest configuration on the federation service.
Additional Data
Error:
Retrieval of proxy configuration data from the Federation Server using trust certificate with thumbprint 'Removed Thumbprint' failed with status code 'ServiceUnavailable'. The remote server returned an error: (503) Server Unavailable.
Any thoughts?
update..
So the above error was partially my fault. I was trying to simulate external traffic by messing with the host files on the WAP servers. This messed up communication with the back end NLB for ADFS. I"M a dummy
once I fixed that, the 2nd WAP server was still having issues though
"The federation server proxy configuration could not be updated with the latest configuration on the federation service. "
Additional Data
Error:
Retrieval of proxy configuration data from the Federation Server using trust certificate with thumbprint '' failed with status code 'Unauthorized'. The remote server returned an error: (401) Unauthorized.
I ran the command get on the working WAP server
Get-WebApplicationProxySslCertificate to get the thumbprint
then ran this is on the non working WAP server
Install-WebApplicationProxy –CertificateThumbprint -FederationServiceName fs.myadfs.com
I entered a local admin account from the ADFS server and after a few minutes it was successful.
live saver!
thanks mate
Hi, appreciate the tutorial. I tought it was an error from Token-decrypting and Token-signing error but this happens on adfs not wap. Anyway those steps save me a lot of time. Thanks a lot sir (from France).